[ad_1]

A digitally signed and trojanized model of the 3CX Voice Over Web Protocol (VOIP) desktop consumer is reportedly getting used to focus on the corporate’s prospects in an ongoing provide chain assault.
3CX is a VoIP IPBX software program growth firm whose 3CX Telephone System is utilized by greater than 600,000 corporations worldwide and has over 12 million every day customers.
The firm’s buyer listing features a lengthy listing of high-profile corporations and organizations like American Categorical, Coca-Cola, McDonald’s, BMW, Honda, AirFrance, NHS, Toyota, Mercedes-Benz, IKEA, and HollidayInn.
In response to alerts from safety researchers from Sophos and CrowdStrike, the attackers are focusing on each Home windows and macOS customers of the compromised 3CX softphone app.
“The malicious exercise contains beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small variety of instances, hands-on-keyboard exercise,” CrowdStrike’s risk intel staff stated.
“The most typical post-exploitation exercise noticed thus far is the spawning of an interactive command shell,” Sophos added in an advisory issued through its Managed Detection and Response service.
Whereas CrowdStrike suspects a North Korean state-backed hacking group it tracks as Labyrinth Collima is behind this assault, Sophos’ researchers say they “can’t confirm this attribution with excessive confidence.”
Labyrinth Collima exercise is understood to overlap with different risk actors tracked as Lazarus Group by Kaspersky, Covellite by Dragos, UNC4034 by Mandiant, Zinc by Microsoft, and Nickel Academy by Secureworks.
“CrowdStrike has an in-depth analytic course of relating to naming conventions of adversaries,” the corporate advised BleepingComputerr through e mail.
“LABYRINTH CHOLLIMA is a subset of what has been described as Lazarus Group, which incorporates different DPRK-nexus adversaries, together with SILENT CHOLLIMA and STARDUST CHOLLIMA.”
SmoothOperator software program provide chain assault
SentinelOne and Sophos additionally revealed in studies revealed Thursday night that the trojanized 3CX desktop app is being downloaded in a provide chain assault.
This provide chain assault, dubbed ‘SmoothOperator’ by SentinelOne, begins when the MSI installer is downloaded from 3CX’s web site or an replace is pushed to an already put in desktop software.
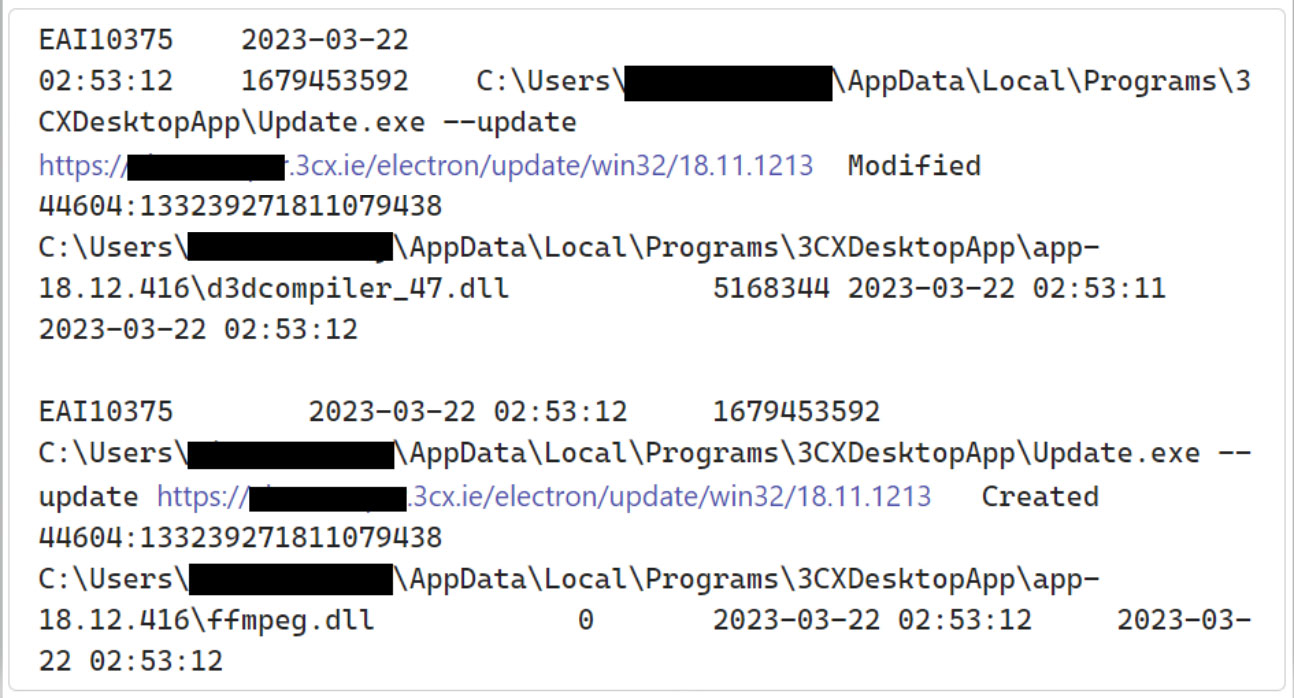
When the MSI or replace is put in, it’s going to extract a malicious ffmpeg.dll [VirusTotal] and the d3dcompiler_47.dll [VirusTotal] DLL information, that are used to carry out the following stage of the assault.
