[ad_1]

An ongoing malware marketing campaign targets YouTube and Fb customers, infecting their computer systems with a brand new data stealer that can hijack their social media accounts and use their units to mine for cryptocurrency.
Safety researchers with Bitdefender’s Superior Risk Management (ATC) crew found the brand new malware and dubbed it S1deload Stealer resulting from its intensive use of DLL sideloading for evading detection.
“Between July and December 2022, Bitdefender merchandise detected greater than 600 distinctive customers contaminated with this malware,” Bitdefender researcher Dávid Ács mentioned.
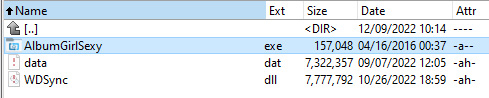
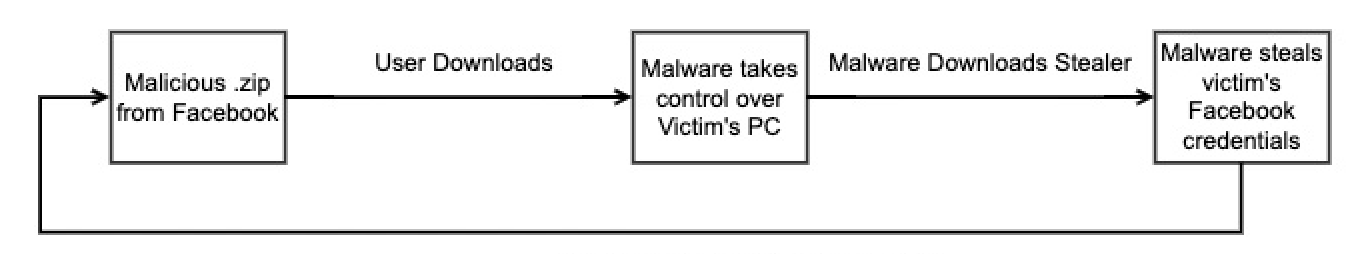
Victims are tricked into infecting themselves utilizing social engineering and feedback on FaceBook pages that push archives with grownup themes (e.g., AlbumGirlSexy.zip, HDSexyGirl.zip, SexyGirlAlbum.zip, and extra).
If the person downloads one of many linked archives, they are going to as an alternative get an executable signed with a sound Western Digital digital signature and a malicious DLL (WDSync.dll) containing the ultimate payload.
As soon as put in on victims’ units, S1deload Stealer could be instructed by its operators to carry out one in all a number of duties after connecting to the command-and-control (C2) server.
As Bitdefender found, it might probably obtain and run extra elements, together with a headless Chrome net browser that runs within the background and emulates human habits to artificially enhance view counts on YouTube movies and Fb posts.
On different programs, it might probably additionally deploy a stealer that decrypts and exfiltrates saved credentials and cookies from the sufferer’s browser and the Login Knowledge SQLite database or a cryptojacker that can mine BEAM cryptocurrency.
If it manages to steal a Fb account, the malware will even try to estimate its precise worth by leveraging the Fb Graph API to seek out out if the sufferer is the admin of a Fb web page or group, if it pays for adverts, or is linked to a enterprise supervisor account.
“The stealer part we noticed within the wild steals the saved credentials from the sufferer’s browser, exfiltrating them to the malware creator’s server,” Ács added.
“The malware creator makes use of the newly obtained credentials to spam on social media and infect extra machines, making a suggestions loop.”
To keep away from getting contaminated and having your social media accounts hijacked, it is best to by no means run executables from unknown sources and all the time preserve your anti-malware software program updated.
Indicators of compromise (IOCs) and YARA guidelines linked to this malware marketing campaign can be found on the finish of Bitdefender’s whitepaper (PDF).
Risk intelligence firm SEKOIA additionally noticed a new data stealer pressure generally known as Stealc and marketed on the darkish net and hacking boards as that includes an easy-to-use administration panel and intensive data-stealing capabilities.
In contrast to S1deload Stealer, the Stealc malware is distributed by way of pretend cracked software program, a extremely widespread tactic additionally used to push different information stealers like Vidar, Redline, Raccoon, and Mars.
[ad_2]