[ad_1]

Safety researchers are seeing menace actors switching to a brand new and open-source command and management (C2) framework often known as Havoc as an alternative choice to paid choices equivalent to Cobalt Strike and Brute Ratel.
Amongst its most attention-grabbing capabilities, Havoc is cross-platform and it bypasses Microsoft Defender on up-to-date Home windows 11 gadgets utilizing sleep obfuscation, return tackle stack spoofing, and oblique syscalls.
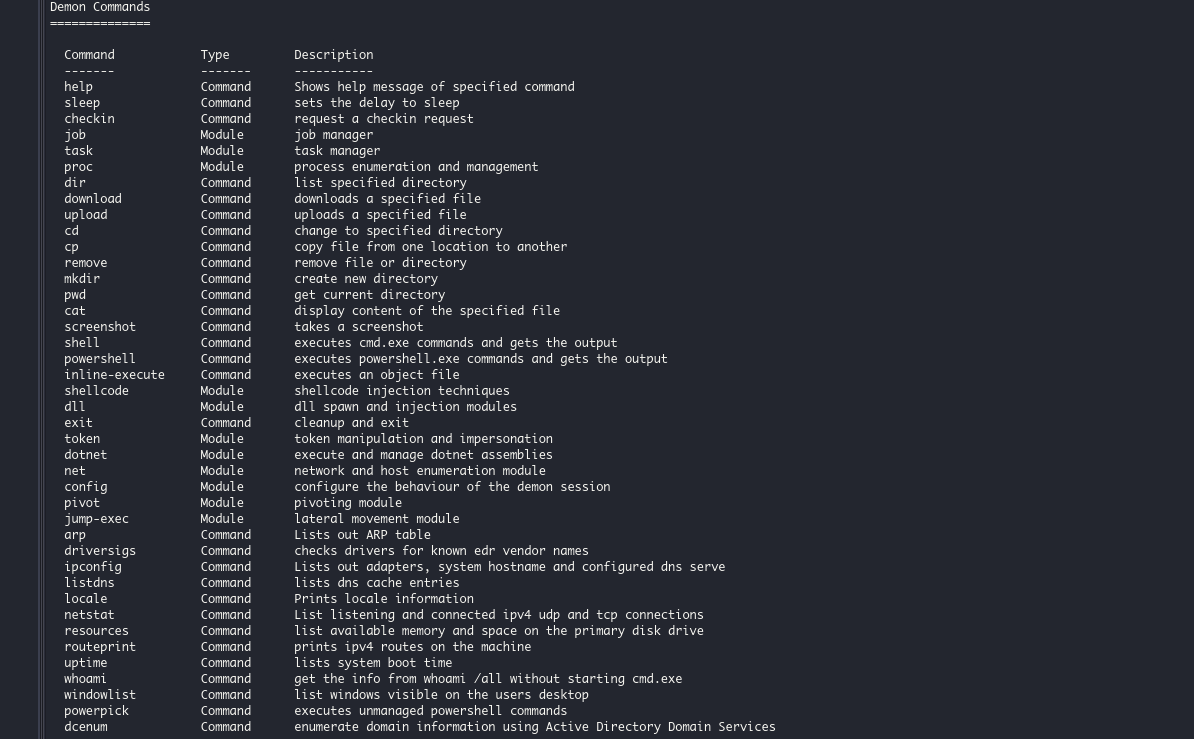
Like different exploitation kits, Havoc consists of all kinds of modules permitting pen testers (and hackers) to carry out numerous duties on exploited gadgets, together with executing instructions, managing processes, downloading further payloads, manipulating Home windows tokens, and executing shellcode.
All of that is finished by means of a web-based administration console, permitting the “attacker” to see all of their compromised gadgets, occasions, and output from duties.
Havoc abused in assaults
An unknown menace group lately deployed this post-exploitation package in early January as a part of an assault marketing campaign concentrating on an undisclosed authorities group.
Because the Zscaler ThreatLabz analysis crew that noticed it within the wild noticed, the shellcode loader dropped on compromised methods will disable the Occasion Tracing for Home windows (ETW) and the ultimate Havoc Demon payload is loaded with out the DOS and NT headers, each to evade detection.
The framework was additionally deployed by way of a malicious npm bundle (Aabquerys) typosquatting authentic module, as revealed in a report from ReversingLabs’ analysis crew earlier this month.
“Demon.bin is a malicious agent with typical RAT (distant entry trojan) functionalities that was generated utilizing an open supply, post-exploitation, command and management framework named Havoc,” ReversingLabs menace researcher Lucija Valentić stated.
“It helps constructing malicious brokers in a number of codecs together with Home windows PE executable, PE DLL and shellcode.”
Extra Cobalt Strike alternate options deployed within the wild
Whereas Cobalt Strike has change into the commonest software utilized by numerous menace actors to drop “beacons” on their victims’ breached networks for later motion and supply of further malicious payloads, a few of them have additionally lately begun in search of alternate options as defenders have gotten higher at detecting and stopping their assaults.
As BleepingComputer beforehand reported, different choices that assist them evade antivirus and Endpoint Detection and Response (EDR) options embody Brute Ratel and Sliver.
These two C2 frameworks have already been discipline examined by a variety of menace teams, from financially motivated cybercrime gangs to state-backed hacking teams.
Brute Ratel, a post-exploitation toolkit developed by Mandiant and CrowdStrike ex-red teamer Chetan Nayak, has been utilized in assaults suspected to be linked to Russian-sponsored hacking group APT29 (aka CozyBear). On the similar time, some Brute Ratel licenses have probably additionally landed within the fingers of ex-Conti ransomware gang members.
In August 2022, Microsoft additionally famous that a number of menace actors, from state-sponsored teams to cybercrime gangs (APT29, FIN12, Bumblebee/Coldtrain), are actually utilizing the Go-based Sliver C2 framework developed by researchers at cybersecurity agency BishopFox of their assaults as an alternative choice to Cobalt Strike.
[ad_2]