Whereas Sophos states that the 3CXDesktopApp.exe executable will not be malicious, the malicious ffmpeg.dll DLL will probably be sideloaded and used to extract an encrypted payload from d3dcompiler_47.dll and execute it.
SentinelOne explains that the malware will now obtain icon information hosted on GitHub that include Base64 encoded strings appended to the tip of the photographs, as proven beneath.
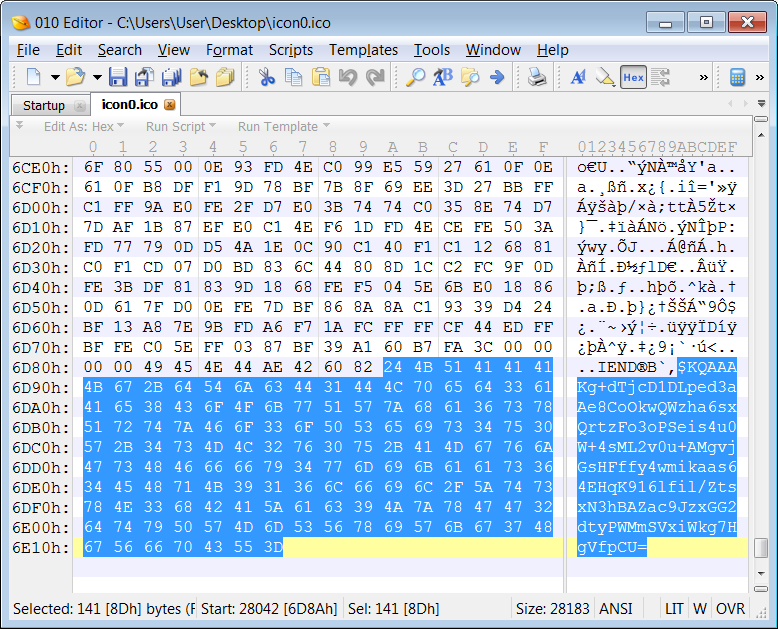
The GitHub repository the place these icons are saved reveals that the primary icon was uploaded on December seventh, 2022.
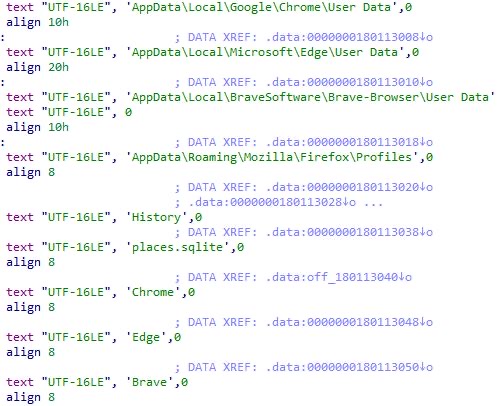
The primary-stage malware makes use of these Base64 strings to obtain a last payload to the compromised gadgets, a beforehand unknown information-stealing malware downloaded as a DLL.
This new malware is able to harvesting system information and stealing knowledge and saved credentials from Chrome, Edge, Courageous, and Firefox consumer profiles.
