[ad_1]

A brand new phishing marketing campaign focusing on Amazon Internet Providers (AWS) logins is abusing Google adverts to sneak phishing websites into Google Search to steal your login credentials.
The marketing campaign was found by Sentinel Labs, whose analysts noticed the malicious search outcomes on January 30, 2023. The dangerous adverts ranked second when trying to find “aws,” proper behind Amazon’s personal promoted search consequence.
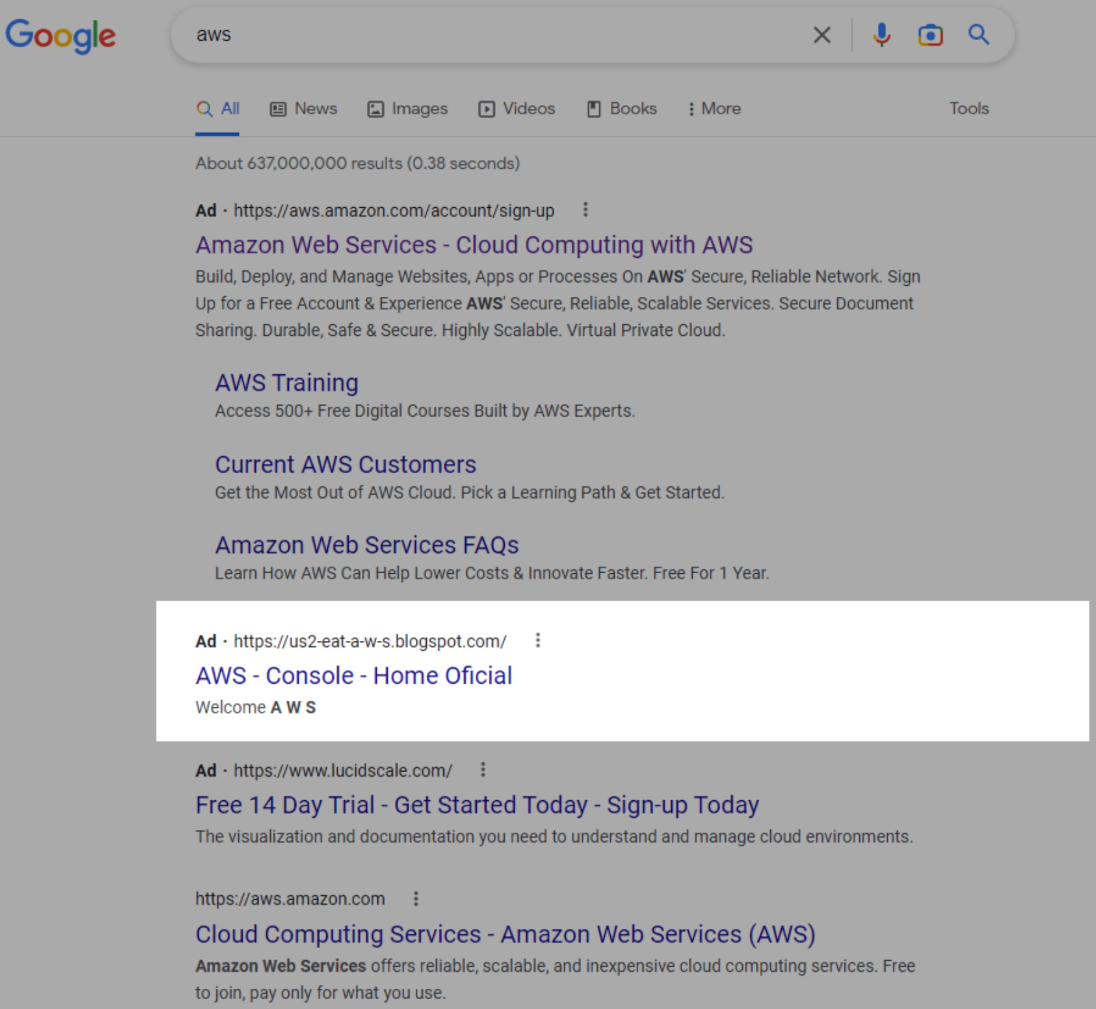
Initially, the risk actors linked the advert on to the phishing web page. Nonetheless, at a later section, they added a redirection step, more likely to evade detection by Google’s advert fraud detection methods.
