[ad_1]

Safety researchers have seen that the operators of the ChromeLoader browser hijacking and adware marketing campaign are actually utilizing VHD recordsdata named after well-liked video games. Beforehand, such campaigns relied on ISO-based distribution.
The malicious recordsdata had been found by member of the Ahnlab Safety Emergency Response Middle (ASEC) by way of Google search outcomes to queries for well-liked video games
Among the many sport titles abused for adware distribution functions are Elden Ring, ROBLOX, Darkish Souls 3, Purple Lifeless Redemption 2, Want for Pace, Name of Responsibility, Portal 2, Minecraft, Legend of Zelda, Pokemon, Mario Kart, Animal Crossing, and extra.
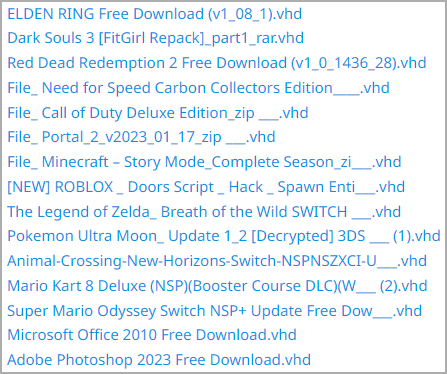
A community of malvertising websites distributes the malicious recordsdata, which seem as respectable game-related packages, that set up the ChromeLoader extension.
ChromeLoader hijacks the browser searches to point out commercials. Itt additionally modifies the browser settings, and collects credentials and browser information.
In accordance with Purple Canary information, the malware bacame extra prevalent in Might 2022. In September 2022, VMware reported new variants carying out extra refined community actions. In some instances the actor even delivered the Enigma ransomware.
In all instances seen all through 2022, ChromeLoader arrived on the goal system as an ISO file. Recently, the operators seem to desire the VHD packaging.
VHD recordsdata may be simply mounted on on a Home windows system and are supported by a number of virtualization software program.
The photographs embrace a number of recordsdata however solely considered one of them, a shortcut known as “Set up.lnk,” is seen. Deploying the shortcut triggers the execution of a batch script that decompresses the content material of a ZIP archive.
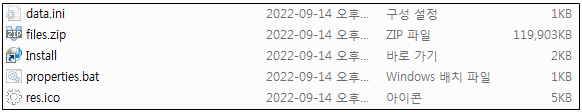
Within the subsequent step, the batch file executes “information.ini,” a VBScript, and a JavaScript that fetches the ultimate payload from a distant useful resource.
In accordance with ASEC, ChromeLoader will begin redirecting to commercial websites, thus producing income for its operators.
The researchers say that the addresses internet hosting the payload usually are not longe accessible. They notice that the malicious Chrome extension that ChromeLoader creates and executes may accumulate credential information saved within the browser.
ASEC’s report offers a brief set of indicators of compromise that may assist detect the ChromeLoader risk.
Customers are suggested to keep away from downloading video games from unofficial sources, and steer clear of cracks for well-liked merchandise as they sometimes have a excessive safety threat.
[ad_2]