[ad_1]
Apple lately up to date XProtect, the software program constructed into macOS that protects the working system from viruses and malware. The replace, model 2166, was issued on February 22, and was put in robotically, which is the same old technique for XProtect.
A current weblog put up by Howard Oakley factors out the brand new model, and though Apple doesn’t subject safety notes in regards to the replace, Oakley says that XProtect was up to date with new Yara definitions for 2 exploits, MACOS.KEYSTEAL.A and HONKBOX_A, B, and C. Oakley additionally says that Apple normally obfuscates the identities of the exploits in its definitions, however this time Apple used their acknowledged names.
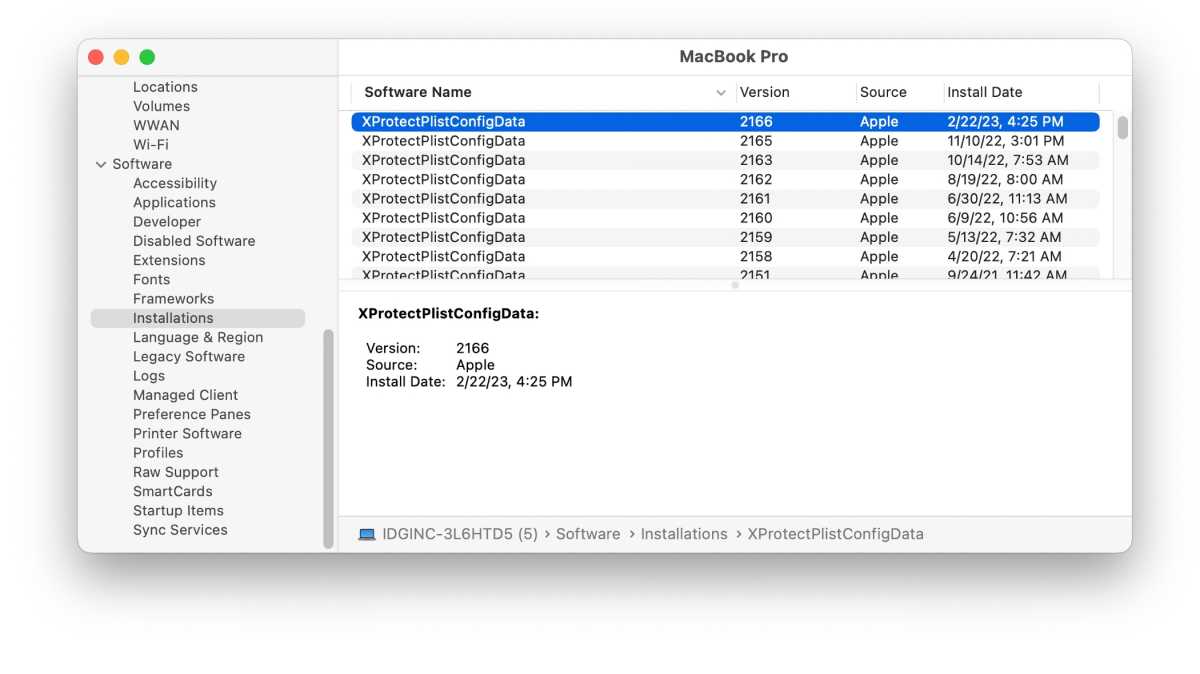
To see if the replace was put in in your Mac, you need to use the System Data app that’s positioned in Purposes > Utilities. When you launch the app, search for the Software program part within the left column, and click on on Installations. In the primary part of the window, an inventory will seem, and if it’s sorted by Software program Title, you may click on the header to reverse the checklist (or scroll to the underside) to see the entry for “XProtectPlistConfigData”. The replace is model 2166, and is obtainable for variations of macOS beginning with El Capitan.
Foundry
The replace ought to set up robotically, purchase you may drive the set up by utilizing one of many utilities Oakley has created: SilentKnight, which checks if macOS’s safety has been up to date, or LockRattler, which checks if macOS’s fundamental safety features are working. These free utilities will be downloaded from Oakley’s web site.
Be sure you try Oakley’s weblog, which is a terrific mixture of Mac technical articles and posts about portray. Oakley is a longtime Mac developer who has written a number of nice Mac utilities.
[ad_2]