[ad_1]

Coinbase pockets and different decentralized crypto apps (dapps) have been discovered to be susceptible to “pink capsule assaults,” a way that can be utilized to cover malicious good contract habits from security measures.
Coinbase is a number one cryptocurrency trade that gives a crypto pockets app for customers to retailer, handle, and work together with a variety of digital belongings they’ll buy from the platform, together with Bitcoin, Ethereum, and ERC-20 tokens.
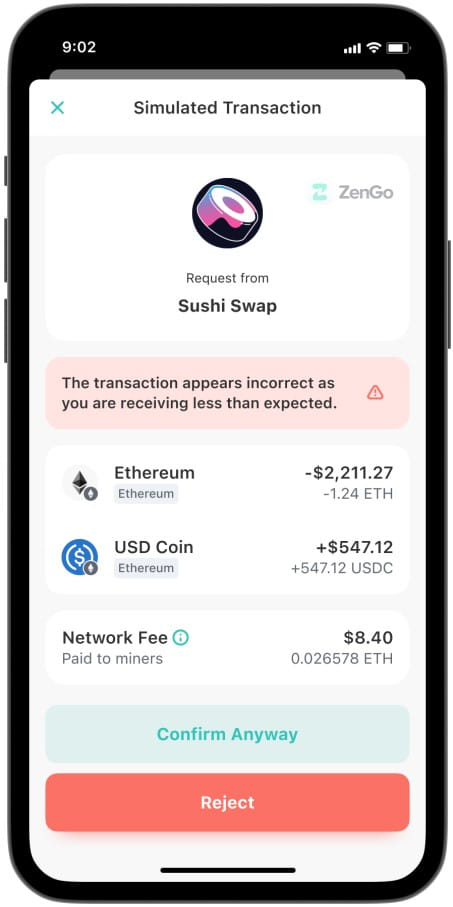
Safety researchers at ZenGo Pockets have found that dapps, together with the Coinbase Pockets, have been susceptible to a brand new assault that enables good contracts to cover malicious habits throughout transaction simulations. This causes the consumer to consider a transaction might be secure, and permit it to proceed, solely later studying that the good contract stole their belongings.
The vulnerability was disclosed to Coinbase, who has since addressed the reported safety issues and awarded ZenGo Pockets a number of bug bounties for his or her accountable disclosure.
Attacking the simulation
Web3 good contracts are applications that may robotically execute when a cryptocurrency takes place, permitting builders a variety of performance for web sites and crypto belongings.
For instance, good contracts can be utilized to robotically ship somebody an NFT after a fee is acquired, “tax” customers for promoting an asset too quickly after buying it, or robotically write content material to a web site primarily based on the transaction. Mainly, something that may be programmed might be executed by the good contract.
Nevertheless, menace actors additionally use good contracts for malicious causes, through the use of them to steal despatched crypto or drain a pockets of belongings.
These malicious contract signing requests are arduous to differentiate from official ones, making it difficult for cryptocurrency holders to navigate risks.
To stop these assaults, dapps builders have launched simulated transaction options to emulate signing a transaction and predict the result earlier than the consumer approves it. The results of these simulations is then introduced to the consumer, permitting them to see what’s going to occur and resolve in the event that they want to permit the transaction to proceed.
(ZenGo Pockets)
Nevertheless, because the ZenGo Pockets report highlights, some malicious good contracts can detect when they’re being simulated and display inauthentic habits to seem benign or worthwhile to the goal, therefore tricking the web3 emulation safety system.
The analysts clarify that menace actors may implement “pink drugs” in malicious contracts to vary their habits when simulated and steal cash from the targets when accepted in actuality.
This assault is performed by filling variables in a wise contract with “secure” knowledge throughout simulations after which swapping it with “malicious” knowledge throughout a reside transaction. This is able to trigger a simulation to point out a wise contract as secure throughout simulation, however throughout a reside transaction, it steals customers’ crypto.
“The “COINBASE” instruction comprises the handle of the present block miner. Since throughout simulation there is no such thing as a actual block and therefore no miner, some simulation implementations simply set it to the null handle (all zeros handle),” explains ZenGo’s report.
“Due to this fact a malicious good contract could weaponize this “COINBASE” pink capsule as follows: Ask customers to ship some native coin to the contract, if COINBASE is zero (which implies simulation in Polygon) the contract will ship again some cash in return, thus making the transaction probably worthwhile to the consumer when its pockets simulates it.”
“Nevertheless, when the consumer really sends the transaction on-chain, COINBASE is definitely full of the non-zero handle of the present miner and the contract simply takes the despatched cash.”
The researchers have additionally launched the next video to display this assault.
Discover that the simulation signifies that the consumer will get 0.016 WETH ($30) in the event that they approve the transaction request. Nevertheless, they get nothing in return when performing the reside transaction.
Affect
By exploring these “pink capsule assault” situations, ZenGo Pockets discovered six cryptocurrency pockets dapps susceptible to exploitation.
These are the Coinbase pockets, Rabby pockets, Blowfish, PocketUniverse, Hearth Extension, and an unnamed extension that has not mounted the issue but.
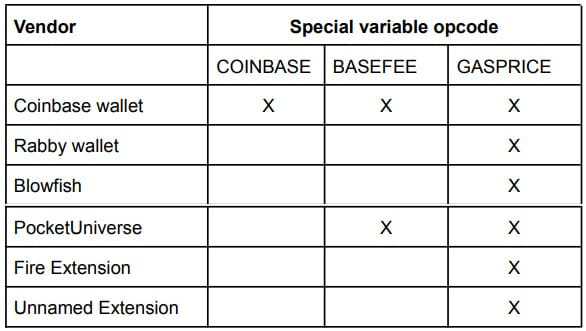
All different distributors talked about above have carried out fixes on their transaction simulation shortly after they acquired ZenGo Pockets’s report.
The repair for this assault is to cease utilizing arbitrary values for susceptible variables, stopping their use as “pink drugs” in malicious contracts.
[ad_2]