[ad_1]

A surge of trojanized Tor Browser installers targets Russians and Japanese Europeans with clipboard-hijacking malware that steals contaminated customers’ cryptocurrency transactions.
Kaspersky analysts warn that whereas this assault isn’t new or notably artistic, it is nonetheless efficient and prevalent, infecting many customers worldwide.
Whereas these malicious Tor installers goal nations worldwide, Kaspersky says that the majority are concentrating on Russia and Japanese Europe.
“We relate this to the ban of Tor Venture’s web site in Russia on the finish of 2021, which was reported by the Tor Venture itself,” explains Kaspersky.
“Based on the latter, Russia was the second largest nation by variety of Tor customers in 2021 (with over 300,000 every day customers, or 15% of all Tor customers).”
Malicious Tor Browser installers
Tor Browser is a specialised internet browser that enables customers to browse the net anonymously by hiding their IP handle and encrypting their site visitors.
Tor may additionally be used for accessing particular onion domains, in any other case often known as the “darkish internet,” which aren’t listed by normal serps or accessible via common browsers.
Cryptocurrency holders could use the Tor browser both to reinforce their privateness and anonymity whereas transacting with cryptocurrencies or as a result of they wish to entry unlawful darkish internet market providers, that are paid in crypto.
Trojanized Tor installations are sometimes promoted as “security-strengthened” variations of the official vendor, Tor Venture, or pushed to customers in nations the place Tor is prohibited, making it more durable to obtain the official model.
Kaspersky says that these installers comprise an ordinary model of the Tor browser, albeit outdated normally, together with an additional executable hidden inside a password-protected RAR archive set to self-extract on the consumer’s system.
The installers are additionally localized with names like ‘torbrowser_ru.exe,’ and comprise language packs permitting customers to pick their most popular language.
Supply: Kaspersky
Whereas the usual Tor browser is launched within the foreground, the archive extracts the malware within the background and runs it as a brand new course of whereas additionally registering it on the system autostart. Moreover, the malware makes use of a uTorrent icon to cover on the breached system.
.jpg)
Supply: Kaspersky
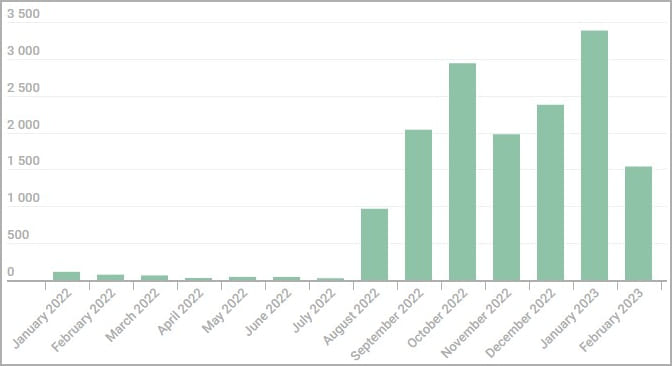
Kaspersky has detected 16,000 variants of those Tor installers between August 2022 and February 2023 in 52 nations, primarily based on knowledge from customers of its safety merchandise.
Whereas the bulk are concentrating on Russia and Japanese Europe, they’ve additionally been seen concentrating on the US, Germany, China, France, the Netherlands, and the UK.
Supply: Kaspersky
Clipboard hijacking
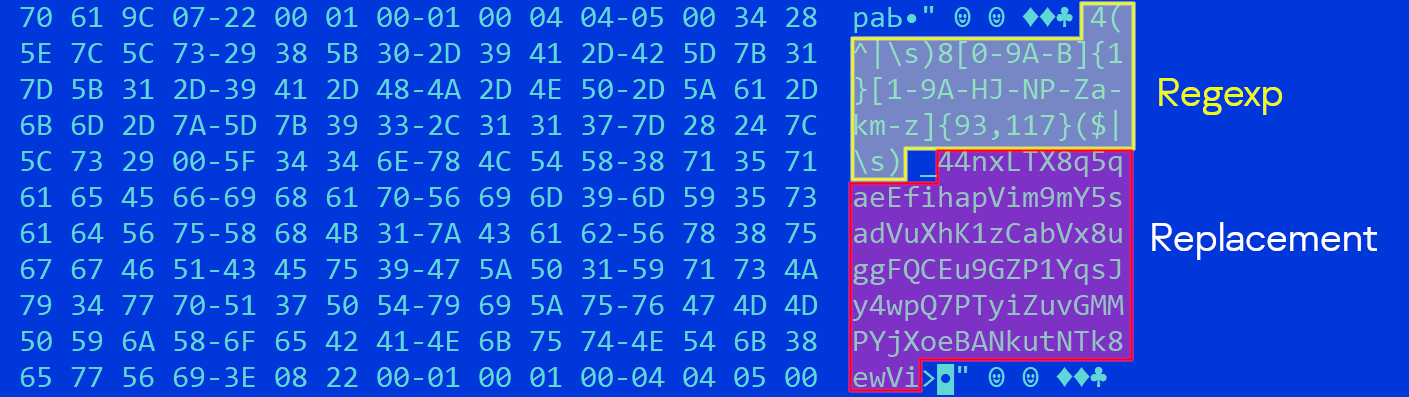
As cryptocurrency addresses are lengthy and sophisticated to kind, it is not uncommon to repeat them first to the clipboard after which paste them into one other program or web site.
The malware displays the clipboard for recognizable crypto pockets addresses utilizing common expressions, and when one is detected, replaces it with an related cryptocurrency handle owned by the menace actors.
When the consumer pastes the cryptocurrency handle, the menace actor’s handle can be pasted as an alternative, permitting the attackers to steal the despatched transaction.
Supply: Kaspersky
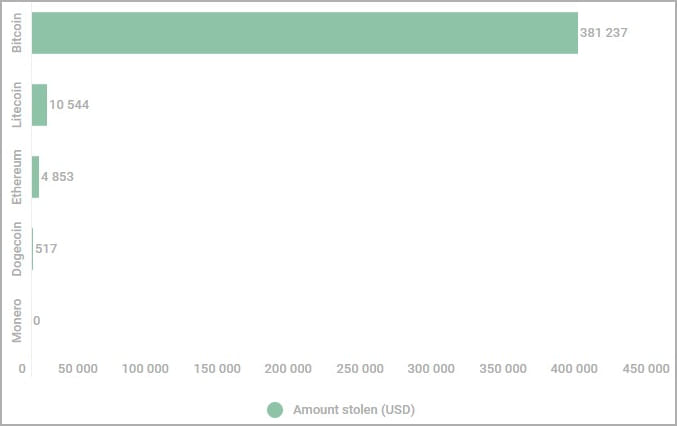
Kaspersky says the menace actor makes use of hundreds of addresses on every malware pattern, chosen randomly from a hardcoded record. This makes pockets monitoring, reporting, and banning arduous.
The cybersecurity firm unpacked a whole bunch of malware samples it had collected to extract the substitute addresses and located that they stole nearly $400,000, excluding Monero, which can’t be traced.
Supply: Kaspersky
That is the cash stolen solely from a single marketing campaign operated by a selected malware writer, and there are nearly definitely different campaigns utilizing trojanized installers for various software program.
To remain secure from clipboard hijackers, solely set up software program from reliable/official sources, on this case, the Tor Venture web site.
A easy check to verify if a clipper has contaminated you is to repeat and paste this handle to your Notepad: bc1heymalwarehowaboutyoureplacethisaddress.
Whether it is modified, it means your system is compromised.
[ad_2]