[ad_1]

An ongoing phishing marketing campaign is pretending to be Trezor information breach notifications trying to steal a goal’s cryptocurrency pockets and its belongings.
Trezor is a {hardware} cryptocurrency pockets the place customers can retailer their cryptocurrency offline moderately than in cloud-based wallets or wallets saved on their units. Utilizing a {hardware} pockets like Trezor provides safety from malware and compromised units, because the pockets will not be meant to be related to your PC.
When organising a brand new Trezor pockets, customers are given a 12 or 24-word restoration seed that can be utilized to recuperate a pockets if a tool is stolen, misplaced, or malfunctions.
Nevertheless, anybody who beneficial properties entry to this seed can even restore the pockets on their very own units, making them juicy targets for menace actors.
Huge phishing marketing campaign targets Trezor customers
Beginning on February twenty seventh, Trezor prospects started receiving SMS and e mail phishing messages stating that Trezor had suffered an information breach. These messages immediate the goal to go to a listed web site to safe their system.
“Trezor Suite has not too long ago endured a safety breach, assume all of your belongings are susceptible. Please observe the safety process to safe your belongings: [phishing-site],” reads the pretend Trezor information breach warning messages.
BleepingComputer acquired considered one of these phishing emails. A safety researcher often called Mich has additionally been receiving and reporting the quite a few SMS phishing texts they’ve acquired, as proven beneath.
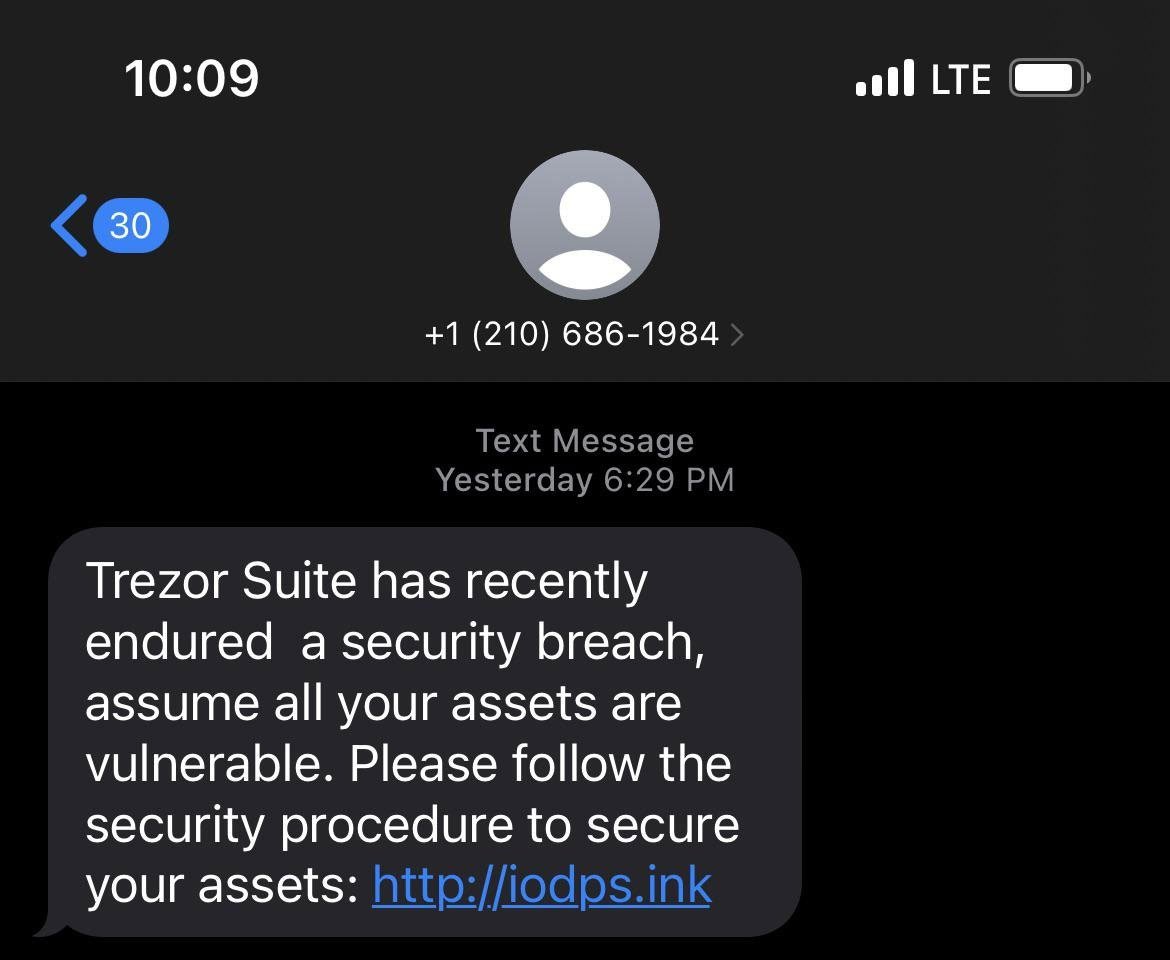
Supply: Mich
When visiting the listed area, guests might be proven a pretend Trezor website that states, “Your belongings may be in danger!” after which prompts you to begin securing your pockets.
