[ad_1]

An ongoing Google advertisements malvertising marketing campaign is spreading malware installers that leverage KoiVM virtualization expertise to evade detection when putting in the Formbook information stealer.
KoiVM is a plugin for the ConfuserEx .NET protector that obfuscates a program’s opcodes in order that the digital machine solely understands them. Then, when launched, the digital machine interprets the opcodes again to their authentic type in order that the applying will be executed.
“Virtualization frameworks resembling KoiVM obfuscate executables by changing the unique code, resembling NET Frequent Intermediate Language (CIL) directions, with virtualized code that solely the virtualization framework understands,” explains a brand new report by SentinelLabs.
“A digital machine engine executes the virtualized code by translating it into the unique code at runtime.”
“When put to malicious use, virtualization makes malware evaluation difficult and in addition represents an try to evade static evaluation mechanisms.”
In a Google promoting marketing campaign noticed by Sentinel Labs, risk actors push the Formbook information-stealing malware as virtualized .NET loaders dubbed ‘MalVirt,’ that assist distribute the ultimate payload with out triggering antivirus alerts.
Sentinel Labs feedback that whereas KoiVM virtualization is fashionable for hacking instruments and cracks, it’s seldom utilized in malware distribution.
As a substitute, the safety agency believes the brand new pattern in its use is likely to be one of many a number of uncomfortable side effects of Microsoft’s disabling of macros in Workplace.
Abusing Google search advertisements
Over the previous month, researchers have seen elevated abuse of Google search advertisements to distribute numerous malware, together with RedLine Stealer, Gozi/Ursnif, Vidar, Rhadamanthys stealer, IcedID, Raccoon Stealer, and lots of extra.
Within the ongoing marketing campaign seen by SentinelLabs, risk actors push the MalVirt loaders in advertisements pretending to be for the Blender 3D software program.
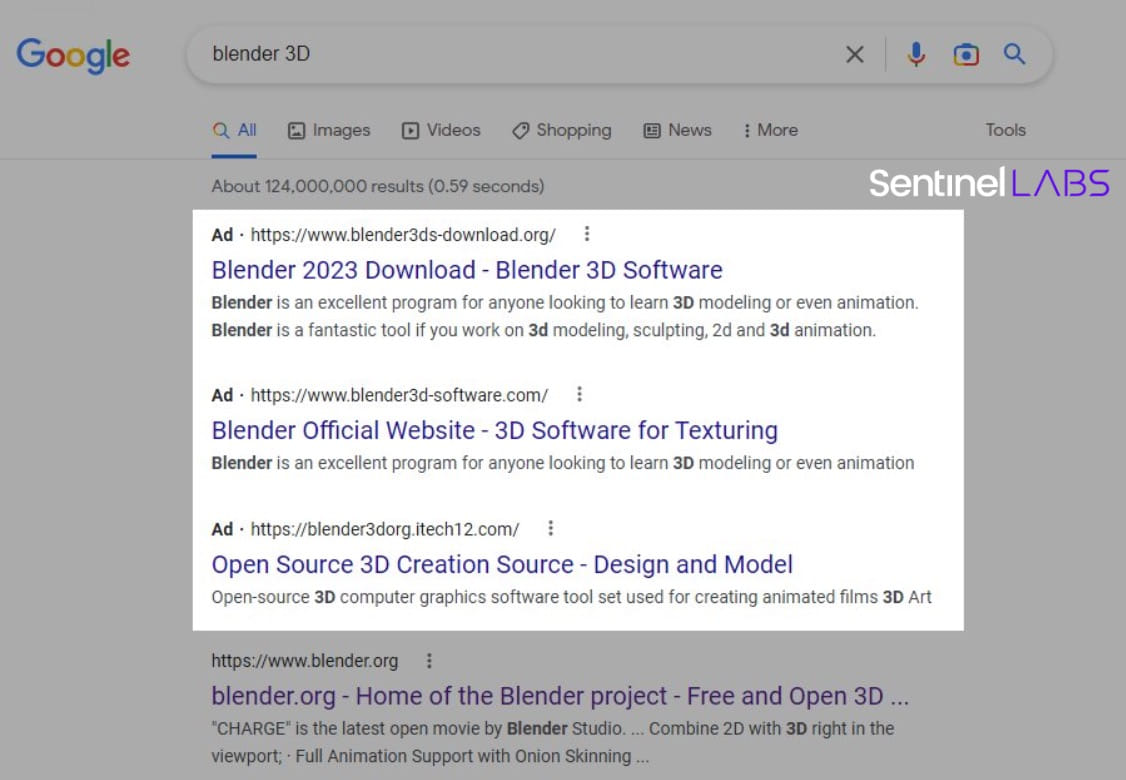
The downloads provided by these pretend websites make the most of invalid digital signatures impersonating Microsoft, Acer, DigiCert, Sectigo, and AVG Applied sciences USA.
