[ad_1]

Admins, internet hosting suppliers, and the French Laptop Emergency Response Group (CERT-FR) warn that attackers actively goal VMware ESXi servers unpatched towards a two-year-old distant code execution vulnerability to deploy ransomware.
Tracked as CVE-2021-21974, the safety flaw is attributable to a heap overflow subject within the OpenSLP service that may be exploited by unauthenticated risk actors in low-complexity assaults.
“As present investigations, these assault campaigns seem like exploiting the vulnerability CVE-2021-21974, for which a patch has been accessible since 23 February 2021,” CERT-FR mentioned.
“The techniques at the moment focused could be ESXi hypervisors in model 6.x and prior to six.7.”
To dam incoming assaults, admins need to disable the weak Service Location Protocol (SLP) service on ESXi hypervisors that have not but been up to date.
CERT-FR strongly recommends making use of the patch as quickly as doable however provides that techniques left unpatched must also be scanned to search for indicators of compromise.
CVE-2021-21974 impacts the next techniques:
- ESXi variations 7.x previous to ESXi70U1c-17325551
- ESXi variations 6.7.x previous to ESXi670-202102401-SG
- ESXi variations 6.5.x previous to ESXi650-202102101-SG
French cloud supplier OVHcloud has additionally printed a report as we speak linking this large wave of assaults concentrating on VMware ESXi servers with the Nevada ransomware operation.
“In line with specialists from the ecosystem in addition to autorities, they is likely to be associated to Nevada ransomware and are utilizing CVE-2021-21974 as compromission vector. Investigation are nonetheless ongoing to substantiate these assumptions,” OVHcloud CISO Julien Levrard mentioned.
“The assault is primarily targetting ESXi servers in model earlier than 7.0 U3i, apparently by way of the OpenSLP port (427).”
No less than 120 VMware ESXi servers worldwide have already been compromised on this ransomware marketing campaign, in accordance with a Shodan search.
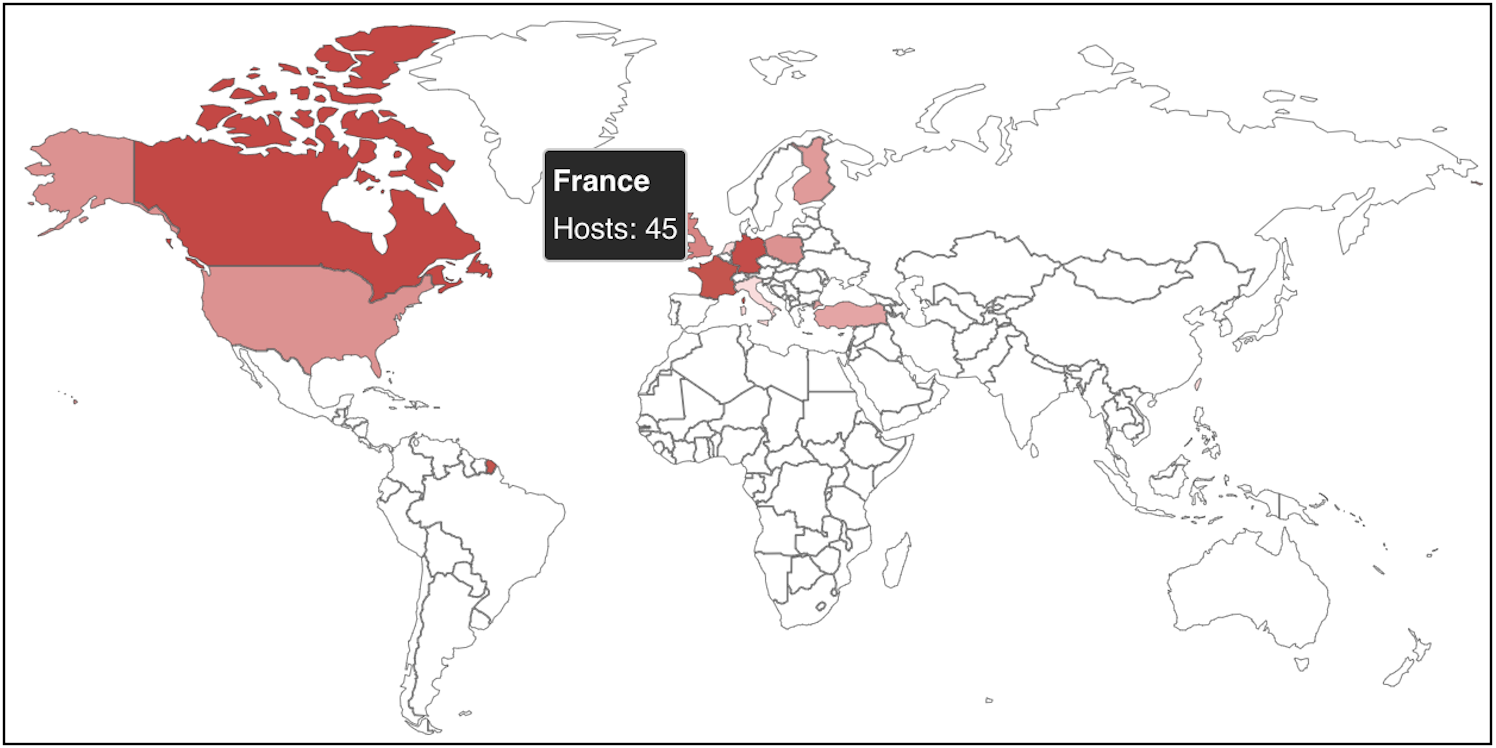
New ESXiArgs ransomware
Nonetheless, from the ransom notes seen on this assault, they don’t seem like associated to the Nevada Ransomware, and seems to be a brand new ransomware household.
