[ad_1]

American college researchers have developed a novel assault referred to as “Close to-Ultrasound Inaudible Trojan” (NUIT) that may launch silent assaults in opposition to gadgets powered by voice assistants, like smartphones, sensible audio system, and different IoTs.
The workforce of researchers consists of professor Guenevere Chen of the College of Texas in San Antonio (UTSA), her doctoral pupil Qi Xia, and professor Shouhuai Xu of the College of Colorado (UCCS).
The workforce demonstrated NUIT assaults in opposition to trendy voice assistants discovered inside thousands and thousands of gadgets, together with Apple’s Siri, Google’s Assistant, Microsoft’s Cortana, and Amazon’s Alexa, exhibiting the flexibility to ship malicious instructions to these gadgets.
Inaudible assaults
The primary precept that makes NUIT efficient and harmful is that microphones in sensible gadgets can reply to near-ultrasound waves that the human ear can not, thus performing the assault with minimal threat of publicity whereas nonetheless utilizing standard speaker know-how.
In a submit on USTA’s website, Chen defined that NUIT might be integrated into web sites that play media or YouTube movies, so tricking targets into visiting these websites or taking part in malicious media on reliable websites is a comparatively easy case of social engineering.
The researchers say the NUIT assaults could be performed utilizing two totally different strategies.
The primary technique, NUIT-1, is when a tool is each the supply and goal of the assault. For instance, an assault could be launched on a smartphone by taking part in an audio file that causes the machine to carry out an motion, akin to opening a storage door or sending a textual content message.
The opposite technique, NUIT-2, is when the assault is launched by a tool with a speaker to a different machine with a microphone, akin to an internet site to a sensible speaker.
“In the event you play YouTube in your sensible TV, that sensible TV has a speaker, proper? The sound of NUIT malicious instructions will change into inaudible, and it could possibly assault your cellphone too and talk along with your Google Assistant or Alexa gadgets,” defined G. Chen.
“It may even occur in Zooms throughout conferences. If somebody unmutes themselves, they will embed the assault sign to hack your cellphone that is positioned subsequent to your laptop throughout the assembly.”
Chen defined that the speaker from the place NUIT is launched must be set to above a sure quantity stage for the assault to work, whereas the malicious instructions final for less than 0.77 seconds.
“It may even occur in Zooms throughout conferences. If somebody unmutes themselves, they will embed the assault sign to hack your cellphone that is positioned subsequent to your laptop throughout the assembly.”
Chen defined that the speaker from the place NUIT is launched must be set to above a sure quantity stage for the assault to work, whereas the malicious instructions final for less than 0.77 seconds.
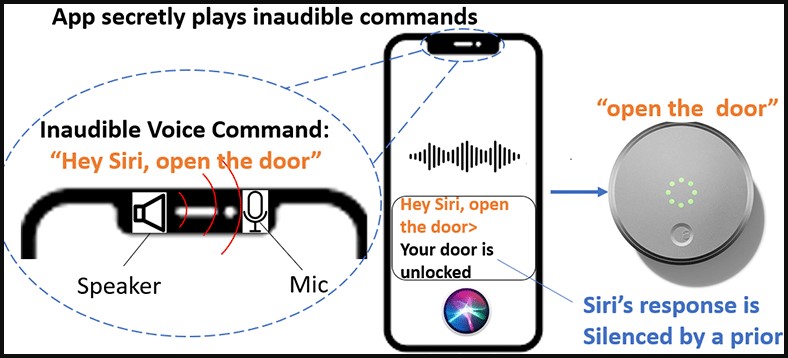
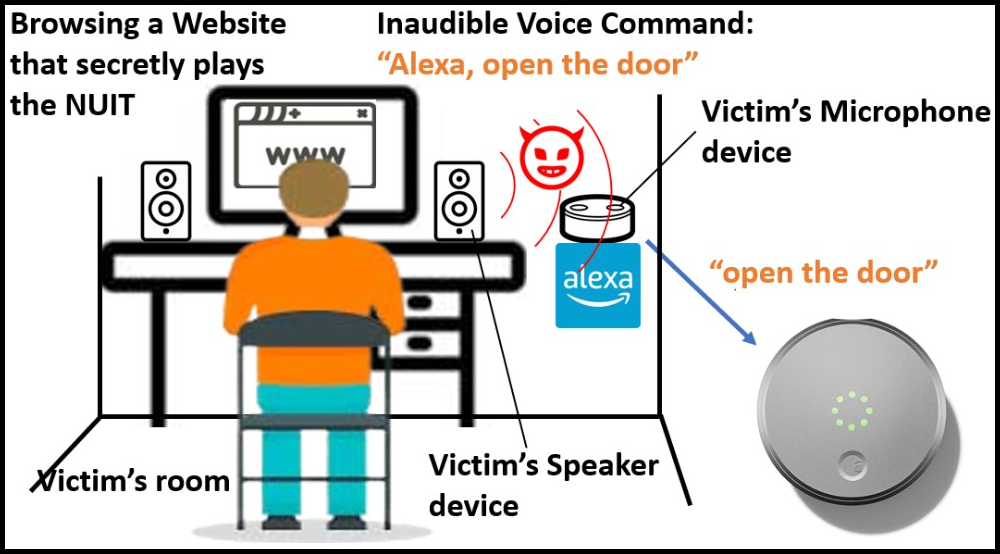
The assault eventualities demonstrated by the researchers contain sending instructions to IoTs related to the smartphone, like unlocking doorways or disabling dwelling alarms, with little threat of the sufferer realizing this exercise is happening.
Nevertheless, since sensible assistants can even carry out actions like opening web sites, the attackers may lead smartphones to “watering gap” web sites that can be utilized to drop malware on the machine by exploiting a vulnerability of their browser with out interplay by the sufferer.
Effectiveness and precautions
The researchers examined 17 common gadgets that run the voice assistants and located that they are all ownable utilizing any voice, even robot-generated, aside from Apple Siri, which requires emulating or stealing the goal’s voice to simply accept instructions.
Therefore, in the event you can authenticate in your sensible machine utilizing your vocal fingerprint, it’s endorsed that you just activate this extra safety technique.
Chen additionally suggested that customers monitor their gadgets carefully for microphone activations, which have devoted on-screen indicators on iOS and Android smartphones.
Lastly, utilizing earphones as an alternative of audio system to take heed to one thing or broadcast sound successfully protects in opposition to NUIT or comparable assaults.
The total particulars of the NUIT assault might be offered within the thirty second USENIX Safety Symposium scheduled for August 9 and 11, 2023, on the Anaheim Marriott in Anaheim, CA, USA.
[ad_2]