[ad_1]

A brand new info stealer referred to as Stealc has emerged on the darkish internet gaining traction on account of aggressive promotion of stealing capabilities and similarities with malware of the identical form like Vidar, Raccoon, Mars, and Redline.
Safety researchers at cyber menace intelligence firm SEKOIA noticed the brand new pressure in January and observed it began to achieve tractionin early February.
New stealer on the market
Stealc has been marketed on hacking boards by a person referred to as “Plymouth,” who offered the malware as a bit of malware with in depth data-stealing capabilities and an easy-to-use administration panel.
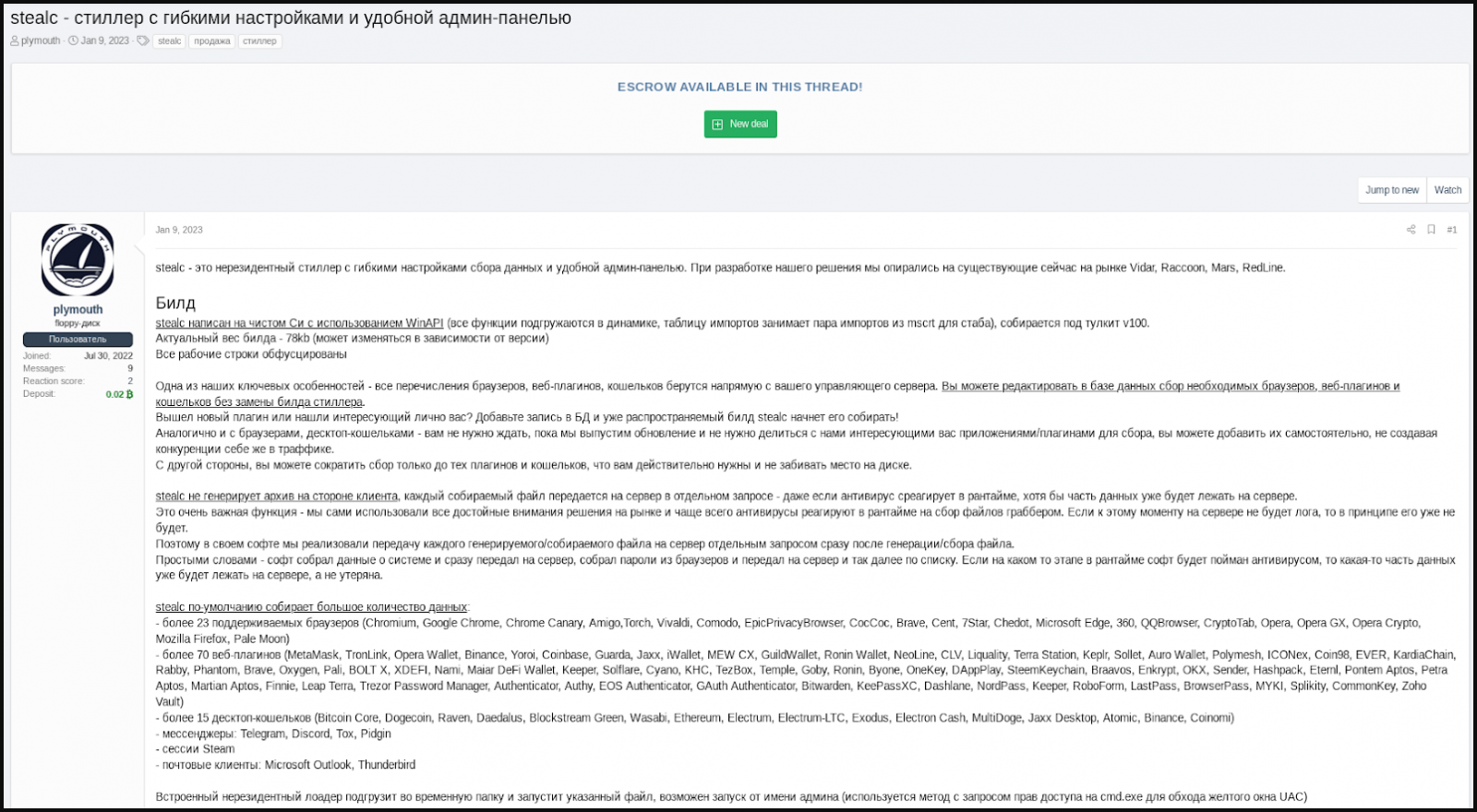
Based on the advertiser, other than the everyday concentrating on of internet browser knowledge, extensions, and cryptocurrency wallets, Stealc additionally has a customizable file grabber that may be set to focus on no matter file varieties the operator needs to steal.
