[ad_1]

New ESXiArgs ransomware assaults at the moment are encrypting extra in depth quantities of knowledge, making it a lot more durable, if not inconceivable, to get better encrypted VMware ESXi digital machines.
Final Friday, an enormous and widespread automated ransomware assault encrypted over 3,000 Web-exposed VMware ESXi servers utilizing a brand new ESXiArgs ransomware.
Preliminary experiences indicated that the units had been breached utilizing previous VMware SLP vulnerabilities. Nonetheless, some victims have acknowledged that SLP was disabled on their units and had been nonetheless breached and encrypted.
When encrypting a tool, an ‘encrypt.sh’ script appears for digital machine recordsdata matching the next extensions:
.vmdk
.vmx
.vmxf
.vmsd
.vmsn
.vswp
.vmss
.nvram
.vmemFor every file that’s discovered, the script checks the file measurement, and if the file is smaller than 128 MB, encrypts the entire file in 1MB increments.
Nonetheless, for recordsdata bigger than 128 MB, it will compute a ‘size_step,’ which might trigger the encryptor to alternate between encrypting 1 MB of knowledge and never encrypting chunks (the size_step in megabytes) of knowledge.
The encrypt.sh script makes use of the next components (barely modified for readability) to find out what size_step ought to be used:
size_step=((($size_in_kb/1024/100)-1))This implies for a 4.5 GB file, it will generate a size_step of ’45,’ inflicting the encryptor to alternate between encrypting 1 MB of the file and skipping 45 MB of the file. So, as you’ll be able to see, fairly a bit of knowledge stays unencrypted by the point it is completed encrypting a file.
For even bigger recordsdata, like a 450GB file, the quantity of skipped knowledge rises dramatically, with the size_step changing into ‘4607,’ now alternating between encrypting 1MB and skipping 4.49 GB of knowledge.
Resulting from these giant chunks of unencrypted knowledge, researchers devised a technique to get better digital machines utilizing the big and primarily unencrypted flat recordsdata, the place the digital machine’s disk knowledge is saved.
A script created by CISA later automated this restoration course of.
Encryption course of modified
Sadly, a second ESXiArgs ransomware wave began at this time and features a modified encryption routine that encrypts way more knowledge in giant recordsdata.
BleepingComputer first realized of the second wave after an admin posted within the ESXiArgs help matter stating that their server was encrypted and couldn’t be recovered utilizing the strategies that had labored beforehand.
After sharing the samples with BleepingComputer, we seen that the encryptor had not modified, however the encrypt.sh script’s ‘size_step’ routine had been taken out and easily set to 1 within the new model.
This variation is illustrated under in a comparability between the unique encrypt.sh size_step computation (left) within the first wave of assaults, with the brand new shell script (proper) within the second wave.
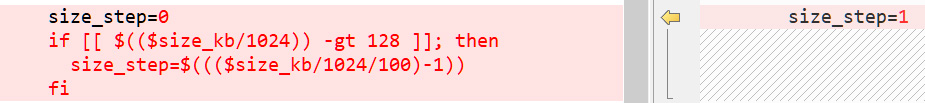
Supply: BleepingComputer
Ransomware skilled Michael Gillespie advised BleepingComputer that this transformation causes the encryptor to alternate between encrypting 1 MB of knowledge and skipping 1 MB of knowledge.
All recordsdata over 128 MB will now have 50% of their knowledge encrypted, making them probably unrecoverable.
This variation additionally prevents the earlier restoration instruments from efficiently recovering machines, because the flat recordsdata may have an excessive amount of knowledge encrypted to be usable.
This second wave of assault additionally made a minor change to the ransom be aware by not together with bitcoin addresses within the ransom be aware, as proven under.
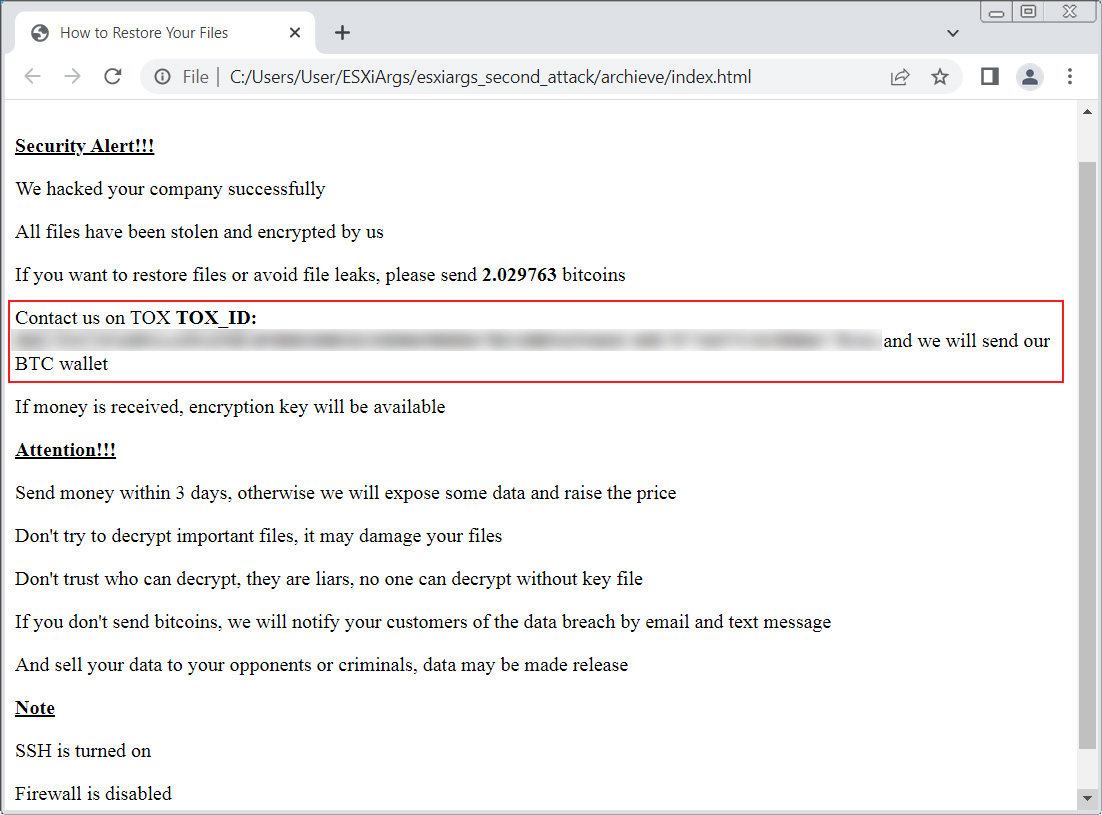
Supply: BleepingComputer
The elimination of the bitcoin addresses was probably because of them being collected by safety researchers to trace ransom funds.
Nonetheless, much more regarding, the admin who shared the brand new samples stated they’d SLP disabled on their server however had been nonetheless breached once more. Additionally they checked for the vmtool.py backdoor seen in earlier assaults, and it was not discovered.
With SLP disabled, it turns into much more complicated as to how this server was breached.
BleepingComputer nonetheless recommends making an attempt to get better encrypted ESXi servers utilizing CISA’s restoration script.
Nonetheless, it should probably not work in the event you had been contaminated within the second wave of assaults utilizing the brand new encryption routine.
When you’ve got any questions or want help on the ESXiArgs ransomware, we’ve got a devoted help matter in our boards.
[ad_2]