[ad_1]

A risk actor has been focusing on authorities entities with PureCrypter malware downloader that has been seen delivering a number of info stealers and ransomware strains.
Researchers at Menlo Safety found that the risk actor used Discord to host the preliminary payload and compromised a non-profit group to retailer extra hosts used within the marketing campaign.
“The marketing campaign was discovered to have delivered a number of varieties of malware together with Redline Stealer, AgentTesla, Eternity, Blackmoon and Philadelphia Ransomware,” the researchers say.
In response to the researchers, the noticed PureCrypter marketing campaign focused a number of authorities group within the Asia-Pacific (APAC) and North America areas.
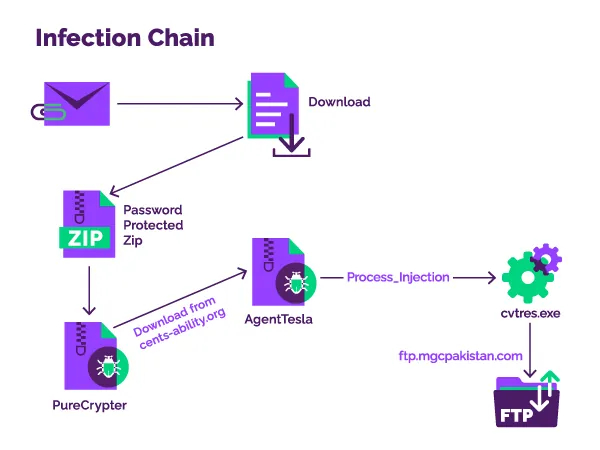
Assault chain
The assault begins with an e-mail that has a Discord app URL pointing to a PureCrypter pattern in a password-protected ZIP archive.
PureCrypter is a .NET-based malware downloader first seen within the wild in March 2021. Its operator rents it to different cybercriminals to distribute numerous varieties of malware.
When executed, it delivers the next-stage payload from a command and management server, which is the compromised server of a non-profit group on this case.
The pattern that the researchers at Menlo Safety analyzed was AgentTesla. When launched, it establishes a connection to a Pakistan-based FTP server that’s used to obtain the stolen information.
The researchers discovered that the risk actors used leaked credentials to take management of the actual FTP server moderately than setting it up their very own, to scale back identification dangers and reduce their hint.
AgentTesla nonetheless in use
AgentTesla is a .NET malware household that has been utilized by cybercriminals for the final eight years. Its utilization peaking in late 2020 and early 2021.
A current report by Cofense highlights that regardless of its age, AgentTesla stays a cheap and highly-capable backdoor that has obtained continuous growth and enchancment through the years.
AgentTesla’s keylogging exercise accounted for roughly one-third of all keylogger stories Cofense Intelligence recorded in 2022.
The malware’s capabilities embody the next:
- Log the sufferer’s keystrokes to seize delicate info akin to passwords.
- Steal passwords saved in internet browsers, e-mail purchasers, or FTP purchasers.
- Seize screenshots of the desktop that would reveal confidential info.
- Intercept information that’s copied to the clipboard, together with texts, passwords, and bank card particulars.
- Exfiltrate stolen information to the C2 through FTP or SMTP.
Within the assaults examined by Menlo Labs, it was found that the risk actors used course of hollowing to inject the AgentTesla payload right into a respectable course of (“cvtres.exe”) to evade detection from antivirus instruments.
Moreover, AgentTesla makes use of XOR encryption to guard its communications with the C2 server, like its configuration recordsdata, from community visitors monitoring instruments.
Menlo Safety believes that the risk actor behind the PureCrypter marketing campaign is just not a serious one however it’s price monitoring its exercise as a result of focusing on authorities entities.
It’s possible that the attacker will preserve utilizing compromised infrastructure for so long as potential earlier than being pressured to search out new one.
[ad_2]