[ad_1]

A brand new Mirai botnet variant tracked as ‘V3G4’ targets 13 vulnerabilities in Linux-based servers and IoT gadgets to make use of in DDoS (distributed denial of service) assaults.
The malware spreads by brute-forcing weak or default telnet/SSH credentials and exploiting hardcoded flaws to carry out distant code execution on the goal gadgets. As soon as a tool is breached, the malware infects the system and recruits it into its botnet swarm.
The actual malware was noticed in three distinct campaigns by researchers at Palo Alto Networks (Unit 42), who reported monitoring the malicious exercise between July 2022 and December 2022.
Unit 42 believes all three assault waves originate from the identical risk actor as a result of the hardcoded C2 domains include the identical string, the shell script downloads are related, and the botnet shoppers utilized in all assaults characteristic similar capabilities.
V3G4 assaults start with the exploitation of one of many following 13 vulnerabilities:
- CVE-2012-4869: FreePBX Elastix distant command execution
- Gitorious distant command execution
- CVE-2014-9727: FRITZ!Field Webcam distant command execution
- Mitel AWC distant command execution
- CVE-2017-5173: Geutebruck IP Cameras distant command execution
- CVE-2019-15107: Webmin command injection
- Spree Commerce arbitrary command execution
- FLIR Thermal Digital camera distant command execution
- CVE-2020-8515: DrayTek Vigor distant command execution
- CVE-2020-15415: DrayTek Vigor distant command execution
- CVE-2022-36267: Airspan AirSpot distant command execution
- CVE-2022-26134: Atlassian Confluence distant command execution
- CVE-2022-4257: C-Information Net Administration System command injection
.png)
After compromising the goal system, a Mirai-based payload is dropped on the system and makes an attempt to hook up with the hardcoded C2 tackle.
The botnet additionally makes an attempt to terminate a set of processes from a hardcoded listing, which incorporates different competing botnet malware households.
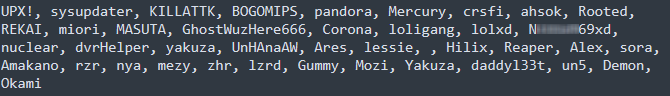
A attribute that differentiates V3G4 from most Mirai variants is that it makes use of 4 totally different XOR encryption keys as a substitute of only one, making reverse engineering the malware’s code and decoding its capabilities tougher.
When spreading to different gadgets, the botnet makes use of a telnet/SSH brute-forcer that tries to attach utilizing default or weak credentials. Unit 42 seen earlier malware variants used each telnet/SSH brute-forcing and vulnerability exploitation for spreading, whereas later samples didn’t use the scanner.
Lastly, compromised gadgets are issued DDoS instructions immediately from the C2, together with TCP, UDP, SYN, and HTTP flooding strategies.
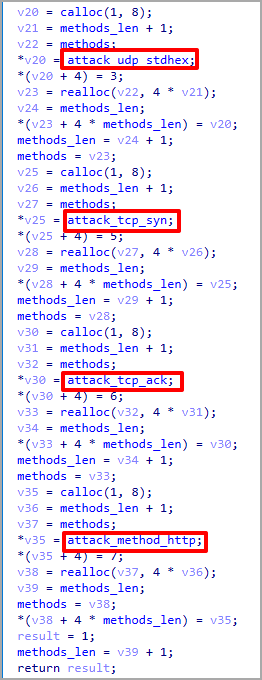
V3G4 seemingly sells DDoS providers to shoppers who need to trigger service disruption to particular web sites or on-line providers.
Nonetheless, this variant has not been tied to a specific service at the moment.
As all the time, one of the simplest ways to guard your gadgets from Mirai-like infections is to vary the default password and set up the most recent safety updates.
[ad_2]