[ad_1]

The builders of the GoAnywhere MFT file switch answer are warning clients of zero-day distant code execution vulnerability on uncovered administrator consoles.
GoAnywhere is a safe internet file switch answer that enables corporations to securely switch encrypted information with their companions whereas holding detailed audit logs of who accessed the information.
The GoAnywhere safety advisory was first made public by reporter Brian Krebs, who posted a replica on Mastodon.
A buyer who acquired the notification instructed BleepingComputer that that is affecting each the on-premise and SaaS implementations of GoAnywhere however we couldn’t independently verify this right now.
Based on the safety advisory, the exploit requires entry to the executive console, which mustn’t usually be uncovered to the web.
“A Zero-Day Distant Code Injection exploit was recognized in GoAnywhere MFT,” warns the GoAnywhere safety advisory.
“The assault vector of this exploit requires entry to the executive console of the appliance, which normally is accessible solely from inside a non-public firm community, by way of VPN, or by allow-listed IP addresses (when working in cloud environments, resembling Azure or AWS).”
As there isn’t any patch presently obtainable for the zero-day vulnerability, Fortra urges admins to use the next mitigation:
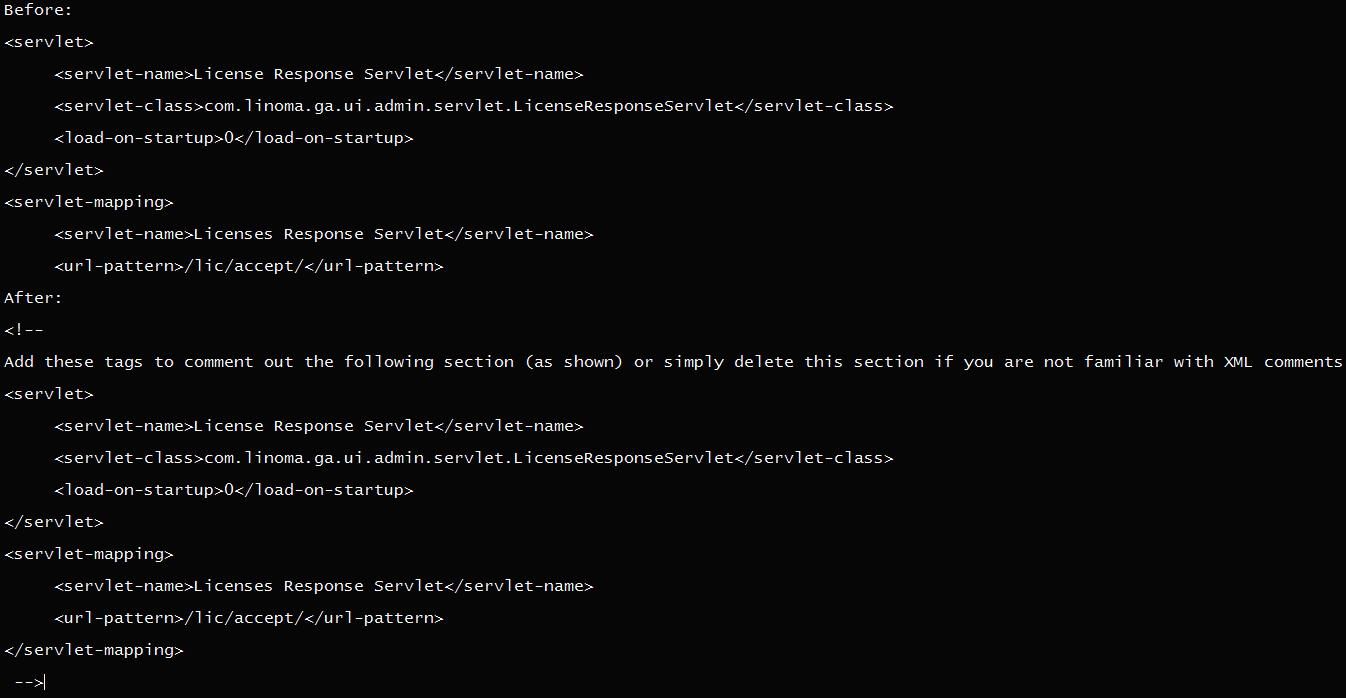
- On the file system the place GoAnywhere MFT is put in, edit the file “[install_dir]/adminroot/WEB_INF/internet.xml.”
- Discover and take away (delete or remark out) the next servlet and servlet-mapping configuration within the screenshot under.
- Restart the GoAnywhere MFT utility.
Presently, there isn’t any different technique to mitigate the assaults, as Fortra has not but made a safety replace obtainable.
Fortra has additionally briefly shut down its SaaS answer whereas they resolve the bug.
The corporate additionally recommends that Directors carry out an audit of their installations, together with:
- Examine to see if new, unknown admin accounts had been created by the ‘system’ and if the “Admin Audit Log exhibits a non-existent or disabled tremendous person creating this account.”
- Search the Administration log for exercise (Reporting -> Audit Logs -> Administration). Seek for something created by root person.
Safety skilled Kevin Beaumont has carried out a Shodan scan to find out what number of GoAnywhere cases are uncovered on the web and located 1,008 servers, primarily in the US.
Nevertheless, Beaumont mentioned that the majority admin consoles make the most of ports 8000 and 8001, of which BleepingComputer solely noticed 151 uncovered.
Whereas the assault floor could seem restricted, it is necessary to notice that enormous organizations use these merchandise to switch delicate information with their companions.
BleepingComputer has recognized native governments, healthcare corporations, banks, vitality corporations, monetary companies corporations, museums, and laptop half producers using the GoAnywhere file switch answer.
Therefore, even a single breach leveraging GoAnywhere MFT’s zero-day flaw might leak delicate data that could possibly be used for extortion.
This precise state of affairs was seen within the 2021 hacks of Accellion FTA (File Switch Equipment) by the Clop ransomware gang, which impacted many high-profile corporations worldwide.
BleepingComputer has contacted Fortra to ask for extra particulars about whether or not the assaults are actively exploited, and we are going to replace this put up as quickly as we obtain a response.
[ad_2]