[ad_1]

Over 15 million publicly dealing with providers are prone to not less than one of many 896 vulnerabilities listed in CISA’s KEV (identified exploitable vulnerabilities) catalog.
This huge quantity is reported by cybersecurity firm Rezilion, which carried out large-scale analysis to determine weak methods uncovered to cyberattacks from risk actors, whether or not state-sponsored or ransomware gangs.
Rezilion’s findings are significantly worrying as a result of the examined vulnerabilities are identified and highlighted in CISA’s KEV catalog as actively exploited by hackers, so any delays of their patching preserve a big assault floor, giving risk actors quite a few potential targets.
Uncovered to assaults
Rezilion used the Shodan net scanning service to search out endpoints which might be nonetheless weak to CVEs added to CISA’s Recognized Exploitable Vulnerabilities Catalog.
Utilizing these customized search queries, the researchers discovered 15 million situations weak to 200 CVEs from the catalog.
Over half of these 7 million situations had been weak to one of many 137 CVEs regarding Microsoft Home windows, making this part a high precedence for defenders and a very good goal for attackers.
Excluding Home windows, Rezilion has recognized the next top-ten CVEs:
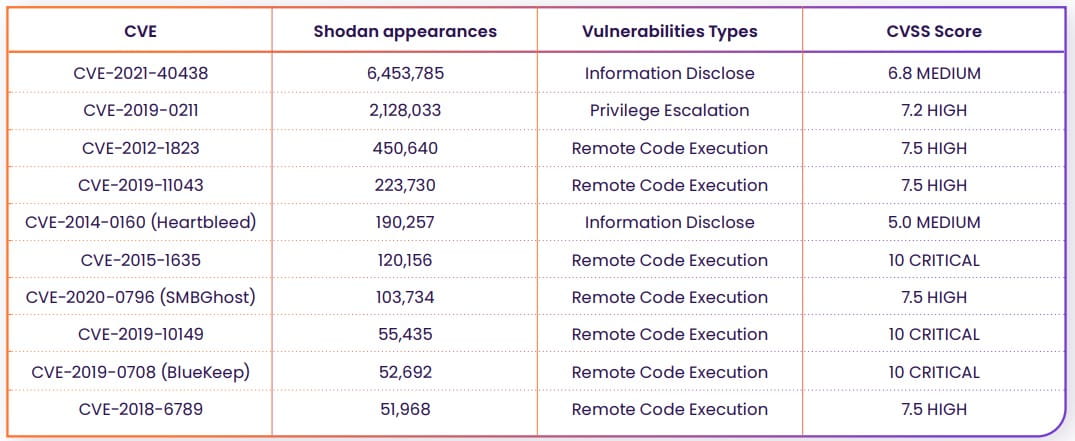
Nearly half of these are over 5 years previous, so roughly 800,000 machines haven’t utilized safety updates for a big time period.
“Total, over 4.5 million internet-facing gadgets had been recognized as weak to KEVs found between 2010 and 2020,” feedback Rezilion in the report.
“It is extremely regarding that these machines didn’t patch the related revealed updates for years although a patch was launched, and these vulnerabilities are identified to be exploited within the wild.”
Some notable CVEs highlighted within the Rezilion report are:
- CVE-2021-40438: medium-severity info disclosure flaw showing in virtually 6.5 million Shodan outcomes, impacting Apache HTTPD servers v2.4.48 and older.
- Proxyshell: a set of three vulnerabilities impacting Microsoft Change, which Iranian APTs chained collectively for distant code execution assaults in 2021. Shodan returns 14,554 outcomes right now.
