[ad_1]

Royal Ransomware is the newest ransomware operation so as to add help for encrypting Linux gadgets to its most up-to-date malware variants, particularly concentrating on VMware ESXi digital machines.
BleepingComputer has been reporting on comparable Linux ransomware encryptors launched by a number of different gangs, together with Black Basta, LockBit, BlackMatter, AvosLocker, REvil, HelloKitty, RansomEXX, and Hive.
The brand new Linux Royal Ransomware variant was found by Will Thomas of the Equinix Risk Evaluation Middle (ETAC), and is executed utilizing the command line.
It additionally comes with help for a number of flags that may give the ransomware operators some management over the encryption course of:
- -stopvm > stops all operating VMs to allow them to be encrypted
- -vmonly – Solely encrypt digital machines
- -fork – unknown
- -logs – unknown
- -id: id have to be 32 characters
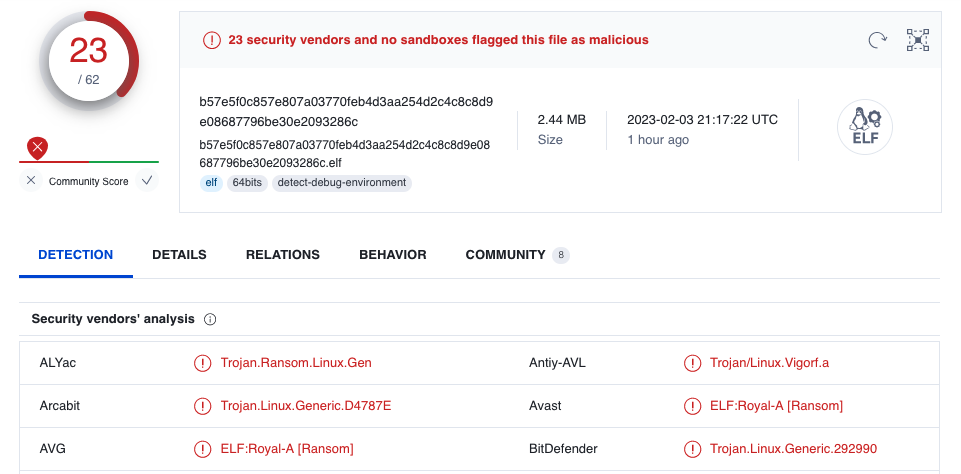
When encrypting recordsdata the ransomware will append the .royal_u extension to all encrypted recordsdata on the VM.
Whereas anti-malware options had points detecting Royal Ransomware samples that bundle the brand new concentrating on capabilities, they’re now detected by 23 out of 62 malware scanning engines on VirusTotal.
Who’s Royal Ransomware?
Royal Ransomware is a personal operation comprised of seasoned risk actors who beforehand labored with the Conti ransomware operation
Beginning in September, Royal ramped up malicious actions months after first being noticed in January 2022.
Whereas they initially utilized encryptors from different operations, resembling BlackCat, they transitioned to utilizing their very own, beginning with Zeon which dropped ransom notes much like these generated by Conti.
In mid-September, the group rebranded as “Royal” and started deploying a brand new encryptor in assaults that produces ransom notes with the identical identify.
The gang calls for ransom funds starting from $250,000 to tens of thousands and thousands after encrypting their targets’ enterprise community techniques.
In December, the U.S. Division of Well being and Human Companies (HHS) warned of Royal ransomware assaults concentrating on organizations within the Healthcare and Public Healthcare (HPH) sector.
Most ransomware strains now additionally goal Linux
The ransomware teams’ shift in the direction of concentrating on ESXi digital machines aligns with a development the place enterprises have transitioned to VMs as they arrive with improved gadget administration and far more environment friendly useful resource dealing with.
After deploying their payloads on ESXi hosts, the ransomware operators use a single command to encrypt a number of servers.
“The rationale why most ransomware teams carried out a Linux-based model of their ransomware is to focus on ESXi particularly,” Wosar informed BleepingComputer final 12 months.
You will discover extra data on Royal Ransomware and what to do in case you get hit in this help matter on the BleepingComputer discussion board.
Tens of hundreds of VMware ESXi servers uncovered on the Web reached their end-of-life in October, in keeping with a Lansweeper report.
These techniques will solely obtain technical help any more however no safety updates, which exposes them to ransomware assaults.
To place issues in perspective and present simply how uncovered to assaults such servers are, a brand new ransomware pressure generally known as ESXiArgs was used to scan for and encrypt unpatched servers in a huge marketing campaign concentrating on ESXi gadgets worldwide this Friday.
Inside only a few hours, over 100 servers worldwide have been compromised in these assaults, in keeping with a Shodan search.
[ad_2]