[ad_1]
A ransomware menace referred to as HardBit has moved to model 2.0 and its operators try to barter a ransom cost that may be lined by the sufferer’s insurance coverage firm.
Particularly, the menace actor tries to persuade the sufferer that it’s of their curiosity to reveal all insurance coverage particulars to allow them to modify their calls for so the insurer would cowl all prices.
Emergence of HardBit 2.0
The primary model of HardBit was noticed in October 2022, whereas model 2.0 was launched in November 2022 and it’s nonetheless the presently circulating variant, in keeping with a report from Varonis, a knowledge safety and analytics firm.
In contrast to most ransomware operations, HardBit doesn’t characteristic a knowledge leak web site, though its operators declare to steal sufferer information and threaten to leak it except a ransom is paid.
As a ransomware pressure, HardBit 2.0 options some capabilities to decrease the sufferer’s safety, like modifying the Registry to disable Home windows Defender’s real-time behavioral monitoring, course of scanning, and on-access file protections.
The malware additionally targets 86 processes for termination, to make delicate information obtainable for encryption. It set up persistence by including itself to the “Startup” folder, and deletes the Quantity Shadow copies to make information restoration tougher.
An fascinating ingredient in regards to the encryption section is that as an alternative of writing encrypted information to file copies and deleting the originals like many strains do, HardBit 2.0 opens the information and overwrites their content material with encrypted information.
This method makes it tougher for consultants to get better the unique information and makes the encryption barely sooner.
Ransom negotiation
Like different ransomware strains, the be aware that HardBit 2.0 drops on the sufferer’s system doesn’t inform of the quantity the hackers need in trade for the decryption key. Victims get 48 hours to contact the attacker over an open-source encrypted peer-to-peer communications messaging app.
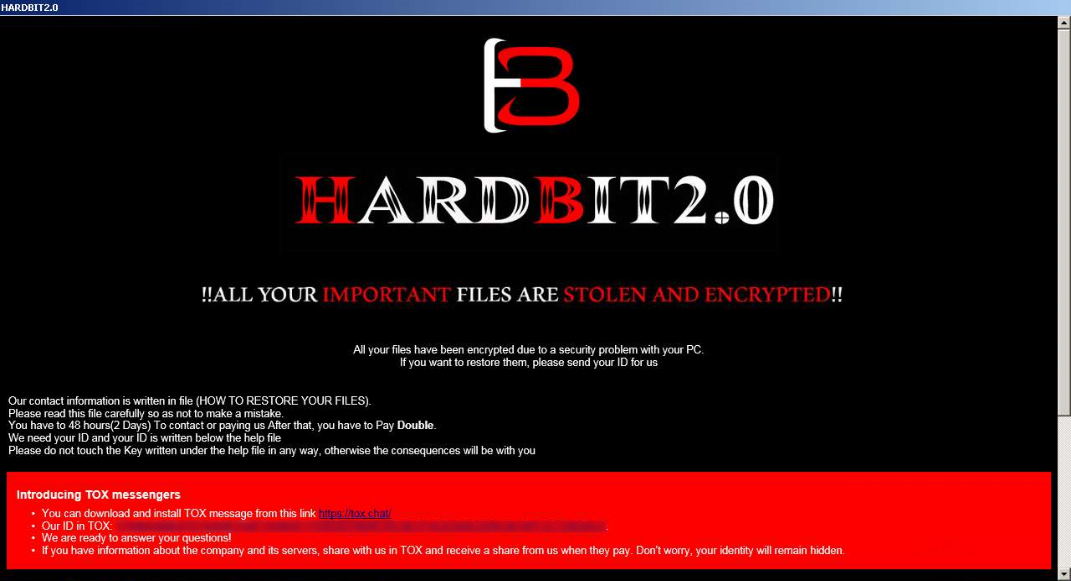
The menace actor advises the victims to not work with intermediaries, since this might solely drive up the full value, however to contact them straight for negotiations.
For firms which have insurance coverage for cyberattacks, the hackers have a extra elaborate set of directions and urge them to reveal the insurance coverage quantity for profitable dialogue.
Much more, the hackers make it appear to be sharing the insurance coverage particulars is helpful to the sufferer, portray the insurer because the dangerous man that stands in the best way of recovering their information.
The menace actors say that insurers by no means negotiate with ransomware actors with their shopper’s pursuits in thoughts, so that they make ludicrous counter-offers to their calls for simply to derail the negotiations and refuse to pay.
“To keep away from all this and get the cash on the insurance coverage, make sure you inform us anonymously in regards to the availability and phrases of the insurance coverage protection, it advantages each you and us, but it surely doesn’t profit the insurance coverage firm,” HardBit operators say in a be aware to victims.
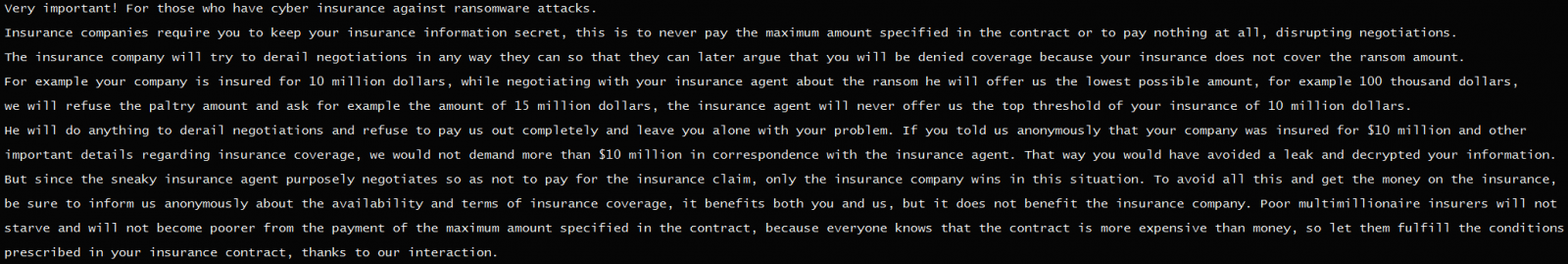
The attackers say that in the event that they know the precise insurance coverage quantity, they’d know precisely how a lot to ask so the insurer is compelled to cowl the demand.
In fact, victims are additionally usually contractually restricted to not disclose insurance coverage particulars to the attackers, and doing so dangers shedding any probability of the insurer masking the damages. For this reason the hackers insist on these particulars to be shared privately.
No matter their provide, ransomware operators’ purpose is to receives a commission and they’d say something to get the cash. The fact is that they can’t be trusted.
Refusing to pay the ransom and reporting the incident to legislation enforcement together with having a constant backup technique are the one methods to battle one of these menace and produce it to an finish.
The report from Varonis offers technical particulars on how HardBit 2.0 works ranging from the preliminary stage and disabling security measures to gaining persistence and deploying the encryption routine. The researchers have additionally shared indicators of compromise (IoCs) that assist establish the menace.
[ad_2]