[ad_1]

The RIG Exploit Equipment is present process its most profitable interval, trying roughly 2,000 intrusions each day and succeeding in about 30% of circumstances, the very best ratio within the service’s lengthy operational historical past.
By exploiting comparatively previous Web Explorer vulnerabilities, RIG EK has been seen distributing numerous malware households, together with Dridex, SmokeLoader, and RaccoonStealer.
In line with an in depth report by Prodaft, whose researchers gained entry to the service’s backend internet panel, the exploit package stays a big large-scale risk to people and organizations.
RIG EK’s sordid historical past
RIG EK was first launched eight years in the past, in 2014, and promoted as an “exploit-as-a-service” rented to different malware operators to unfold their malware on susceptible gadgets.
The RIG exploit package is a set of malicious JavaScript scripts embedded in compromised or malicious web sites by the risk actors, that are then promoted by malvertising.
When a consumer visits these websites, the malicious scripts shall be executed and try to use numerous vulnerabilities within the browser to put in malware on the system routinely.
In 2015, the package’s authors launched the second main model of the package, laying the bottom for extra in depth and profitable operations.
In 2017 although, RIG suffered a big blow following a coordinated takedown motion that worn out giant elements of its infrastructure, severely disrupting its operations.
In 2019, RIG returned, this time specializing in ransomware distribution, serving to Sodinokibi (REvil), Nemty, and ERIS ransomware, compromise organizations with data-encrypting payloads.
In 2021, RIG’s proprietor introduced the service would shut down; nevertheless, RIG 2.0 returned in 2022 with two new exploits (CVE-2020-0674 and CVE-2021-26411 in Web Explorer), reaching an all-time excessive profitable breach ratio.
In April 2022, Bitdefender reported that RIG was getting used to drop the Redline information-stealer malware onto victims.
Whereas lots of the exploits focused by RIG EK are for Web Explorer, which Microsoft Edge has lengthy changed, the browser remains to be utilized by thousands and thousands of Enterprise gadgets, that are a major goal.
Present assault volumes
Prodaft says RIG EK at present targets 207 international locations, launching a median of two,000 assaults per day and having a present success fee of 30%. This fee was 22% earlier than the exploit package resurfaced with two new exploits, says Prodaft.
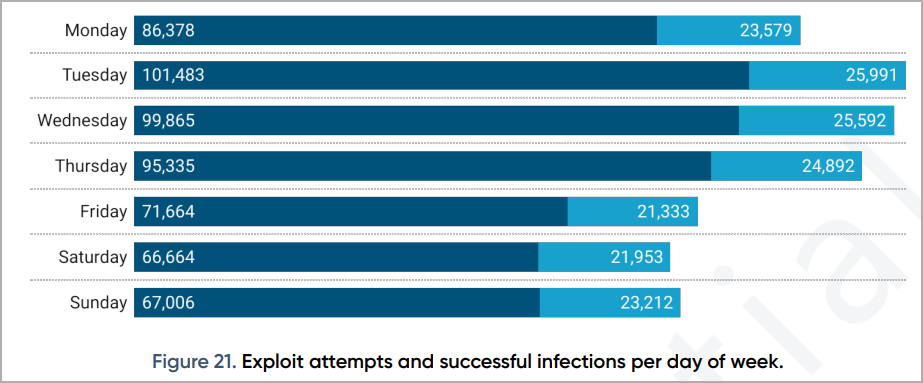
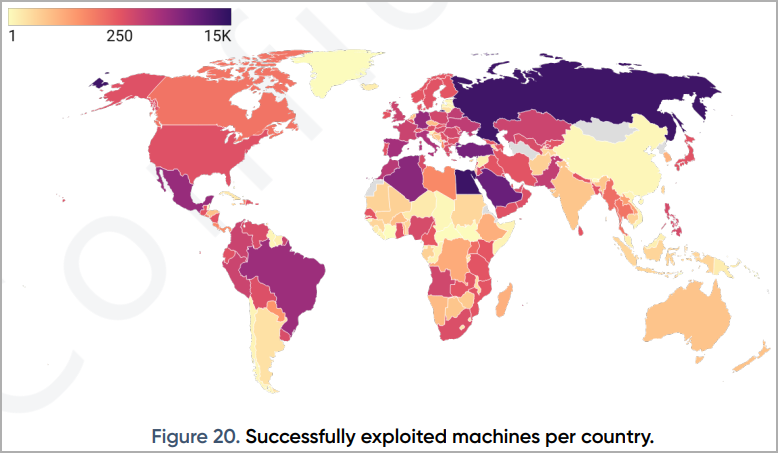
Because the heatmap revealed within the report exhibits, essentially the most impacted international locations are Germany, Italy, France, Russia, Turkey, Saudi Arabia, Egypt, Algeria, Mexico, and Brazil. Nonetheless, there are victims worldwide.
The very best success fee is introduced by CVE-2021-26411, attaining a forty five% profitable exploitation ratio, adopted by CVE-2016-0189 with 29% and CVE-2019-0752 with 10%.
