[ad_1]

North Korean hackers have discovered a approach round U.S.-imposed sanctions to launder the cryptocurrency proceeds from their heists, in response to proof found by blockchain analysts.
The Lazarus Group, because the risk actor is usually referred to, has laundered about $100 million in stolen Bitcoin since October 2022 by a single crypto-mixing service referred to as Sinbad.
Lazarus behind main crypto heists
Final 12 months, the U.S. Treasury’s Workplace of International Property Management (OFAC) introduced sanctions towards the cryptocurrency mixing providers Blender and Twister Money, which Lazarus had used to launder near $500 million in illicitly obtained cryptocurrency.
The measure was taken after greater than $600 million in crypto property have been stolen from Axie Infinity’s cross-chain bridge in a hack later attributed to the North Korean Lazarus group.
Hackers usually use cryptocurrency mixers/tumblers as a result of, for a charge, they permit hiding the origin and homeowners of the funds by mixing the property of a bigger variety of customers.
supply: Elliptic
Whereas the OFAC sanctions didn’t cease Twister Money, they put a cease to Blender, whose operator disappeared after reportedly taking from the mixer nearly $22 million in Bitcoin.
In line with blockchain evaluation firm Elliptic, Blender’s operator very doubtless began in early October 2022 a brand new service referred to as Sinbad, which is being utilized by Lazarus to launder property.
Switching to new mixer
Tom Robinson, Elliptic co-founder and chief scientist, instructed BleepingComputer that the connection emerged after the Concord Horizon crypt heist in June 2022 that result in about $100 million in losses.
Quickly after the hack, Elliptic discovered sturdy hyperlinks to Lazarus, one thing that the FBI confirmed earlier this 12 months, by following the funds by the Twister Money mixing service.
Usually, the actor mixed Twister Money crypto mixing with a custodial-based service, like Blender. This time although, they used one other Bitcoin mixer referred to as Sinbad.
supply: BleepingComputer
Robinson says that though the Sinbad service is “comparatively small,” it has been used to launder the funds stolen by the Lazarus group.
“Tens of thousands and thousands of {dollars} from Horizon and different North Korea-linked hacks have been handed by Sinbad thus far and proceed to take action, demonstrating confidence and belief within the new mixer” – Elliptic
Sturdy hyperlinks between Blender and Sinbad mixers
Not like Twister Money, each Blender and Sinbad are custodial mixers, that means that each one cryptocurrency that goes into the service is underneath the management of the operator; so homeowners have adequate confidence to surrender command of their funds.
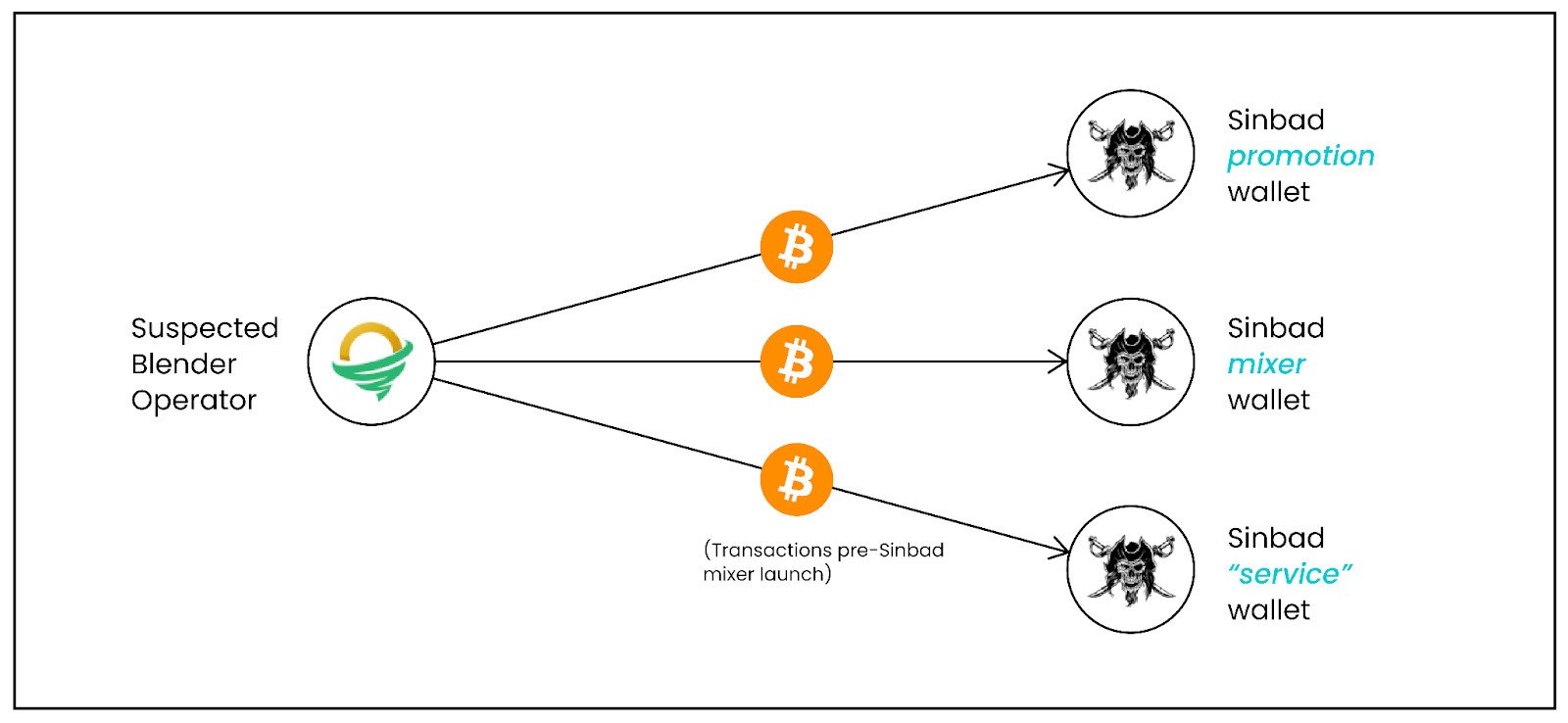
Elliptic’s evaluation reveals with excessive confidence that Sinbad is operated by the identical particular person or group that was behind Blender.
The researchers discovered {that a} “service” tackle on the Sinbad web site acquired Bitcoin from a pockets believed to belong to the operator of Blender.
The identical pockets was used to pay for selling the brand new crypto mixer and to fund nearly all preliminary transactions coming to Sinbad, about $22 million.
supply: Elliptic
Other than the pockets, the researchers additionally observed an analogous on-chain sample conduct for each mixers, which incorporates particular traits of transactions.
“The way in which wherein the Sinbad mixer operates is equivalent to Blender in a number of methods, together with ten-digit mixer codes, assure letters signed by the service tackle, and a most seven-day transaction delay” – Elliptic
Different commonalities the researchers noticed embody sturdy similarities within the web sites, use of naming conventions, language, and “a transparent nexus to Russia, with Russian-language help and web sites.”
Though known as one group, Lazarus defines a number of North Korean operators tasked by the federal government with gathering intelligence in addition to stealing cash to help national-level priorities and aims.
Moreover focusing on cryptocurrency exchanges, North Korean risk actors additionally engaged in ransomware assaults utilizing a number of locker strains towards well being sector organizations within the U.S. and South Korea.
[ad_2]