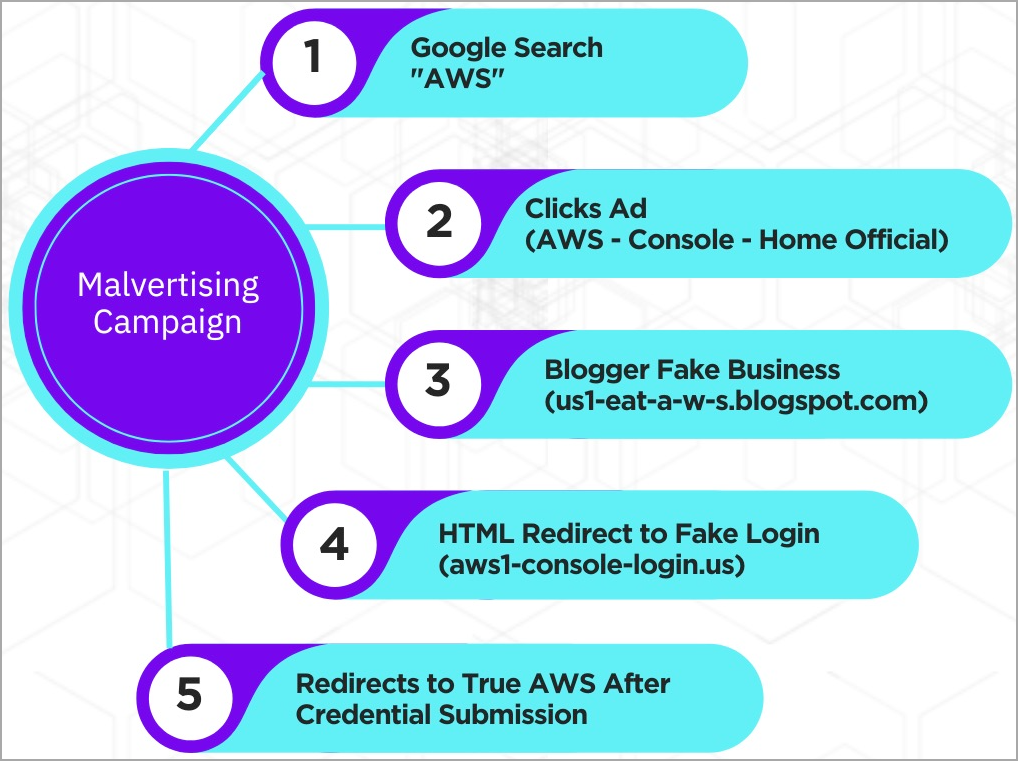
The malicious Google adverts take the sufferer to a blogger web site (“us1-eat-a-w-s.blogspot[.]com”) beneath the attackers’ management, which is a duplicate of a reliable vegan meals weblog.
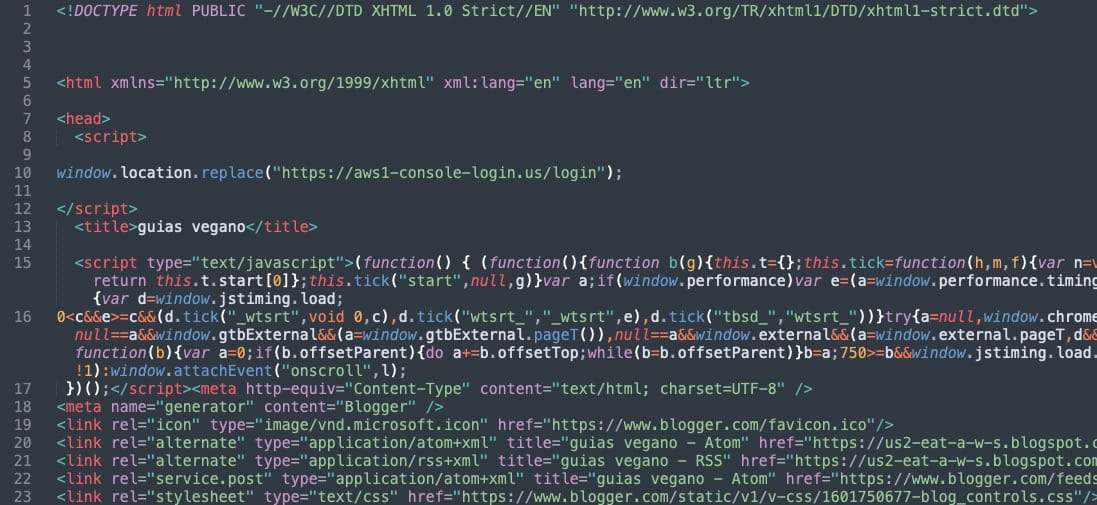
The location makes use of ‘window.location.substitute’ to routinely redirect the sufferer to a brand new web site that hosts the faux AWS login web page, made to look genuine.