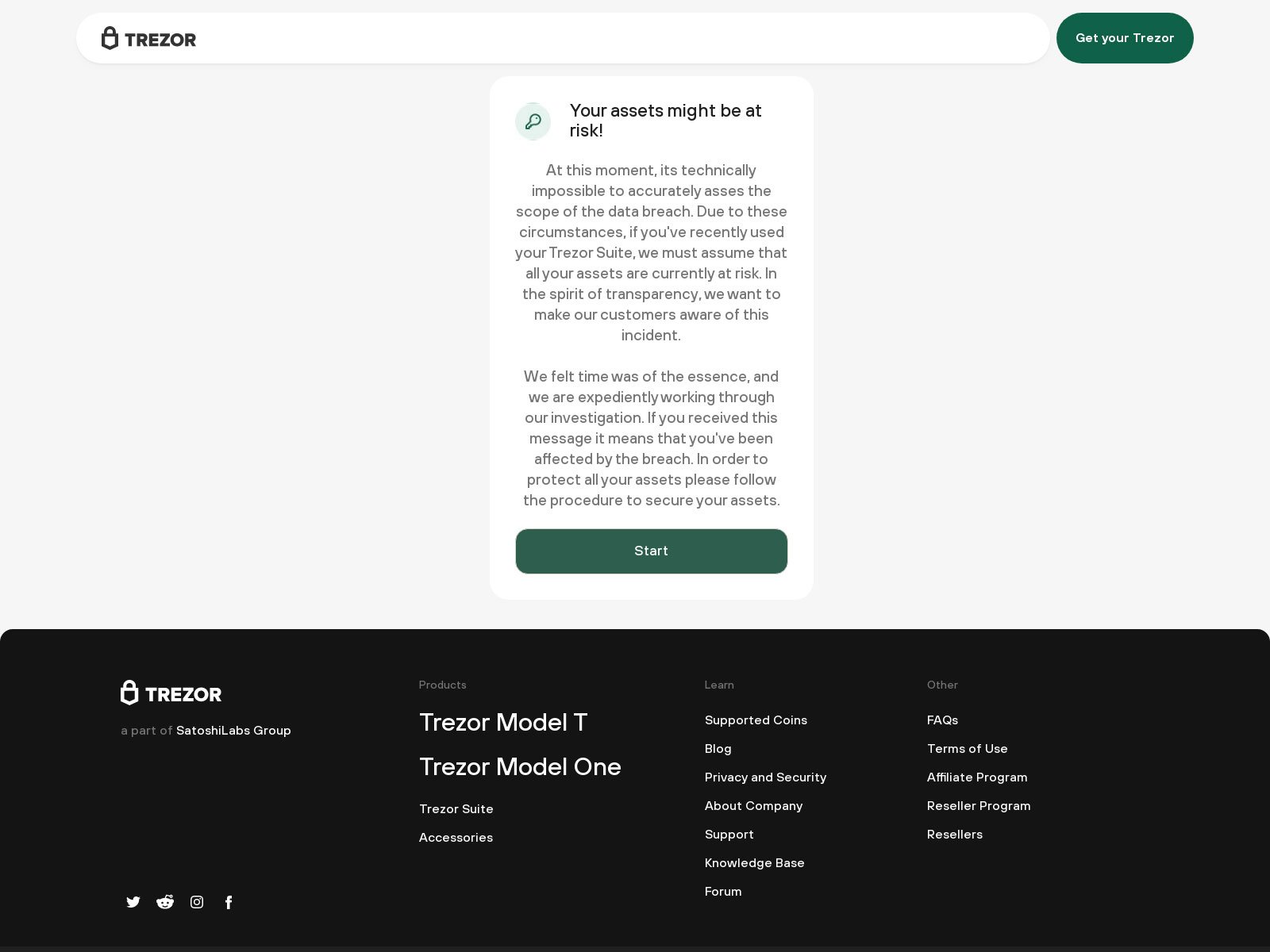
Supply: Urlscan
When customers click on the ‘Begin’ button, they are going to finally be prompted to enter their restoration seed, which the menace actors will then steal.
As soon as a restoration seed is stolen, it’s recreation over for the pockets proprietor, because the menace actors will probably shortly switch any belongings to a different handle underneath their management.
Subsequently, it’s vital to by no means share your pockets’s restoration passwords, seeds, or phrases with anybody else or enter them on any websites.
Trezor is conscious of the phishing marketing campaign and warned customers to watch out for phishing SMS and emails warning of a pretend information breach. The corporate additionally states that they haven’t discovered any proof of a current information breach in its techniques.
“Watch out for the lively phishing rip-off! The attackers contact the victims through telephone name, SMS and/or e mail to say that there is been a safety breach or suspicious exercise on their Trezor account,” tweeted Trezor.
“Please ignore these messages as they aren’t from Trezor.”
“We’ve not discovered any proof of a current database breach. We’ll by no means contact you through calls or SMS.”
Whereas it’s not recognized how the menace actors are focusing on Trezor prospects’ telephone numbers and e mail addresses, it could possibly be via a advertising and marketing listing stolen in a MailChimp breach in March 2022.
MailChimp advised BleepingComputer then that the menace actors stole information from 102 prospects, with most within the cryptocurrency and finance sectors.
The menace actors quickly used Trezor’s advertising and marketing listing to ship a huge wave of pretend information breach notifications in April 2022, resulting in a website internet hosting a pretend Trezor Suite.
When put in, this Trezor Suite would immediate the person to enter their restoration seed, which was then transmitted again to the menace actors.
Whereas the present phishing marketing campaign will not be utilizing pretend software program, the menace actors are nonetheless trying to steal your restoration seed. Subsequently, as we mentioned earlier, and it warrants repeating, by no means share your restoration seed with anybody or on any website.
[ad_2]