[ad_1]

The Clop ransomware gang is now additionally utilizing a malware variant that explicitly targets Linux servers, however a flaw within the encryption scheme has allowed victims to quietly recuperate their recordsdata at no cost for months.
This new Linux model of Clop was noticed in December 2022 by Antonis Terefos, a researcher at SentinelLabs, after the menace group used it along with the Home windows variant in an assault towards a college in Colombia.
Whereas similar to the Home windows model, as they each use the identical encryption methodology and virtually equivalent course of logic, there nonetheless are some variations, primarily restricted to OS API calls and options nonetheless ready to be carried out within the Linux variant.
Clop’s Linux malware can be in early improvement, because it’s nonetheless lacking correct obfuscation and evasiveness mechanisms, and it’s tormented by flaws that make it doable for victims to retrieve their recordsdata with out paying the crooks any cash.
Focusing on Oracle database servers
The Linux executable (ELF) of Clop ransomware creates a brand new course of upon launch, which makes an attempt to raise permissions to a stage that will permit knowledge encryption.
The recordsdata and folders it targets embrace the person’s “/house” listing, which incorporates all private recordsdata, the “/root” listing, “/decide,” and Oracle directories (“/u01” – “/u04”) used for storing database recordsdata or as mount factors for Oracle software program.
The precise concentrating on of Oracle database folders is just not generally seen in Linux ransomware encryptors, which normally give attention to encrypting ESXi digital machines.
The Linux variant additionally lacks assist for the hashing algorithm utilized by the Home windows model to exclude sure file varieties and folders from encryption. Additionally, there is no mechanism to deal with recordsdata of varied sizes in a different way on Linux.
Different options not current within the Linux model of Clop embrace the absence of drive enumeration, which might assist discover the place to begin for encrypting folders recursively, and command line parameters to supply extra management over the encryption course of.
Encryption flaws
The present Linux model may also not encrypt the RC4 keys used for file encryption with the RSA-based uneven algorithm used within the Home windows variant.
As an alternative, within the Linux model, Clop makes use of a hardcoded RC4 “grasp key” to generate the encrypting keys after which makes use of the identical key to encrypt it and retailer it regionally on the file. Additionally, the RC4 secret’s by no means validated, whereas, in Home windows, it is validated earlier than initiating the encryption.
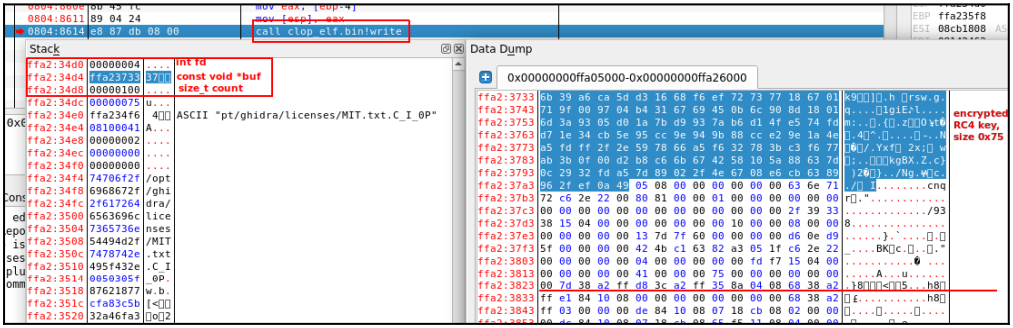
This weak scheme doesn’t shield the keys from being freely retrieved and the encryption from being reversed, which SentinelLabs has carried out (a Python script that does simply that’s now obtainable on GitHub).
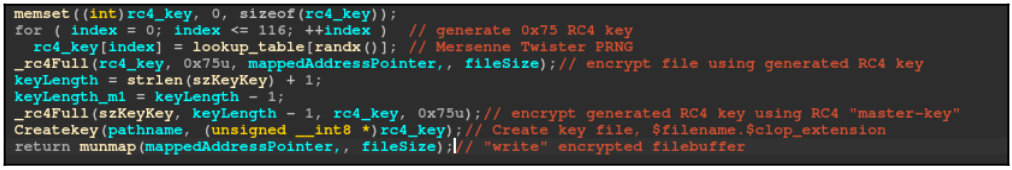
Along with the dearth of key safety, SentinelLabs additionally discovered that when the encrypted secret’s written to a file, the malware additionally writes some additional knowledge, like particulars in regards to the file, corresponding to its measurement and time of encryption.
This knowledge needs to be hid, because it might assist forensic specialists carry out focused decryption of particular, useful recordsdata.
Clop ransomware for Linux is unlikely to turn out to be a widespread menace in its present kind. The discharge of a decryptor will probably push its authors to launch safe and improved variations with a correct encryption scheme.
SentinelLabs advised BleepingComputer that that they had shared their decryptor with regulation enforcement, so they may assist victims recuperate their recordsdata.
“We shared our findings early with related regulation enforcement and intelligence companions and can proceed to collaborate with the related organizations to have an effect on the economics of the ransomware area in favor of defenders,” SentinelLabs advised BleepingComputer.
Regardless of its weaknesses, the usage of the Linux variant in precise Clop assaults demonstrates that, for the menace actors, having a Linux model, even one which’s simple to compromise, remains to be preferable to not with the ability to assault Linux techniques inside the goal organizations.
[ad_2]