[ad_1]

A Russian hacking group tracked as TA473, aka ‘Winter Vivern,’ has been actively exploiting vulnerabilities in unpatched Zimbra endpoints since February 2023 to steal the emails of NATO officers, governments, army personnel, and diplomats.
Two weeks in the past, Sentinel Labs reported on a latest operation by ‘Winter Vivern’ utilizing websites mimicking European businesses preventing cybercrime to unfold malware that pretends to be a virus scanner.
In the present day, Proofpoint has printed a brand new report on how the risk actor exploits CVE-2022-27926 on Zimbra Collaboration servers to entry the communications of NATO-aligned organizations and individuals.
Concentrating on Zimbra
Winter Vivern assaults start with the risk actor scanning for unpatched webmail platforms utilizing the Acunetix device vulnerability scanner.
Subsequent, the hackers ship a phishing e mail from a compromised handle, which is spoofed to look as somebody the goal is accustomed to or is in some way related to their group.
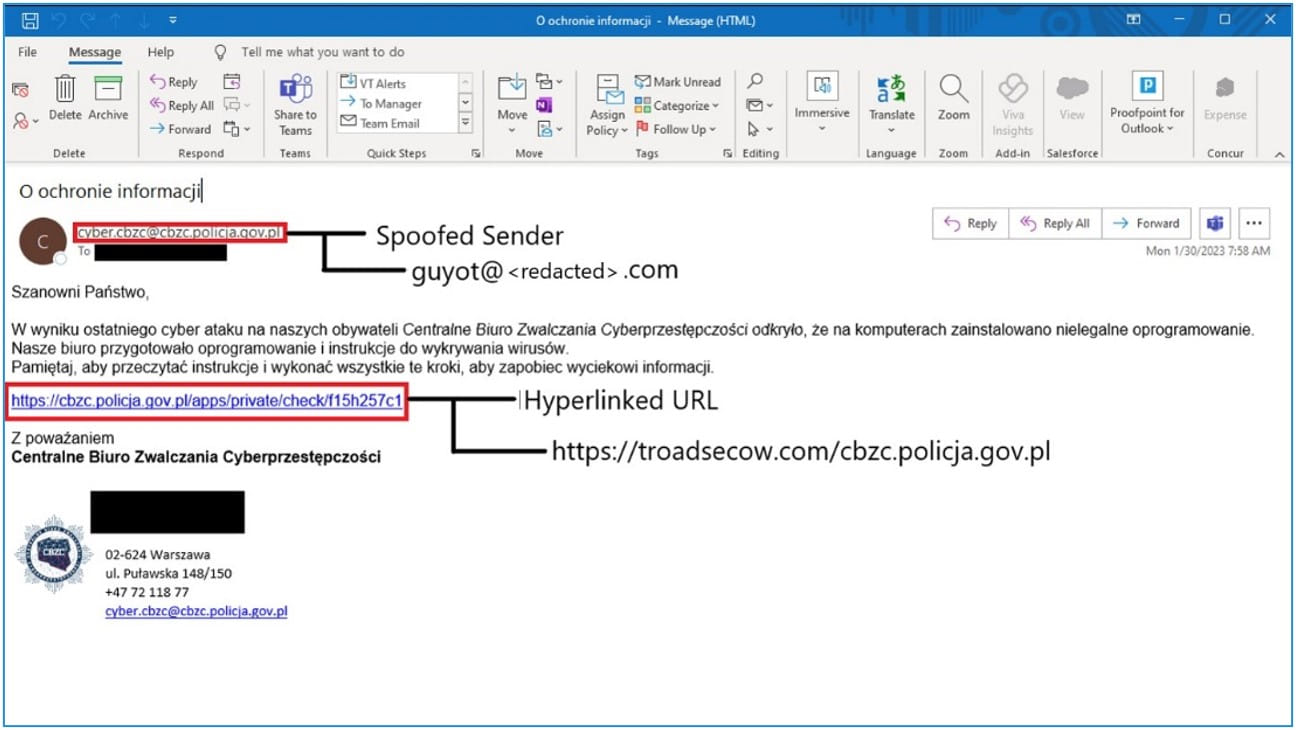
The emails comprise a hyperlink that exploits the CVE-2022-27926 within the goal’s compromised Zimbra infrastructure to inject different JavaScript payloads into the webpage.
