[ad_1]

Safety researchers have found a brand new backdoor known as WhiskerSpy used in a marketing campaign from a comparatively new superior menace actor tracked as Earth Kitsune, recognized for concentrating on people exhibiting an curiosity in North Korea.
The actor used a tried and examined methodology and picked victims from guests to a professional North Korea web site, a tactic referred to as a watering gap assault.
The brand new operation was found on the finish of final 12 months by researchers at cybersecurity firm Development Micro, who’ve been monitoring Earth Kitsune exercise since 2019.
Watering gap assault
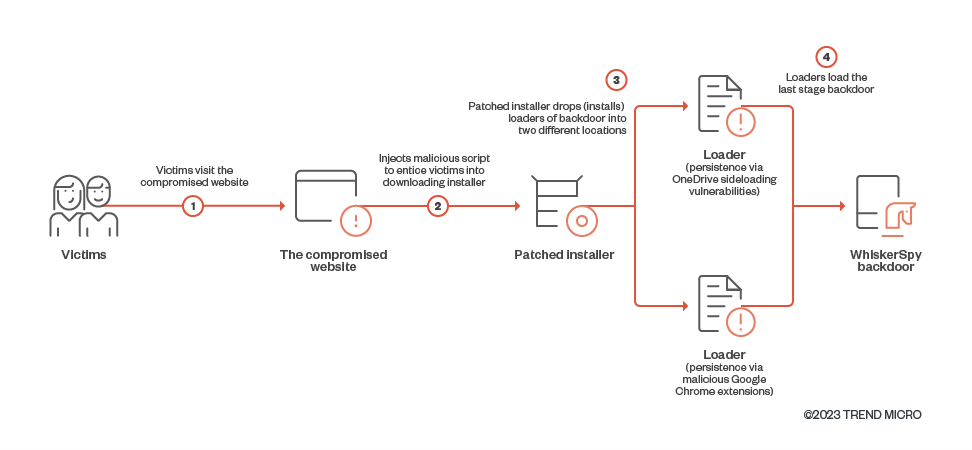
In keeping with Development Micro, WhiskerSpy was delivered when guests tried to look at movies on the web site. The attacker compromised the web site and injected a malicious script that requested the sufferer to put in a video codec for the media to run.
To keep away from suspicions, the menace actor modified a legit codec installer in order that it in the end loaded “a beforehand unseen backdoor” on the sufferer’s system.
supply: Trrend Micro
The researchers say that the menace actor focused solely guests to the web site with IP addresses from Shenyang, China; Nagoya, Japan; and Brazil.
It’s seemingly that Brazil was used just for testing the watering gap assault utilizing a VPN connection and the true targets had been guests from the 2 cities in China and Japan. Related victims could be served the faux error message beneath that prompts them to put in a codec to look at the video.
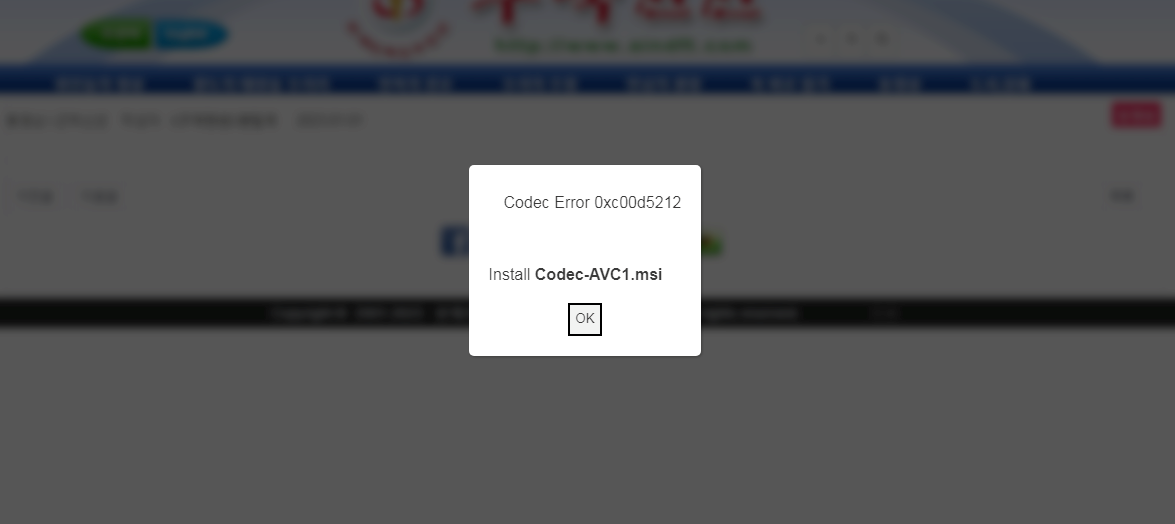
In actuality, the codec is an MSI executable that installs on the sufferer’s pc shellcode that triggers a sequence PowerShell instructions that result in deploying the WhiskerSpy backdoor.