Beginning roughly 4 hours in the past, victims impacted by this marketing campaign have additionally begun reporting the assaults on BleepingComputer’s discussion board, asking for assist and extra data on easy methods to get better their information.
The ransomware encrypts information with the .vmxf, .vmx, .vmsd, and .nvram extensions on compromised ESXi servers and creates a .args file for every encrypted doc with metadata (probably wanted for decryption).
Victims have discovered ransom notes named “ransom.html” and “The right way to Restore Your Information.html” on locked techniques. Others mentioned that their notes are plaintext information.
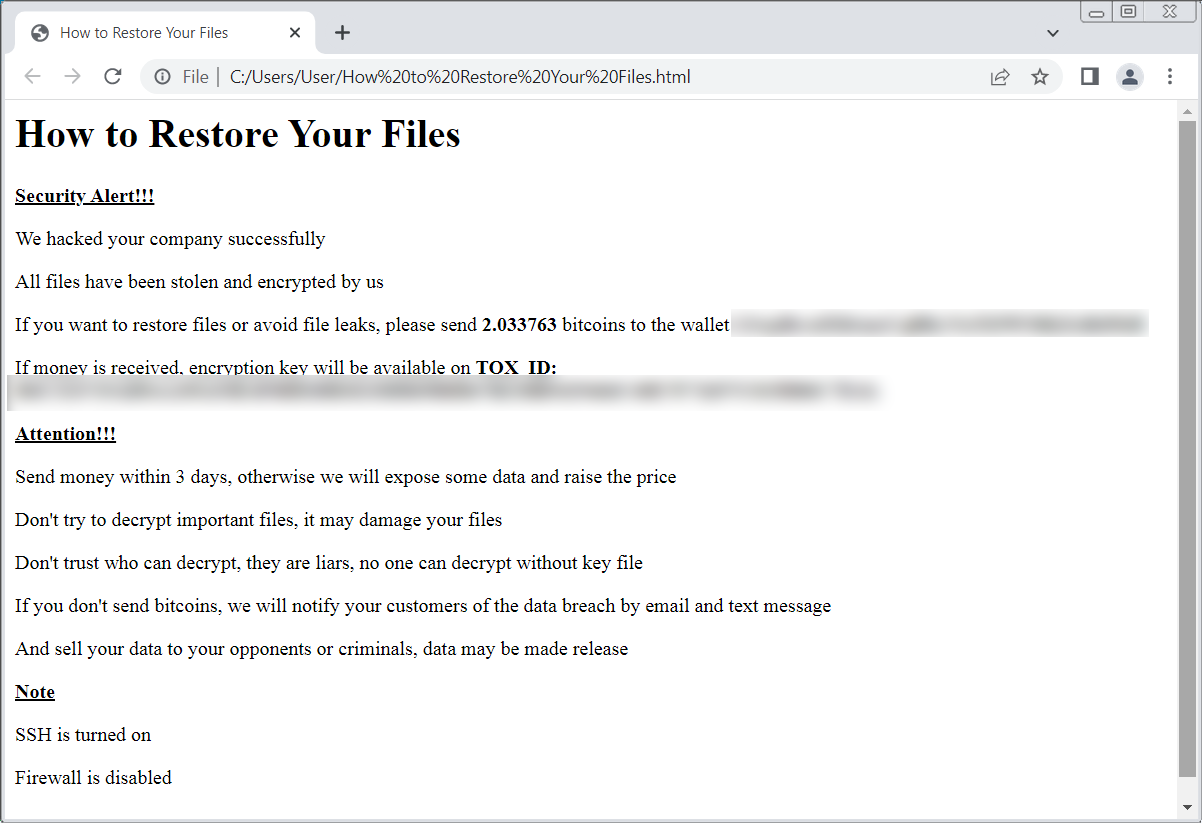
ID Ransomware‘s Michael Gillespie is at the moment monitoring the ransomware underneath the title ‘ESXiArgs,’ however advised BleepingComputer that till we are able to discover a pattern, there is no such thing as a method to decide if it has any weaknesses within the encryption.
BleepingComputer has a devoted help subject the place persons are reporting their experiences with this assault.
When you have new data or a duplicate of the malware, please tell us so researchers can analyze it for weaknesses.
This can be a creating story and will likely be up to date with new information because it turns into accessible …
[ad_2]