[ad_1]

A ten-year-old Home windows vulnerability remains to be being exploited in assaults to make it seem that executables are legitimately signed, with the repair from Microsoft nonetheless “opt-in” in any case these years. Even worse, the repair is eliminated after upgrading to Home windows 11.
On Wednesday evening, information broke that VoIP communications firm 3CX was compromised to distribute trojanized variations of its Home windows desktop software in a large-scale provide chain assault.
As a part of this provide chain assault, two DLLs utilized by the Home windows desktop software had been changed with malicious variations that obtain further malware to computer systems, resembling an information-stealing trojan.
One of many malicious DLLs used within the assault is often a reputable DLL signed by Microsoft named d3dcompiler_47.dll. Nevertheless, the risk actors modified the DLL to incorporate an encrypted malicious payload on the finish of the file.
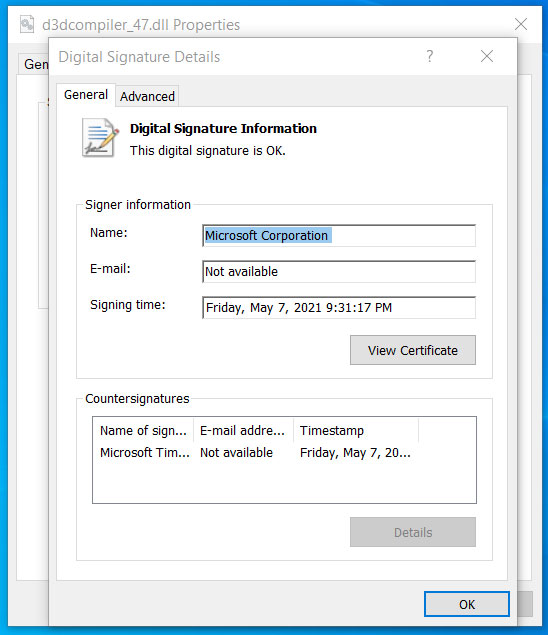
As first famous yesterday, regardless that the file was modified, Home windows nonetheless confirmed it as appropriately signed by Microsoft.
Supply: BleepingComputer
Code signing an executable, resembling a DLL or EXE file, is supposed to guarantee Home windows customers that the file is genuine and has not been modified to incorporate malicious code.
When a signed executable is modified, Home windows will show a message stating that the “digital signature of the item didn’t confirm.” Nevertheless, regardless that we all know that the d3dcompiler_47.dll DLL was modified, it nonetheless confirmed as signed in Home windows.
After contacting Will Dormann, a senior vulnerability analyst at ANALYGENCE, about this habits and sharing the DLL, we had been informed that the DLL is exploiting the CVE-2013-3900 flaw, a “WinVerifyTrust Signature Validation Vulnerability.”
Microsoft first disclosed this vulnerability on December tenth, 2013, and defined that including content material to an EXE’s authenticode signature part (WIN_CERTIFICATE construction) in a signed executable is feasible with out invalidating the signature.
For instance, Dormann defined in tweets that the Google Chrome installer provides information to the Authenticode construction to find out in the event you opted into “sending utilization statistics and crash experiences to Google.” When Google Chrome is put in, it would verify the authenticode signature for this information to find out if diagnostic experiences ought to be enabled.
Microsoft in the end determined to make the repair optionally available, doubtless as a result of it could invalidate reputable, signed executables that saved information within the signature block of an executable.
“On December 10, 2013, Microsoft launched an replace for all supported releases of Microsoft Home windows that modifications how signatures are verified for binaries signed with the Home windows Authenticode signature format,” explains Microsoft’s disclosure for the CVE-2013-3900.
“This transformation may be enabled on an opt-in foundation.”
“When enabled, the brand new habits for Home windows Authenticode signature verification will not permit extraneous data within the WIN_CERTIFICATE construction, and Home windows will not acknowledge non-compliant binaries as signed.”