“Right now, we can’t affirm that the Mac installer is equally trojanized. Our ongoing investigation contains extra functions just like the Chrome extension that is also used to stage assaults,” SentinelOne stated.
“The risk actor has registered a sprawling set of infrastructure beginning as early as February 2022, however we don’t but see apparent connections to present risk clusters.”
Tagged as malicious by safety software program
CrowdStrike says that the trojanized model of 3CX’s desktop consumer will connect with one of many following attacker-controlled domains:
| akamaicontainer[.]com | msedgepackageinfo[.]com |
| akamaitechcloudservices[.]com | msstorageazure[.]com |
| azuredeploystore[.]com | msstorageboxes[.]com |
| azureonlinecloud[.]com | officeaddons[.]com |
| azureonlinestorage[.]com | officestoragebox[.]com |
| dunamistrd[.]com | pbxcloudeservices[.]com |
| glcloudservice[.]com | pbxphonenetwork[.]com |
| qwepoi123098[.]com | zacharryblogs[.]com |
| sbmsa[.]wiki | pbxsources[.]com |
| sourceslabs[.]com | journalide[.]org |
| visualstudiofactory[.]com |
A number of the domains talked about by prospects that the desktop consumer tried to hook up with embody azureonlinestorage[.]com, msstorageboxes[.]com, and msstorageazure[.]com.
BleepingComputer examined an allegedly trojanized model of the software program however was not in a position to in a position to set off any connections to those domains.
Nonetheless, a number of prospects in 3CX’s boards have acknowledged that they’ve been receiving alerts beginning one week in the past, on March 22, saying that the VoIP consumer app was marked as malicious by SentinelOne, CrowdStrike, ESET, Palo Alto Networks, and SonicWall safety software program.
Clients report that the safety alerts are triggered after putting in the 3CXDesktopApp 18.12.407 and 18.12.416 Home windows variations or the 18.11.1213 and the newest model on Macs.
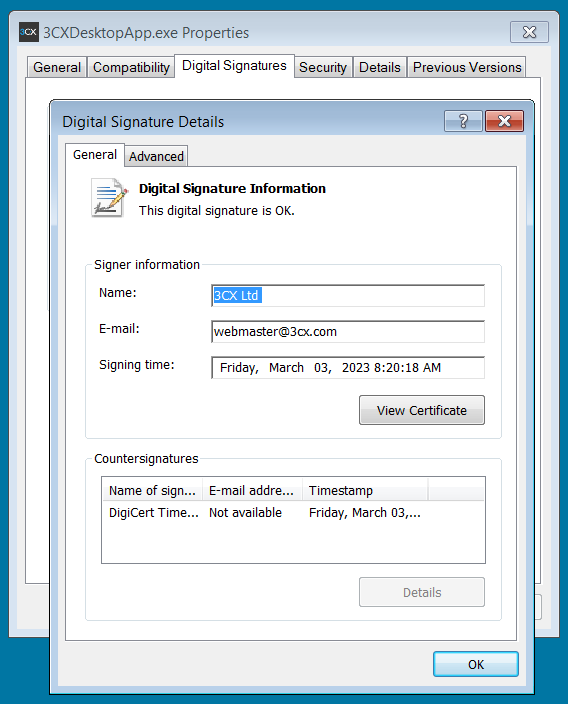
One of many trojanized 3CX softphone consumer samples shared by CrowdStrike was digitally signed over three weeks in the past, on March 3, 2023, with a professional 3CX Ltd certificates issued by DigiCert.
BleepingComputer confirmed this similar certificates was utilized in older variations of 3CX software program.
SentinelOne detects “penetration framework or shellcode” whereas analyzing the 3CXDesktopApp.exe binary, ESET tags it as a “Win64/Agent.CFM” trojan, Sophos as “Troj/Loader-AF”, and CrowdStrike’s Falcon OverWatch managed risk searching service warns customers to analyze their techniques for malicious exercise “urgently.”
Despite the fact that 3CX’s help staff members tagged it as a possible SentinelOne false optimistic in one of many discussion board threads full of buyer studies on Wednesday, the corporate is but to acknowledge the problems publicly.
A 3CX spokesperson did not reply to a request for remark when BleepingComputer reached out earlier at present.
Replace 3/29/23 9:31 PM ET: Up to date so as to add additional data from Sophos
[ad_2]