[ad_1]

A brand new hacking marketing campaign exploits Sunlogin flaws to deploy the Sliver post-exploitation toolkit and launch Home windows Convey Your Personal Susceptible Driver (BYOVD) assaults to disable safety software program.
Sliver is a post-exploitation toolkit created by Bishop Fox that menace actors started utilizing as a Cobalt Strike various final summer time, using it for community surveillance, command execution, reflective DLL loading, session spawning, course of manipulation, and extra.
Based on a report by the AhnLab Safety Emergency Response Heart (ASEC), not too long ago noticed assaults goal two 2022 vulnerabilities in Sunlogin, a remote-control software program by a Chinese language developer.
After exploiting these vulnerabilities to compromise a tool, the attackers use PowerShell script to open reverse shells, or set up different payloads, comparable to Sliver, Gh0st RAT, or the XMRig Monero coin miner.
Bringing a malicious driver to the assault
The assault begins with exploiting the CNVD-2022-10270 / CNVD-2022-03672 RCE vulnerabilities in Sunlogin v11.0.0.33 and earlier, utilizing available proof of idea (PoC) exploits.
The intruders leverage the flaw to execute an obfuscated PowerShell script to disable safety merchandise earlier than deploying backdoors.
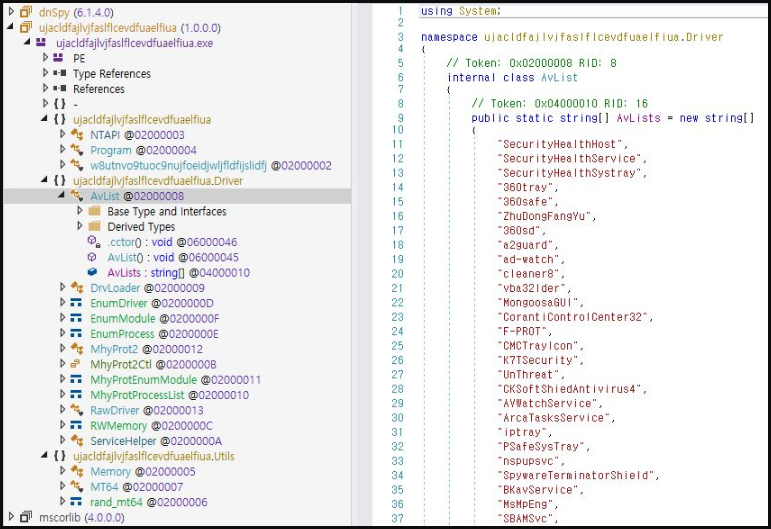
The script decodes a .NET transportable executable and masses it in reminiscence. This executable is a modified model of the Mhyprot2DrvControl open-source software, created to abuse susceptible Home windows drivers to carry out malicious actions with kernel-level privileges.
Mhyprot2DrvControl particularly abuses the mhyprot2.sys file, a digitally signed anti-cheat driver for Genshin Impression that Development Micro noticed getting used for ransomware assaults since final 12 months.
“By way of a easy bypassing course of, the malware can entry the kernel space by mhyprot2.sys,” explains ASEC within the report.
“The developer of Mhyprot2DrvControl supplied a number of options that may be utilized with the privileges escalated by mhyprot2.sys. Amongst these, the menace actor used the characteristic which permits the drive termination of processes to develop a malware that shuts down a number of anti-malware merchandise.”
As soon as the driving force is loaded, the menace actors exploit its vulnerability to achieve Home windows kernel privileges, which may then be used to terminate safety processes protected against user-mode packages.
The second a part of the PowerShell script downloads Powercat from an exterior supply and makes use of it to run a reverse shell that connects to the C2 server, offering the attacker with distant entry to the breached gadget.
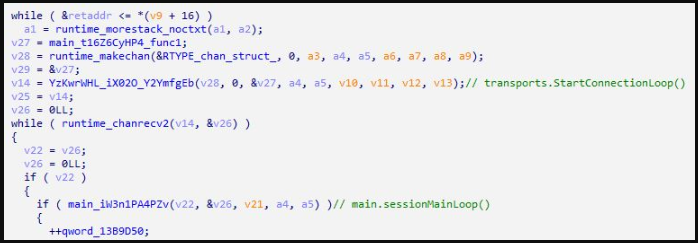
In some circumstances noticed by ASEC, the Sunlogin assaults have been adopted by putting in a Sliver implant (“acl.exe”). The menace actors used the implant generated by the Sliver framework in “Session Mode” with out utilizing any packers.
In different circumstances, the attackers put in the Gh0st RAT (distant entry trojan) for distant file administration, key logging, distant command execution, and information exfiltration capabilities.
Microsoft recommends that Home windows admins allow the susceptible driver blocklist to guard towards BYOVD assaults.
A Microsoft assist article supplies info on enabling the blocklist utilizing the Home windows Reminiscence Integrity characteristic or Home windows Defender Software Management (WDAC).
One other technique to defend towards this assault is to dam the hash of the AV killer, “f71b0c2f7cd766d9bdc1ef35c5ec1743,” and monitor occasion logs for newly put in companies named “mhyprot2.”
[ad_2]