It’s now shut to 10 years later, with the vulnerability recognized to be exploited by quite a few risk actors. But, it stays an opt-in repair that may solely be enabled by manually enhancing the Home windows Registry.
To allow the repair, Home windows customers on 64-bit methods could make the next Registry modifications:
Home windows Registry Editor Model 5.00
[HKEY_LOCAL_MACHINESoftwareMicrosoftCryptographyWintrustConfig]
“EnableCertPaddingCheck”=”1”
[HKEY_LOCAL_MACHINESoftwareWow6432NodeMicrosoftCryptographyWintrustConfig]
“EnableCertPaddingCheck”=”1”
As soon as these Registry keys are enabled, you possibly can see how in another way Microsoft validates the signature within the malicious d3dcompiler_47.dll DLL used within the 3CX provide chain assault.
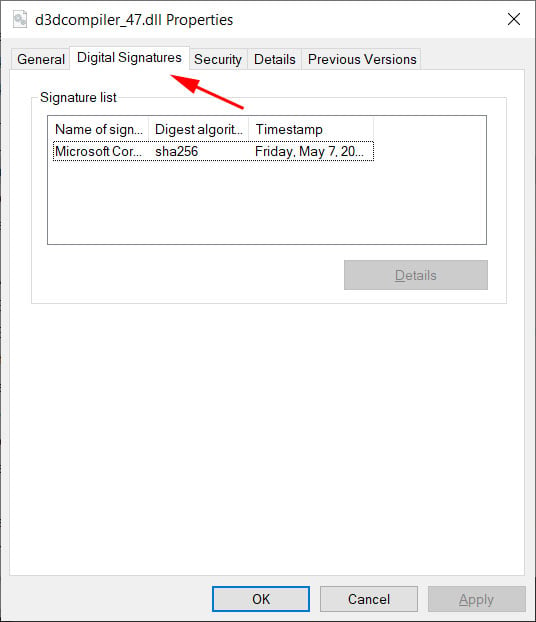 |
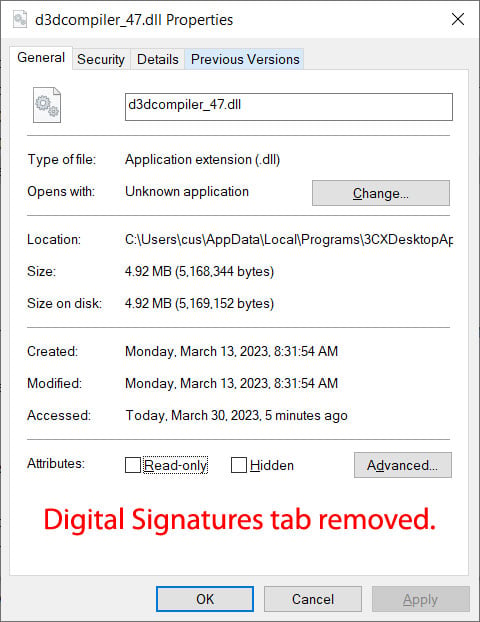 |
To make issues worse, even in the event you add the Registry keys to use the repair, they are going to be eliminated when you improve to Home windows 11, making your machine weak once more.
Because the vulnerability has been utilized in latest assaults, such because the 3CX provide chain and a Zloader malware distribution marketing campaign in January, it has grow to be clear that it ought to be mounted, even when that inconveniences builders.
Sadly, most do not learn about this flaw and can take a look at a malicious file and assume it is reliable as Home windows experiences it as being so.
“However when a repair is optionally available, the lots aren’t going to be protected,” warned Dormann.
I enabled the optionally available repair, used the pc as typical all through the day, and didn’t run into any points that made me remorse my determination.
Whereas this will trigger a problem with some installers, like Google Chrome, not displaying as signed, the added safety is well worth the inconvenience.
BleepingComputer reached out to Microsoft in regards to the continued abuse of this flaw and it solely being an opt-in repair however has not obtained a reply.
[ad_2]