These payloads are then used to to steal usernames, passwords, and tokens from cookies obtained from the compromised Zimbra endpoint. This data permits the risk actors to entry the targets’ e mail accounts freely.
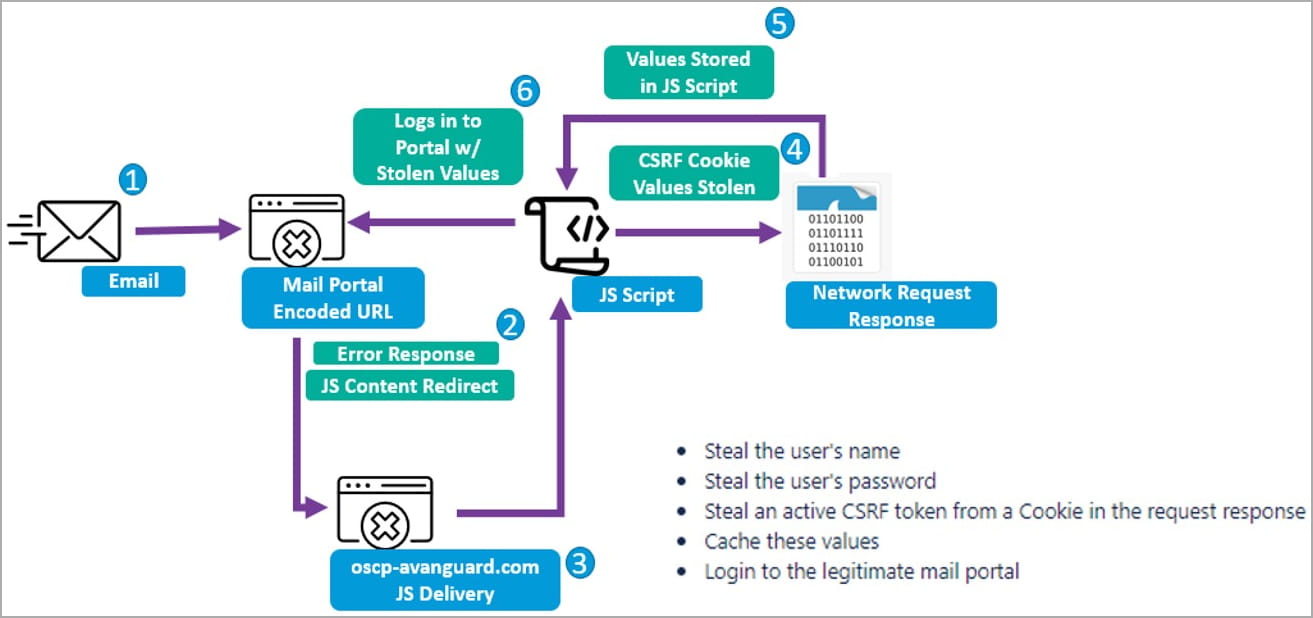
“These CSRF JavaScript code blocks are executed by the server that hosts a weak webmail occasion,” explains Proofpoint within the reported
“Additional, this JavaScript replicates and depends on emulating the JavaScript of the native webmail portal to return key net request particulars that point out the username, password, and CSRF token of targets.”
“In some situations, researchers noticed TA473 particularly focusing on RoundCube webmail request tokens as effectively.”
This element demonstrates the diligence of the risk actors in pre-attack reconnaissance, determining which portal their goal makes use of earlier than crafting the phishing emails and setting the touchdown web page operate.
Aside from the three layers of base64 obfuscation utilized on the malicious JavaScript to make evaluation extra sophisticated, ‘Winter Vivern’ additionally included elements of the professional JavaScript that runs in a local webmail portal, mixing with regular operations and lowering the chance of detection.
Lastly, the risk actors can entry delicate data on the compromised webmails or keep their maintain to observe communications over a time frame. Moreover, the hackers can use the breached accounts to hold out lateral phishing assaults and additional their infiltration of the goal organizations.
Regardless of researchers stating that ‘Winter Vivern’ isn’t significantly subtle, they comply with an efficient operational method that works even in opposition to high-profile targets who fail to use software program patches shortly sufficient.
On this case, CVE-2022-27926 was mounted in Zimbra Collaboration 9.0.0 P24, launched in April 2022.
Contemplating that the earliest assaults have been noticed in February 2023, the delay in making use of the safety replace is measured to at the very least ten months.
[ad_2]