After the preliminary publish, Plymouth began to advertise the malware on different hacking boards and on non-public Telegram channels, providing check samples to potential clients.
The vendor additionally arrange a Telegram channel devoted to publishing Stealc’s new model changelogs, the latest being v1.3.0, launched on February 11, 2023. The malware is actively developed, and a brand new model seems on the channel each week.
Plymouth additionally mentioned that Stealc was not developed from scratch however as an alternative relied on Vidar, Raccoon, Mars and Redline stealers.
One commonality the researchers discovered between Stealc and Vidar, Raccoon and Mars infostealers is that all of them obtain legit third-party DLLs (e.g. sqlite3.dll, nss3.dll) to assist with pilfering delicate knowledge.
In a report at the moment, SEKOIA researchers be aware that the command and management (C2) communications of one of many samples they analyzed shared similarities to these of Vidar and Raccoon information stealers.
The researchers found greater than 40 C2 servers for Stealc and a number of other dozens of samples within the wild, indicating that the brand new malware has attracted the curiosity of the cybercriminal neighborhood.
This recognition could also be accounted by the truth that clients with entry to the administration panel can generate new stealer samples, which improve the probabilities of the malware leaking to a broader viewers.
Regardless of the poor enterprise mannequin, SEKOIA believes that Stealc represents a major menace because it may very well be adopted by much less technical cybercriminals.
Stealc’s capabilities
Stealc has added new options since its first launch in January, together with a system to randomize C2 URLs, a greater logs (stolen recordsdata) looking and sorting system, and an exclusion for victims in Ukraine.
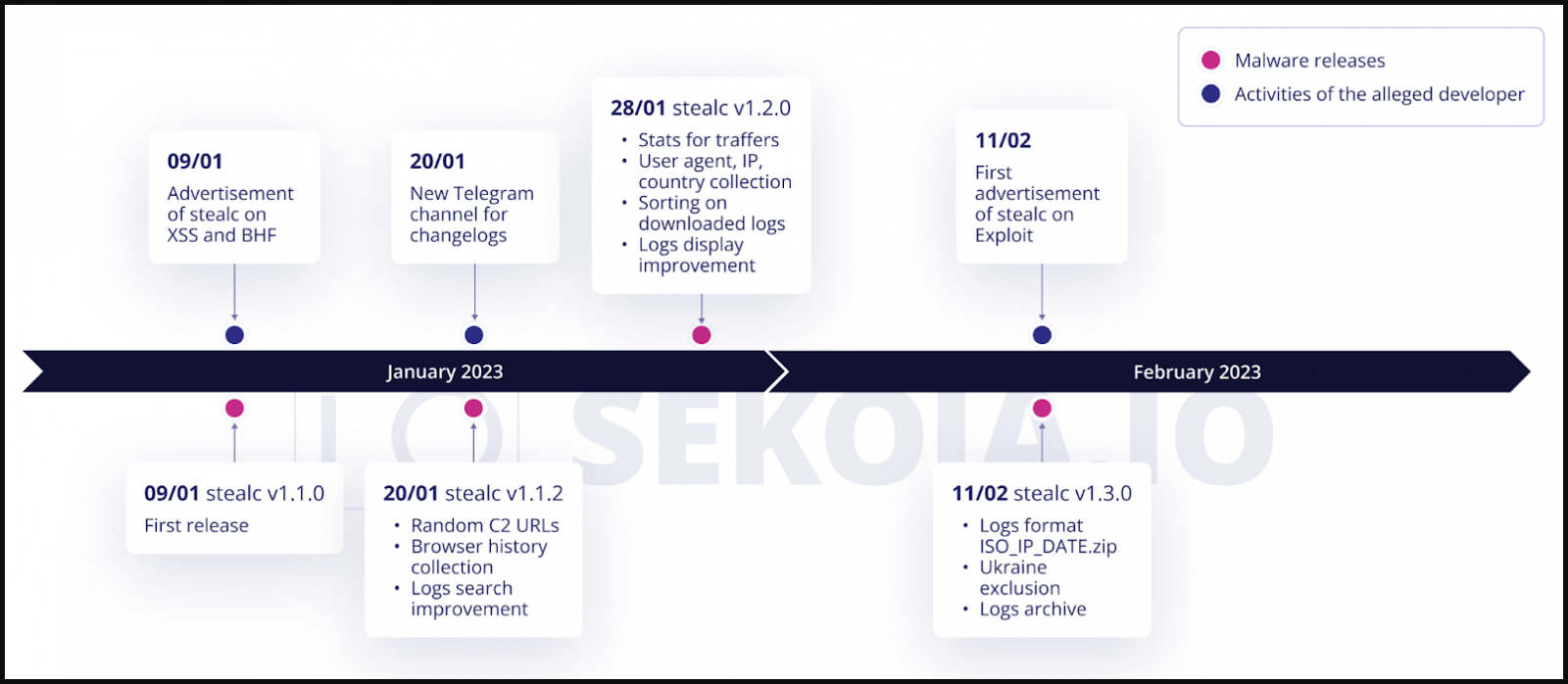
The options that SEKOIA might confirm by analyzing the captured pattern are the next:
- Light-weight construct of solely 80KB
- Use of legit third-party DLLs