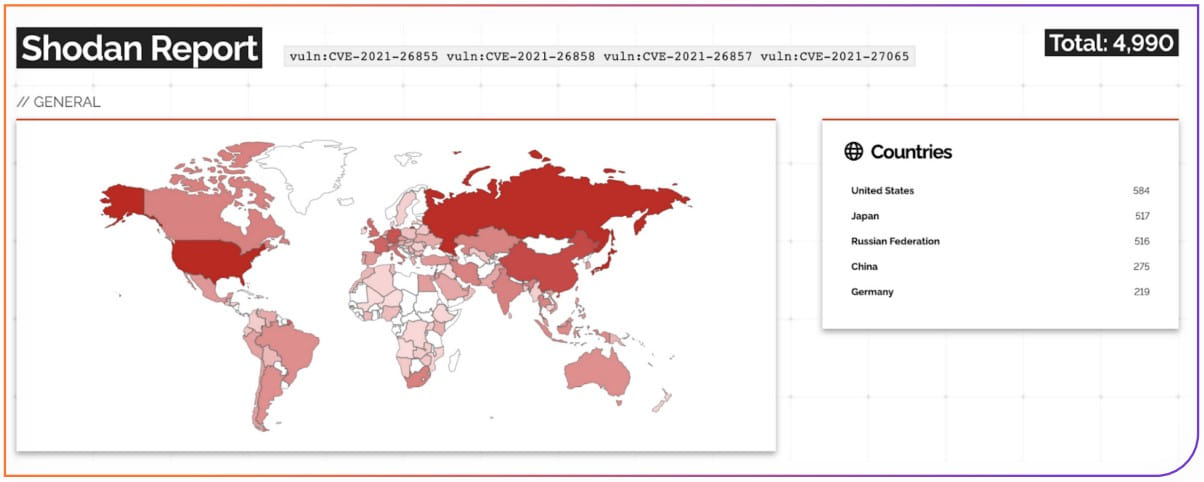
- ProxyLogon: a set of 4 flaws impacting Microsoft Change, which Russian hackers extensively leveraged in 2021 in opposition to U.S. infrastructure. There are nonetheless 4,990 methods weak to ProxyLogon, in line with Shodan, with 584 situated within the U.S.
- HeartBleed (CVE-2014-0160): medium-severity flaw impacting OpenSSL, permitting attackers to leak delicate info from a course of reminiscence. Shodan says a whopping 190,446 are nonetheless weak to this flaw.
Moreover, for CVE-2021-40438, that enormous quantity corresponds to the variety of web sites/providers operating on Apache, not particular person gadgets, as many web sites will be hosted on a single server.
It’s also vital to underline that Rezilion’s 15 million uncovered endpoints estimate is conservative, containing solely non-duplicates and likewise leaving out instances for which the researchers couldn’t discover queries that narrowed down product variations.
Rezilion additionally instructed BleepingComputer that they didn’t solely depend on built-in Shodan CVE searches for his or her analysis however created customized search queries that decided the variations of software program operating on gadgets.
“For a number of the vulnerabilities we’ve got Shodan’s inherent tags, however largely we carried out our personal evaluation which included figuring out the precise weak variations for each affected product and designing particular shodan queries that may permit us to determine indications of those variations within the metadata seen to Shodan,” defined Rezilion’s Director of vulnerability analysis, Yotam Perkal, to BleepingComputer.
Exploitation makes an attempt
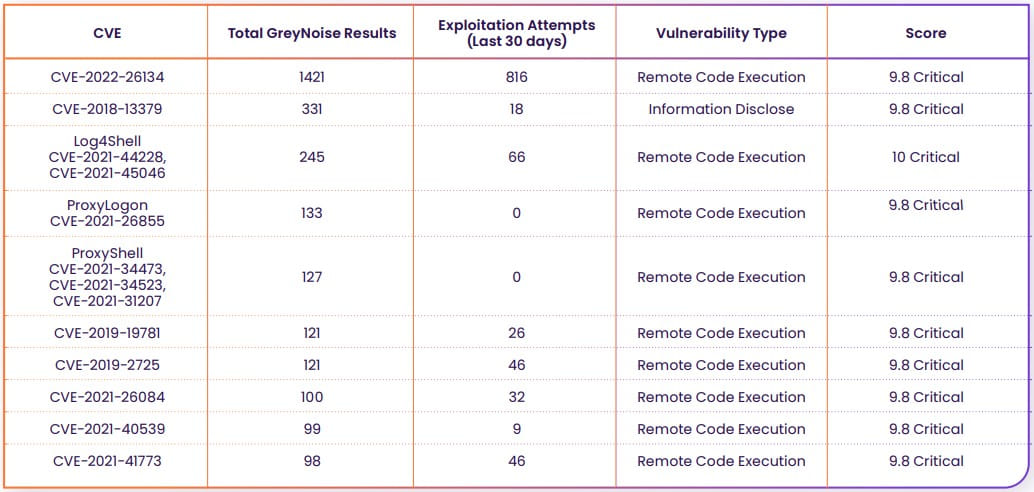
Publicity is one factor, however curiosity from hackers is one other, and to reply this, Rezilion used information from Greynoise that screens and categorizes vulnerability exploitation makes an attempt.