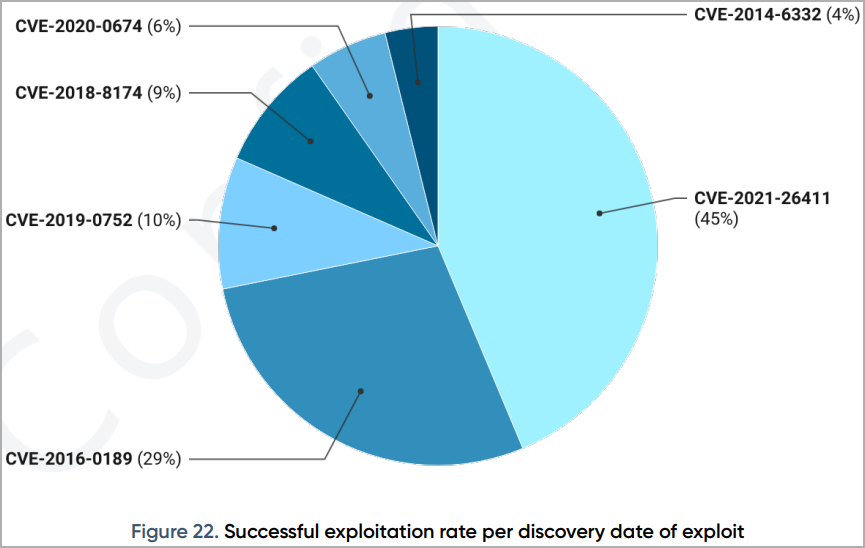
CVE-2021-26411 is a high-severity reminiscence corruption flaw in Web Explorer that Microsoft mounted in March 2021, triggered by viewing a maliciously crafted web site.
The CVE-2016-0189 and CVE-2019-0752 vulnerabilities are additionally in Web Explorer, permitting distant code execution within the browser.
CISA revealed an energetic exploitation alert for CVE-2019-0752 in February 2022, warning system directors the vulnerability remains to be being exploited and to use out there safety updates.
A wide range of malicious payloads
At present, RIG EK primarily pushes information-stealing and preliminary entry malware, with Dridex being the most typical (34%), adopted by SmokeLoader (26%), RaccoonStealer (20%), Zloader (2.5%), Truebot (1.8%), and IcedID (1.4%).
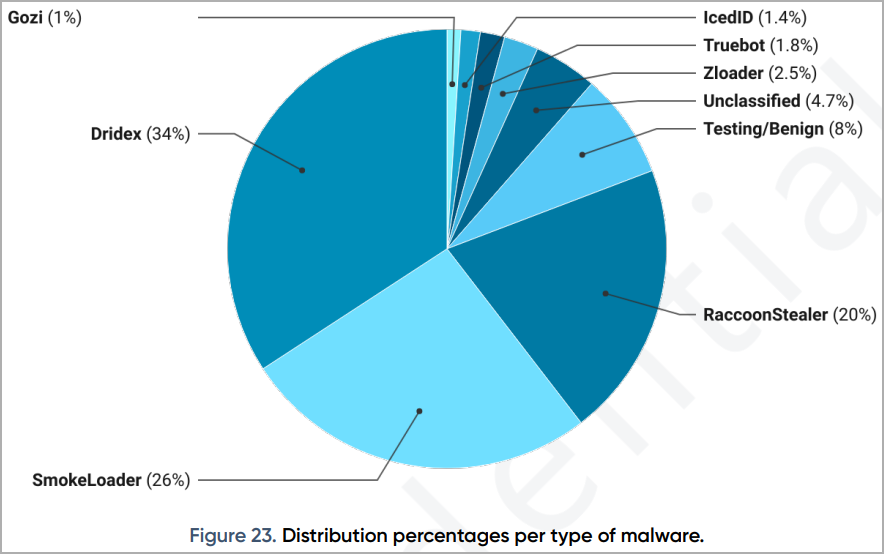
After all, the forms of malware unfold by RIG EK continuously change relying on which cybercriminals select to make use of the service.
Prodaft has beforehand additionally noticed the distribution of Redline, RecordBreaker, PureCrypter, Gozi, Royal Ransomware, and UrSnif.
Distributing the Dridex banking trojan is especially attention-grabbing as a result of there are indicators that the RIG operators have taken motion to make sure its distribution is problem-free.
“The RIG administrator had taken extra handbook configuration steps to make sure that the malware was distributed easily,” explains Prodaft within the report.
“Contemplating all these info, we assess with excessive confidence that the developer of Dridex malware has an in depth relationship with the RIG’s admins.”
It ought to be famous that Dridex was linked to Entropy ransomware assaults a yr in the past, so RIG EK breaches might result in data-encryption incidents.
The RIG EK stays a big risk to people and organizations utilizing outdated software program, threatening to contaminate their methods with stealthy info stealers that may siphon highly-sensitive information.
Nonetheless, RIG EK’s concentrate on Web Explorer could trigger the service to develop into quickly out of date as Microsoft lastly retired Web Explorer in February 2023, redirecting customers to Microsoft Edge.
[ad_2]