[ad_1]

VMware has launched a vital safety improve to handle a vital injection vulnerability that impacts a number of variations of Carbon Black App Management for Home windows.
The corporate warns that the severity ranking of the safety situation is 9.1 out of 10 and that an attacker can leverage it to realize entry to the underlying working system.
Carbon Black App Management is a collection designed to assist giant organizations be sure that its vital endpoints run solely trusted and accepted software program.
Tracked as CVE-2023-20858, the problem was found by safety analyst Jari Jääskelä and will enable a risk actor with privileged entry to the App Management administration console to get entry to the working system utilizing specifically crafted enter.
“A malicious actor with privileged entry to the App Management administration console could possibly use specifically crafted enter permitting entry to the underlying server working system,” reads VMware’s advisory.
Injection flaws enable attackers to execute instructions or code within the goal app. They’ll result in full compromise of backend methods and all purchasers that hook up with the weak utility.
VMware strongly recommends directors to “improve as quickly as attainable” to a protected model of the product.
CVE-2023-20858 impacts VMware Carbon Black App Management for Home windows model 8.7.7 and older, model 8.8.5 and older, and model 8.9.3 and older. Directors are really helpful to improve to variations 8.9.4, 8.8.6, and 8.7.8 or later.
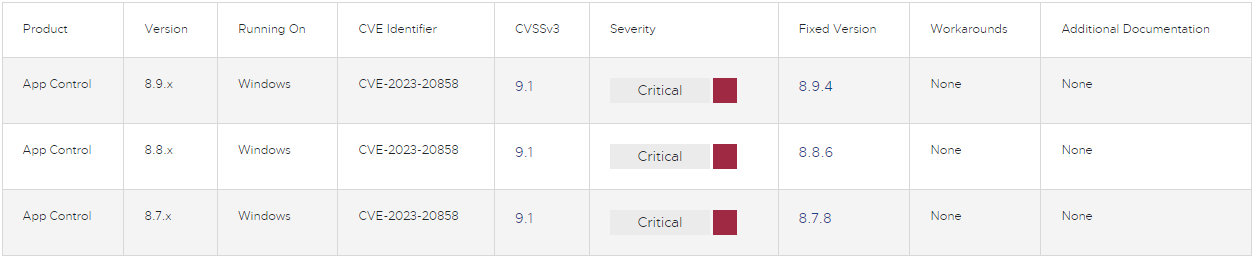
VMware’s safety advisory has shared no workarounds or mitigation recommendation, so the one protected possibility is to maneuver to the really helpful variations.
On Tuesday, VMware additionally patched CVE-2023-20855, a high-severity (CVSS v3: 8.8) XXE (XML exterior entity) injection flaw that would allow an attacker to bypass XML parsing restrictions to entry delicate data or carry out privilege escalation.
CVE-2023-20855 impacts VMware Orchestrator beneath v8.11.1 (fastened model), vRealize Automation beneath v8.11.1 (fastened model), and VMware Cloud Basis 4.x (fastened in KB90926).
[ad_2]