[ad_1]

American quick meals chain Chick-fil-A has confirmed that clients’ accounts had been breached in a months-long credential stuffing assault, permitting risk actors to make use of saved rewards balances and entry private data.
In January, BleepingComputer reported that Chick-fil-A had begun investigating what it described as “suspicious exercise” on clients’ accounts.

On the time, Chick-fil-A arrange a help web page with data on what clients ought to do in the event that they detect suspicious exercise on their accounts.
This warning got here after BleepingComputer emailed Chick-fil-A earlier than Christmas about stories of Chick-fil-A person accounts being stolen in credential-stuffing assaults and offered on-line.
These accounts had been offered for costs starting from $2 to $200, relying on the rewards account steadiness and linked fee strategies.
One Telegram channel seen by BleepingComputer confirmed folks buying these accounts after which sharing photos of their purchases made by these accounts.
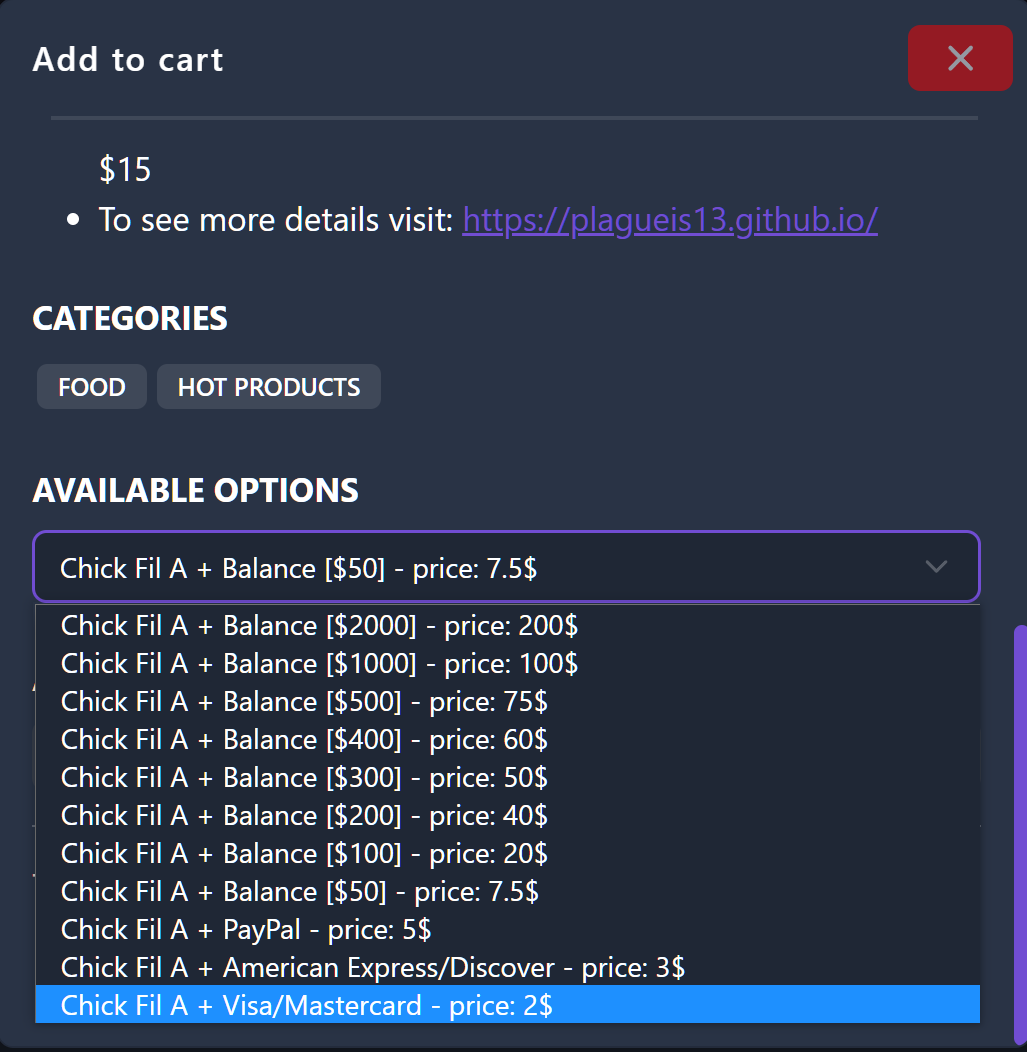
Supply: BleepingComputer
Chick-fil-A confirms credential stuffing assault
At present, Chick-fil-A confirmed our reporting in a safety discover submitted to the California Lawyer Basic’s Workplace, stating that they suffered a credential stuffing assault between December 18th, 2022, and February twelfth, 2023.
“Following a cautious investigation, we decided that unauthorized events launched an automatic assault in opposition to our web site and cellular software between December 18, 2022 and February 12, 2023 utilizing account credentials (e.g., e mail addresses and passwords) obtained from a third-party supply.
Based mostly on our investigation, we decided on February 12, 2023 that the unauthorized events subsequently accessed data in your Chick-fil-A One account.” – Chick-fil-A notification.
The quick meals chain is warning impacted clients that risk actors who accessed their account would have additionally had entry to their private data, together with their title, e mail deal with, Chick-fil-A One membership quantity and cellular pay quantity, QR code, masked credit score/debit card quantity, and the quantity of Chick-fil-A credit score (e.g., e-gift card steadiness) in your account (if any).
For some clients, the data might have included birthdays, cellphone numbers, bodily addresses, and the final 4 digits of bank cards.
In response to the assault, Chick-fil-A pressured clients to reset passwords, froze funds loaded into accounts, and eliminated any saved fee data from accounts.
Chick-fil-A additionally states that they restored Chick-fil-A One account balances and added rewards to impacted accounts as a manner of apologizing.
Because the accounts had been breached utilizing credentials uncovered in different knowledge breaches, impacted customers should change their passwords in any respect websites they frequent, particularly in the event that they use the identical Chick-fil-A password.
When resetting passwords, use a novel password for every web site and retailer them in a password supervisor, like Bitwarden, in order that they are often simply managed.
Whereas there is no such thing as a proof that private data was abused, impacted clients must also be looking out for doubtlessly focused phishing emails using this data.
[ad_2]