On the high of the checklist with probably the most exploited flaws is CVE-2022-26134, having 1,421 leads to GreyNoise, and 816 exploitation makes an attempt previously month.
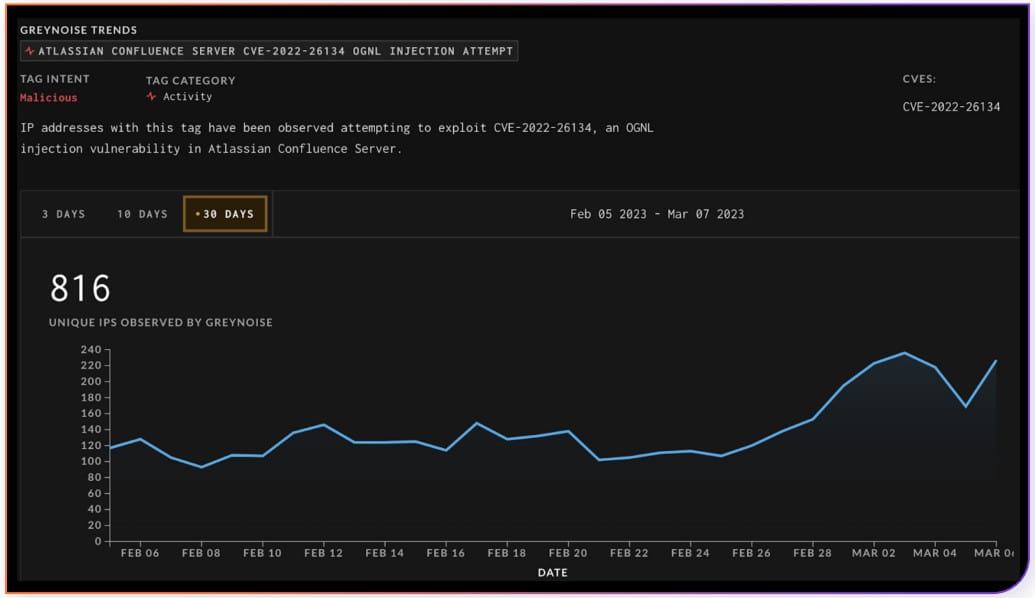
This critical-severity flaw in Atlassian Confluence Server and Information Middle permits a distant attacker to execute an Object-Graph Navigation Language expression on the weak occasion.
Different flaws rating excessive within the checklist embody CVE-2018-13379, a pre-authentication arbitrary recordsdata learn impacting FortiOS gadgets, which has 331 outcomes on GreyNoise, and Log4Shell, a nasty code execution bug on Log4J2 that had 66 exploitation makes an attempt previously month.
Patching all flaws in your setting is the obvious resolution to those dangers,
Nevertheless, if this can be a difficult process to your group, prioritizing important flaws in your setting or securing them behind a firewall ought to be the way in which to go.
Rezilion says that flaws in Microsoft Home windows, Adobe Flash Participant, Web Explorer, Google Chrome, Microsoft Workplace, and Win32k make up one-fourth of CISA’s KEV catalog, so these merchandise can be place to begin.
[ad_2]