- Written in C and abusing Home windows API capabilities
- Most strings are obfuscated with RC4 and base64
- The malware exfiltrates stolen knowledge routinely
- It targets 22 internet browsers, 75 plugins, and 25 desktop wallets
SEKOIA’s curent report doesn’t embrace all the info obtained from reverse engineering Stealc however offers an summary of the primary steps of its execution.
When deployed, the malware deobfuscates its strings and performs anti-analysis checks to make sure it doesn’t run in a digital atmosphere or sandbox.
Subsequent, it dynamically hundreds WinAPI capabilities and initiates communication with the C2 server, sending the sufferer’s {hardware} identifier and construct title within the first message, and receiving a configuration in response.
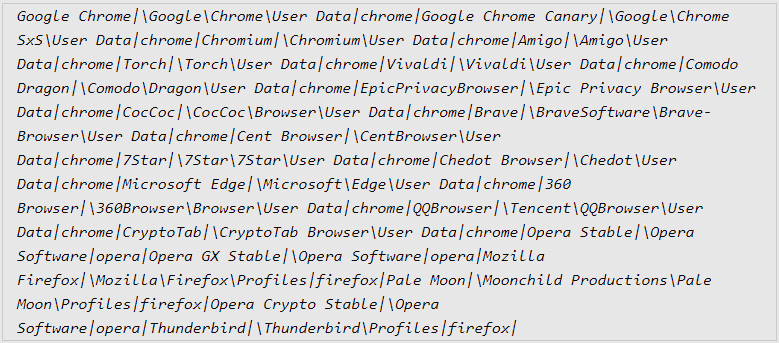
Stealc then collects knowledge from the focused browsers, extensions, and apps, and in addition executes its customized file grabber if energetic, and eventually exfiltrates every part to the C2. As soon as this step is over, the malware removes itself and the downloaded DLL recordsdata from the compromised host to wipe the traces of the an infection.
For the entire checklist of Stealc’s capabilities and focused apps, try the Annex 1 part in SEKOIA’s report.
One distribution methodology the researchers noticed is by way of YouTube movies describing the way to set up cracked software program and linking to a obtain web site.

The researchers say that the software program obtain embeds the Stealc information stealer. As soon as the installer is executed, the malware begins its routine and communicates with its server.
SEKOIA has shared a big set of indicators of compromise that firms can use to defend their digital property in addition to YARA and Suricata guidelines to detect the malware based mostly on decryption routine, particular strings and habits,
Contemplating the noticed distribution methodology, customers are beneficial to steer away from putting in pirated software program and obtain merchandise solely from the official developer’s web site.
[ad_2]