Whereas these invalid signatures is not going to trick Home windows into exhibiting them as signed, the MalVirt loaders nonetheless pack options to keep away from detection.
“For instance, some samples patch the AmsiScanBuffer perform applied in amsi.dll to bypass the Anti Malware Scan Interface (AMSI) that detects malicious PowerShell instructions,” explains researcher A. Milenkoski.
“Additional, in an try to evade static detection mechanisms, some strings (resembling amsi.dll and AmsiScanBuffer) are Base-64 encoded and AES-encrypted.”
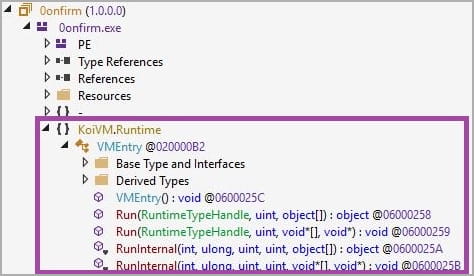
The loaders also can detect in the event that they run in a virtualized setting by querying particular registry keys, and in the event that they do, the execution stops to evade evaluation.
MalVirt additionally makes use of a signed Microsoft Course of Explorer driver loaded at system start-up as “TaskKill,” enabling it to switch working processes to dodge detection.
To additionally evade the decompilation of the virtualized code, the loaders additionally use a modified model of KoiVM that options further obfuscation layers, making its decyphering much more difficult.
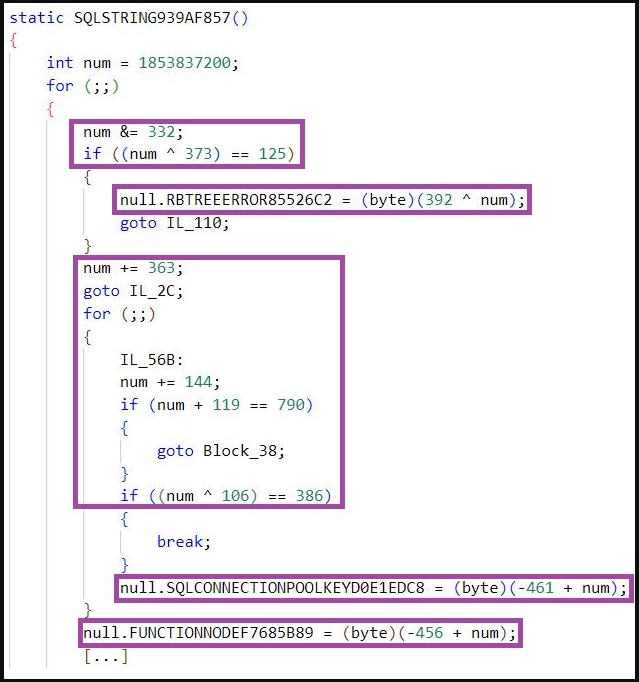
SentinelLabs says this tradition KoiVM implementation confuses normal devirtualization frameworks just like the ‘OldRod’ by obfuscating its routine by way of arithmetic operations as an alternative of utilizing easy assignments.
Milenkoski says it is doable to defeat the obfuscation in these MalVirt loaders and restore the unique order of KoiVM’s 119 fixed variables.
Nevertheless, the extra obfuscation makes it troublesome, requiring hefty guide labor since present automated instruments can not assist.
Hiding the infrastructure
Along with all detection avoidance methods used within the malware loader, a brand new trick is employed by Formbook itself that helps disguise its actual C2 (command and management) visitors and IP addresses.
The information-stealing malware mixes its actual visitors with numerous “smokescreen” HTTP requests whose content material is encrypted and encoded so they do not stand out.
The malware communicates with these IPs randomly, selecting them out of a hardcoded record with domains hosted by numerous firms.
SentinelLabs says that within the samples it analyzed, it noticed Formbook speaking with 17 domains, solely one in all which was the precise C2 server, and the remaining serving as mere decoys to confuse community visitors monitoring instruments.