The sufferer is prompted to pick out if they’re a root or IAM person after which enter their electronic mail handle and password. This feature helps the risk actors categorize the stolen knowledge into two classes of worth and utility.
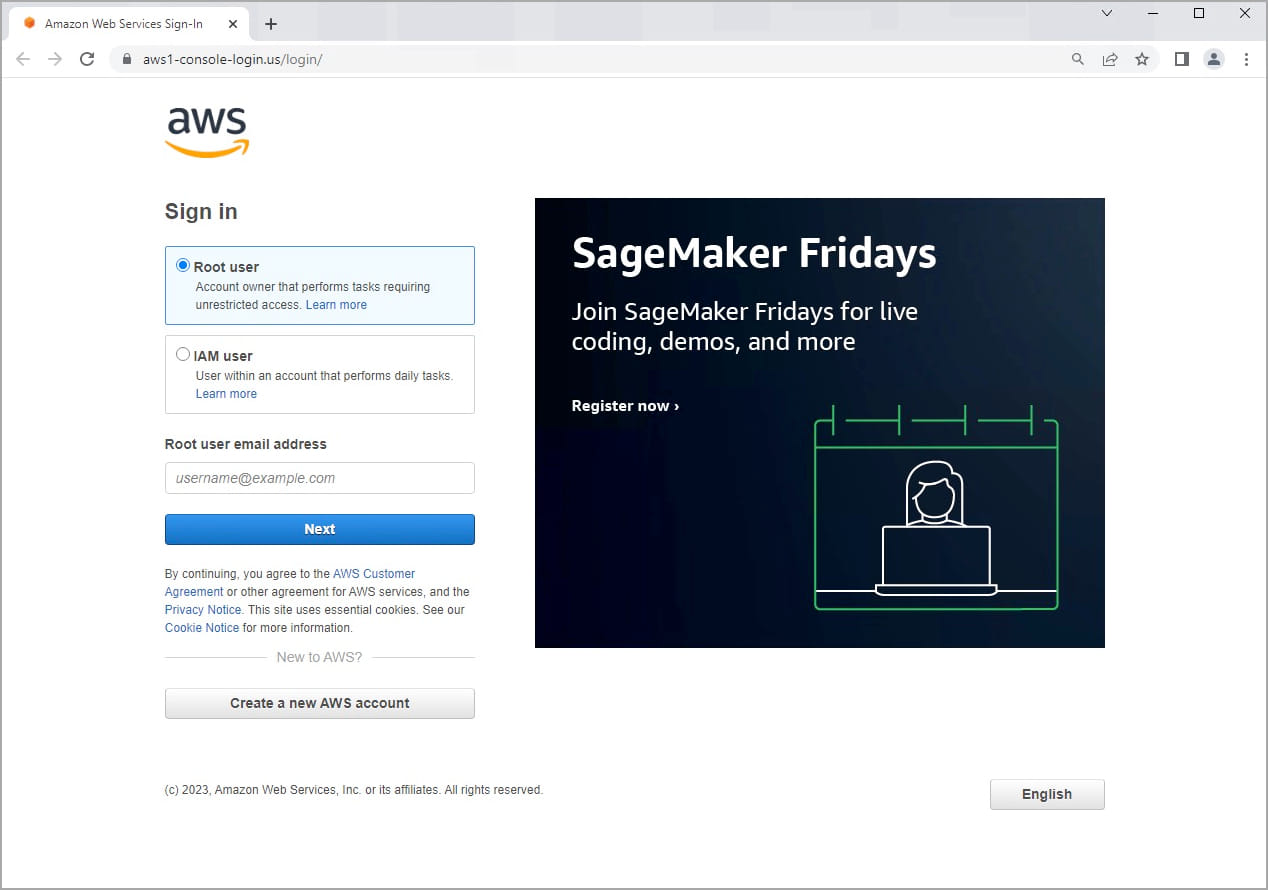
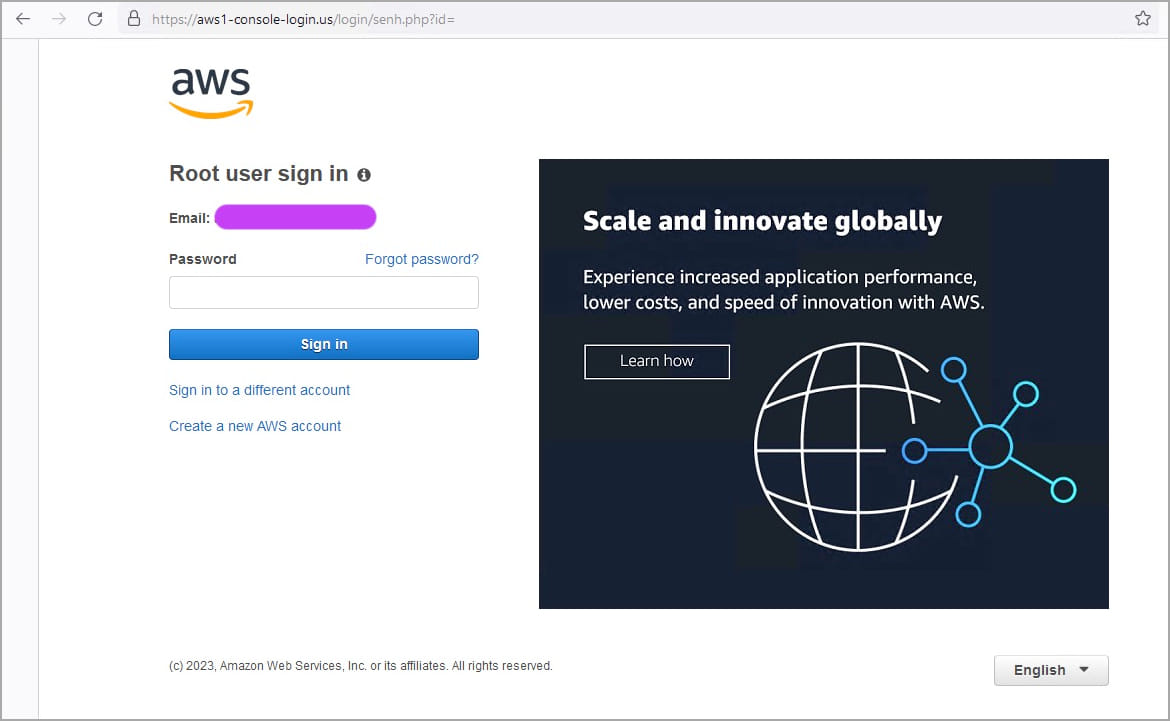
The phishing domains seen by Sentinel Labs are:
- aws1-console-login[.]us
- aws2-console-login[.]xyz
- aws1-ec2-console[.]com
- aws1-us-west[.]data
An attention-grabbing characteristic of the phishing pages is that their writer has included a JavaScript perform to disable proper clicks, center mouse buttons, or keyboard shortcuts.
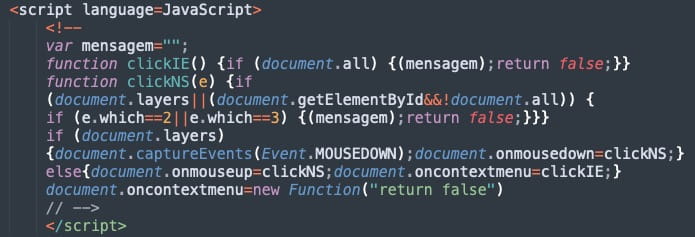
Sentinel Labs says that is seemingly a mechanism to forestall customers from navigating away from the web page, both purposefully or by mistake.
The safety agency studies seeing Portuguese used as a language within the JavaScript code feedback and variables, whereas the basis web page of the blogger area mimics a Brazilian dessert enterprise. Lastly, the Whois particulars used for registering the domains level to a Brazilian particular person.
Sentinel Labs reported the abuse to CloudFlare, which protected the phishing websites, and the web firm shortly shut down the account. Nonetheless, the malicious Google Advertisements stay, even when the websites they hyperlink to are not on-line.
Google Advertisements have been beneath huge abuse from cybercriminals of all types recently, serving in its place technique to succeed in potential victims.
These adverts have been used recently for phishing password supervisor accounts, reaching preliminary community compromise for ransomware deployment, and malware distribution masquerading reliable software program instruments.
Final week, Sentinel Labs found a marketing campaign that makes use of virtualization expertise along with Google Advertisements to unfold malware that makes it more durable to detect by antivirus instruments.
[ad_2]