[ad_1]

CISA and the FBI have issued a joint advisory highlighting the growing risk behind ongoing Royal ransomware assaults concentrating on many U.S. vital infrastructure sectors, together with healthcare, communications, and training.
This follows an advisory issued by the Division of Well being and Human Companies (HHS), whose safety crew revealed in December 2022 that the ransomware operation had been linked to a number of assaults towards U.S. healthcare organizations.
In response, the FBI and CISA shared indicators of compromise and a listing of techniques, strategies, and procedures (TTPs) linked, which might assist defenders detect and block makes an attempt to deploy Royal ransomware payloads on their networks.
“CISA encourages community defenders to overview the CSA and to use the included mitigations,” the U.S. cybersecurity company mentioned on Thursday.
The federal companies are asking all organizations liable to being focused to take concrete steps to guard themselves towards the rising ransomware risk.
To safeguard their organizations’ networks, enterprise admins can begin by prioritizing the remediation of any identified vulnerabilities attackers have already exploited.
Coaching workers to identify and report phishing makes an attempt successfully can also be essential. Cybersecurity defenses can additional be hardened by enabling and implementing multi-factor authentication (MFA), making it a lot more durable for attackers to entry delicate techniques and knowledge.
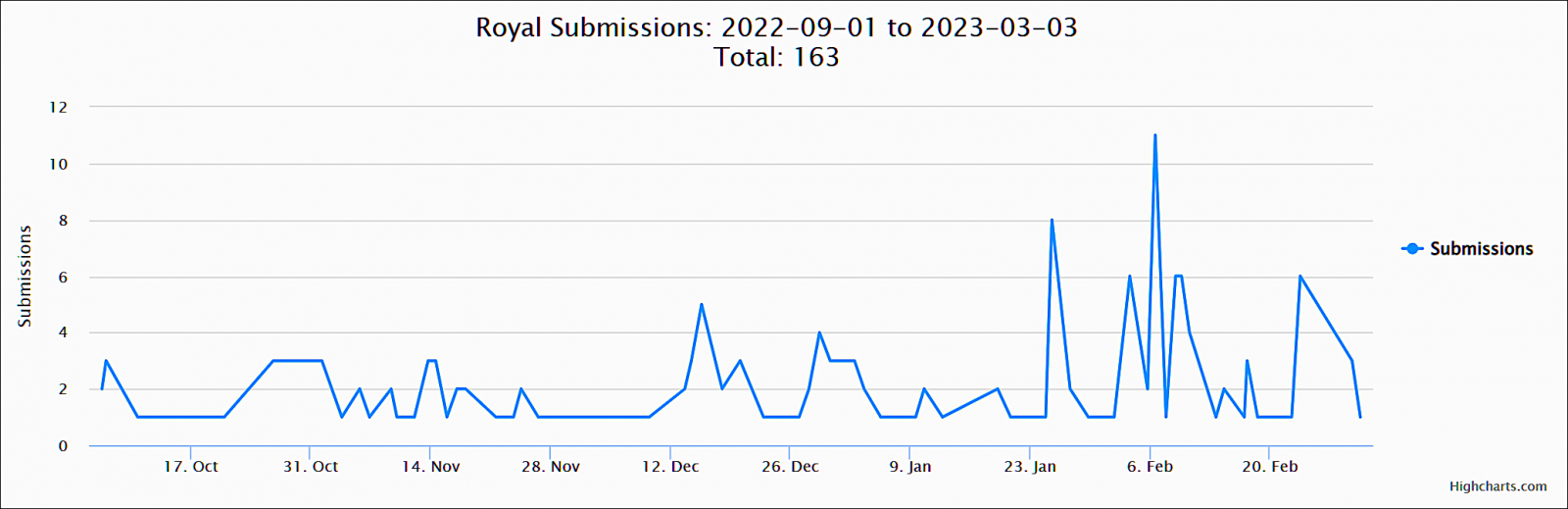
Samples submitted to the ID-Ransomware platform for evaluation present that the enterprise-targeting gang has been more and more lively beginning late January, exhibiting this ransomware operation’s large affect on its victims.
Request for Royal incident reviews
Regardless that the FBI says that paying ransoms will doubtless encourage different cybercriminals to affix the assaults, victims are urged to report Royal ransomware incidents to their native FBI discipline workplace or CISA no matter whether or not they’ve paid a ransom or not.
Any extra data will assist gather vital knowledge wanted to maintain monitor of the ransomware group’s exercise, assist cease additional assaults, or maintain the attackers accountable for his or her actions.
Royal Ransomware is a personal operation comprised of extremely skilled risk actors identified for beforehand working with the infamous Conti cybercrime gang. Their malicious actions have solely seen a soar in exercise since September, regardless of first being detected in January 2022.
Regardless that they initially deployed encryptors from different operations like BlackCat, they’ve since transitioned to utilizing their very own.
The primary was Zeon, which generated ransom notes much like these utilized by Conti, however they switched to a brand new encryptor in mid-September after rebranding to “Royal.”
The malware was not too long ago upgraded to encrypt Linux gadgets, particularly concentrating on VMware ESXi digital machines.
Royal operators encrypt their targets’ enterprise techniques and demand hefty ransom funds starting from $250,000 to tens of thousands and thousands per assault.
This ransomware operation additionally stands out from the gang attributable to its social engineering techniques to deceive company victims into putting in distant entry software program as a part of callback phishing assaults, the place they fake to be software program suppliers and meals supply providers.
As well as, the group employs a novel technique of using hacked Twitter accounts to tweet out particulars of compromised targets to journalists, hoping to draw information protection and add additional stress on their victims.
These tweets comprise a hyperlink to leaked knowledge, which the group allegedly stole from the victims’ networks earlier than encrypting them.
[ad_2]