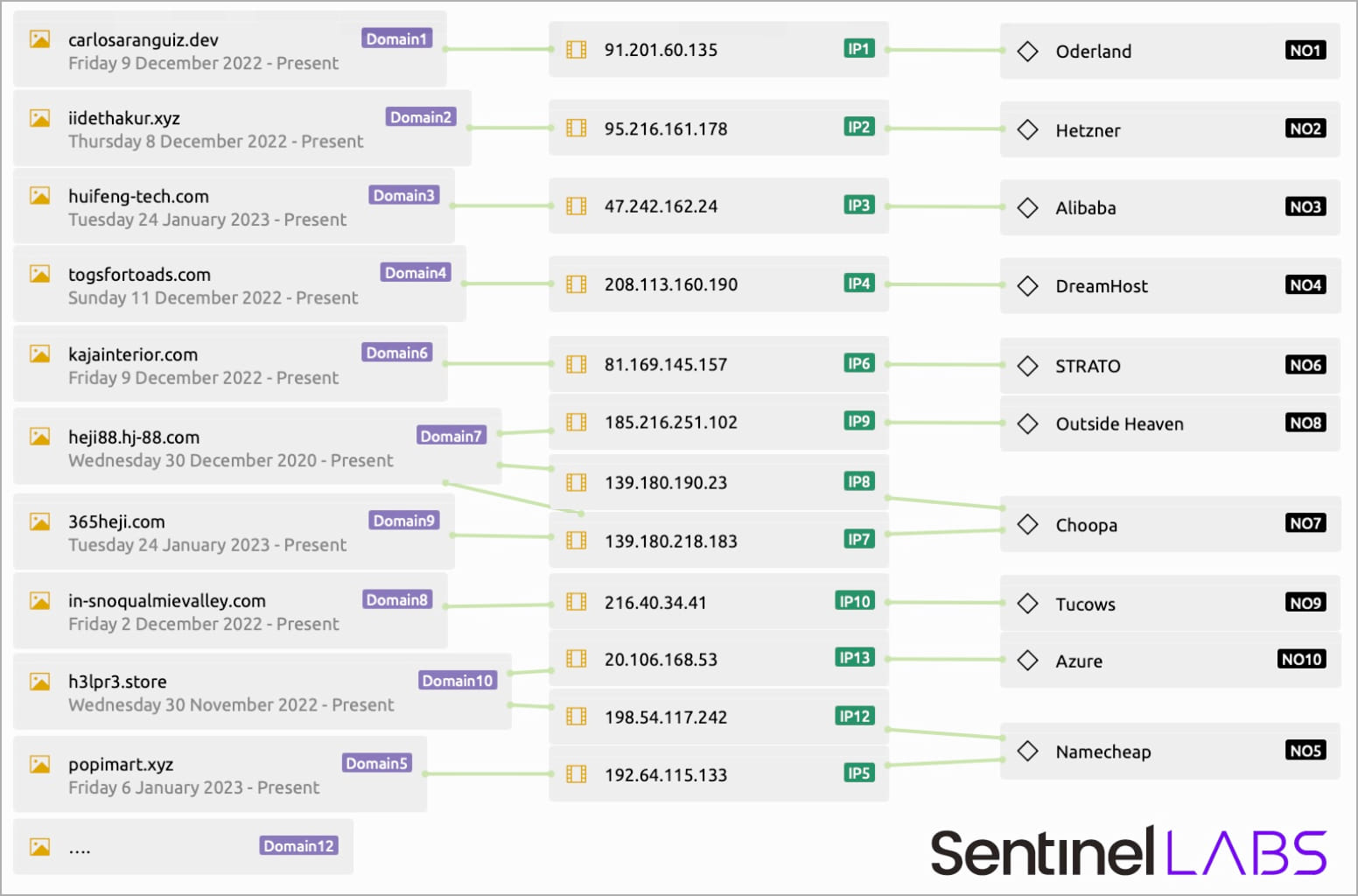
This can be a novel system on a fairly outdated malware pressure, indicating that its operators are curious about empowering it with new options that may make it higher at staying hidden from safety instruments and analysts.
Whether or not or not risk actors have utterly switched malspam distribution of Formbook to Google search commercials stays to be seen, nevertheless it’s one other instance that customers must be very cautious of the hyperlinks they click on in search outcomes.
[ad_2]