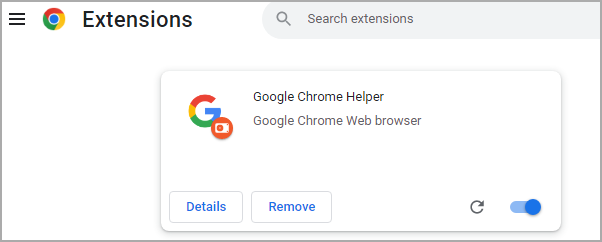
The researchers observe that one persistence method that Earth Kitsune used on this marketing campaign abuses the native messaging host in Google Chrome and installs a malicious Google Chrome extension known as Google Chrome Helper.
The function of the extension is to permit execution of the payload each time the browser begins.
The opposite methodology to realize persistence is by leveraging OneDrive side-loading vulnerabilities that permit dropping a malicious file (faux “vcruntime140.dll”) within the OneDrive listing.
WhiskerSpy particulars
WhiskerSpy is the primary payload used within the newest ‘Earth Kitsune’ marketing campaign, giving distant operators the next capabilities:
- interactive shell
- obtain file
- add file
- delete file
- record information
- take screenshot
- load executable and name its export
- inject shellcode right into a course of
The backdoor communicates with the command and management (C2) server utilizing a 16-byte AES key for encryption.
WhiskerSpy periodically connects to the C2 for updates about its standing and the server could reply with directions for the malware, akin to execute shell instructions, inject code to a different course of, exfiltrate particular information, take screenshots.
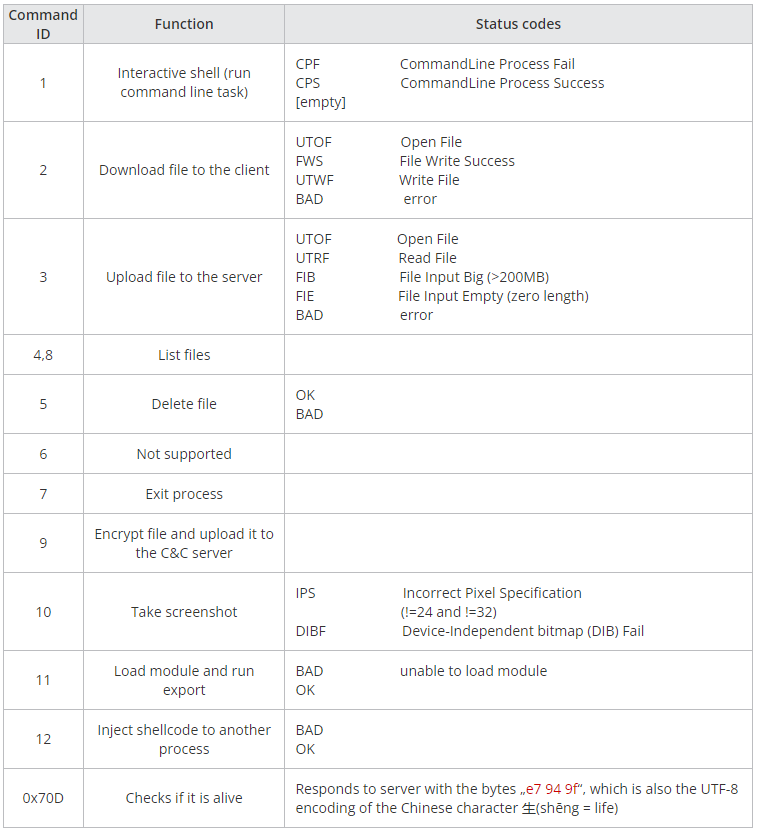
Development Micro has found an earlier model of WhiskerSpy that use the FTP protocol as a substitute of HTTP for C2 communication. This older variant additionally checks for the presence of a debugger upon execution and informs the C2 with the suitable standing code.
To notice, the researchers’ confidence in attributing this watering gap assault to Earth Kitsune is medium however the modus operandi and the targets are much like actions beforehand related to the group.
[ad_2]