[ad_1]

GitHub has rotated its non-public SSH key for GitHub.com after the key was was unintentionally revealed in a public GitHub repository.
The software program growth and model management service says, the non-public RSA key was solely “briefly” uncovered, however that it took motion out of “an abundance of warning.”
Unclear window of publicity
In a succinct weblog put up revealed at present, GitHub acknowledged discovering this week that the RSA SSH non-public key for GitHub.com had been ephemerally uncovered in a public GitHub repository.
“We instantly acted to include the publicity and started investigating to know the basis trigger and influence,” writes Mike Hanley, GitHub’s Chief Safety Officer and SVP of Engineering.
“We’ve now accomplished the important thing substitute, and customers will see the change propagate over the following thirty minutes. Some customers might have seen that the brand new key was briefly current starting round 02:30 UTC throughout preparations for this modification.”
GitHub.com’s newest public key fingerprints are proven beneath. These can be utilized to validate that your SSH connection to GitHub’s servers is certainly safe.
As some might discover, solely GitHub.com’s RSA SSH key has been impacted and changed. No change is required for ECDSA or Ed25519 customers.
SHA256:uNiVztksCsDhcc0u9e8BujQXVUpKZIDTMczCvj3tD2s (RSA)
SHA256:br9IjFspm1vxR3iA35FWE+4VTyz1hYVLIE2t1/CeyWQ (DSA – deprecated)
SHA256:p2QAMXNIC1TJYWeIOttrVc98/R1BUFWu3/LiyKgUfQM (ECDSA)
SHA256:+DiY3wvvV6TuJJhbpZisF/zLDA0zPMSvHdkr4UvCOqU (Ed25519)
“Please be aware that this concern was not the results of a compromise of any GitHub techniques or buyer info,” says GitHub.
“As a substitute, the publicity was the results of what we consider to be an inadvertent publishing of personal info.”
The weblog put up, nonetheless, doesn’t reply when precisely was the important thing uncovered, and for a way lengthy, making the timeline of publicity a bit murky. Such timestamps can usually be ascertained from safety logs—ought to these be accessible, and Git commit historical past.
GitHub additional states it has “no purpose to consider” that the uncovered key was abused, and rotated the important thing “out of an abundance of warning.”
However, rotating a non-public key as soon as it has been leaked, regardless of how ‘briefly,’ is any means a obligatory step to defend customers from adversaries who may doubtlessly impersonate your server, or snoop on a consumer’s connection.
The uncovered RSA key in query doesn’t grant entry to GitHub’s infrastructure or buyer information, Hanley has clarified.
“This variation solely impacts Git operations over SSH utilizing RSA. Net visitors to GitHub.com and HTTPS Git operations aren’t affected.”
Double-check that fingerprint
Though GitHub has modified the non-public SSH keys, a number of docs and software program tasks together with these by GitHub, proceed to make use of the SSH fingerprint of its now-revoked key:
SHA256:nThbg6kXUpJWGl7E1IGOCspRomTxdCARLviKw6E5SY8
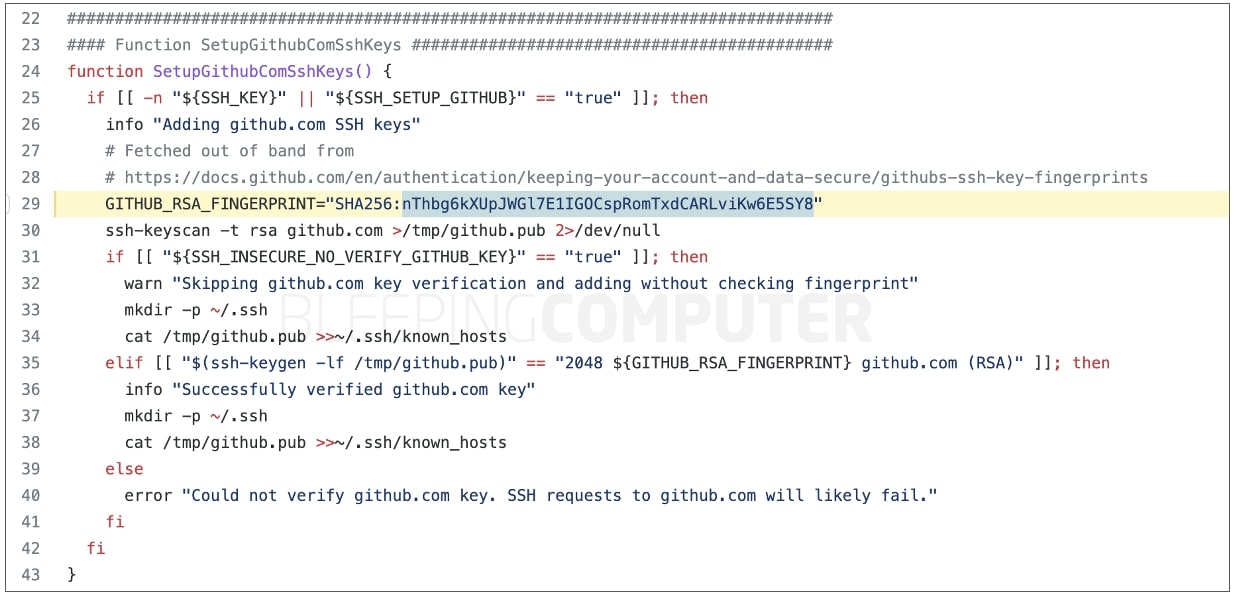
As such, customers ought to replace their ~/.ssh/known_hosts file with GitHub’s new key fingerprint, in any other case they might see safety warnings when making SSH connections. When receiving such warnings, customers ought to make sure the fingerprint seen on their display matches the one for GitHub.com’s newest key.
As of final yr, GitHub’s updated SSH host keys are additionally revealed to its API metadata endpoint.
[ad_2]